TP-Link Archer C5 Routers Vulnerable to Remote Takeover
- IBM researchers discover a zero-day critical flaw that concerns various TP-Link routers.
- An attacker could spoof the victim’s IP address and send an invalid request to the device, triggering the wiping of the admin password.
- Users are urged to apply the fixing patches that were released by TP-Link immediately.
As discovered by IBM’s X-Force Red researcher Grzegorz Wypych, all TP-Link Archer C5 v4 routers running the firmware version 3.16.0 0.9.1 v600c.0 Build 180124 Rel.28919n are vulnerable to “CVE-2017-7405”. This flaw enables an attacker to take over the device remotely by spoofing the IP address which belongs to the victim’s host, gaining administrative rights without having to enter any authentication credentials. The attacker may then sniff the network traffic of the victim, change the router settings, and lock the real owner out.
Archer C5 routers are extremely popular devices, so this zero-day flaw affects millions of users. Besides the C5 though, the Archer MR200 v4, MR400 v3, and MR6400 v4 were also confirmed to be affected by the same flaw, so all of them need to be patched immediately. TP-Link has already released the fixing updates, so the owners of these devices are urged to apply them as soon as possible. For additional security, users are advised to activate the two-factor authentication step on their router administration platform so as to minimize the chances of being compromised.
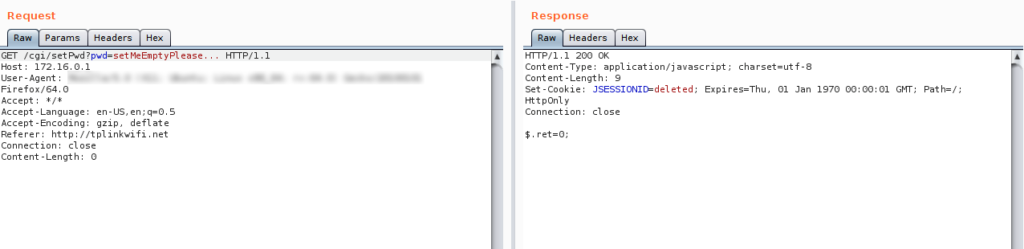
As the researcher points out, the risk of this vulnerability is greater in corporate environments as the attacker would enable guest Wi-Fi, engage in lateral movement, and set up an insecure FTP on WAN configuration. This flaw isn’t just opening the door to the attacker, but can also lock the legitimate user out of the router since the original passwords can be changed without any warnings or notifications. According to the few technical details that were provided right now, the issue concerns a password overflow bug. More specifically, if the attacker sends a string that is too long for the device, the router wipes the saved password and replaces it with an empty value. Since the only user in these devices is the admin, this simple method results in the complete takeover of the router.
Source: securityintelligence.com
Source: securityintelligence.com
According to current statistics, only one out of six consumers are keeping their routers up to date by applying the available vendor patches that plug any severe security holes like the one presented here. For home users out there, the consequences could also involve private life exposure, as these routers often handle the feed of smart IoT devices like webcams, baby monitors, smart speakers, and more. That said, remember that it’s better to set up a separate network for these devices in your house.
Are you using an Archer C5, and when was the last time you applied a security patch? Let us know in the comments down below, or on our socials, on Facebook and Twitter.