Trojanized Discord Client Grabs Passwords and User Tokens
- Actors are stealing people’s accounts on Discord by pushing modifying trojans into them.
- The attackers are taking over the accounts and then dispense the malware to the victim’s friends.
- Deleting and reinstalling the client from the official source should fix the infection problem.
The “MalwareHunter” research team has discovered a malicious process that turns the Discord chat app client into a password stealer. The threat actor who is engaging in this campaign is deploying a custom spin of the “AnarchyGrabber” Trojan, which is capable of stealing passwords, disabling two-factor authentication, and even spreading over the victim’s friends on Discord. The crooks are distributing the trojan by pushing it as a game cheat or pirated software that would normally cost a lot to purchase. This is the mechanism for convincing the victims, as the involvement of the target is an absolute requirement for planting “AnarchyGrabber.”
The malware is turning the Discord client into a dangerous piece of software by modifying its regular JavaScript files. The actor has created a custom variant of “AnarchyGrabber,” putting a “3” in the version number to denote its upgraded nature. When the infected Discord client launches, it loads “inject.js” from a folder named “4n4rchy” - which, in turn, loads “discordmod.js” into the client itself. The filenames are giving away the role of these JavaScript snippets, but the victims are unlikely to check these manually anyway.
Source: Bleeping Computer
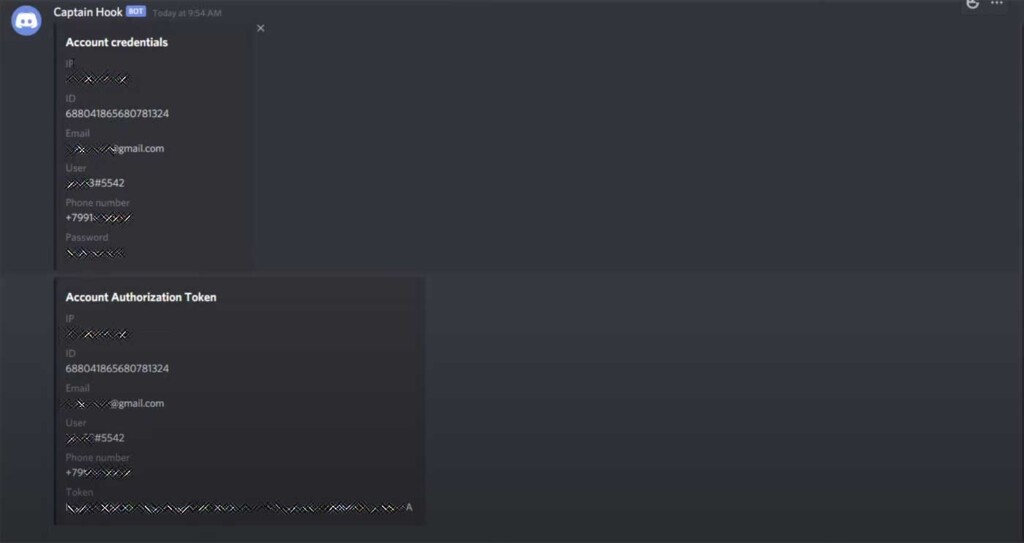
The malware will automatically log the users out and then prompt them to re-login. Once they do, the trojan disables 2FA on their account and exfiltrates the credentials in plain text form, the user token, and their IP address. From there, the attacker may use these to log in as the victim, and then spread the malware over to the user’s friends - who would be more open to trusting a message that comes from their contacts. All of this is done once, so after stealing the credentials, the malware goes dormant. However, the infected Discord client continues to remain part of the botnet.
Source: Bleeping Computer
To check if your Discord client has been infected by “AnarchyGrabber3,” open ’%AppData%\Discord\[version]\modules\discord_desktop_core\index.js’ using your Notepad app, and check the contents. Normally, you should only get a single line that contains the following:
‘module.exports = require('./core.asar');’
If there’s anything else there that you haven’t manually added yourself, then your Discord client has most probably been infected by malware. To fix this issue, simply uninstall it and then install it again by fetching the latest version from the official Discord website. Finally, check the aforementioned “index.js” file again to make sure that you’re using a clear version.