‘ToxicEye’ Is the Latest Malware to Abuse Telegram for Command & Control
- Users of the ‘ToxicEye’ RAT are abusing the Telegram platform to engage in malicious operations.
- The particular malware is capable of data exfiltration, deletion, or even ransomware-backing encryption.
- The abuse of legitimate services like Telegram is growing, and there seem to be very few ways to stop it.
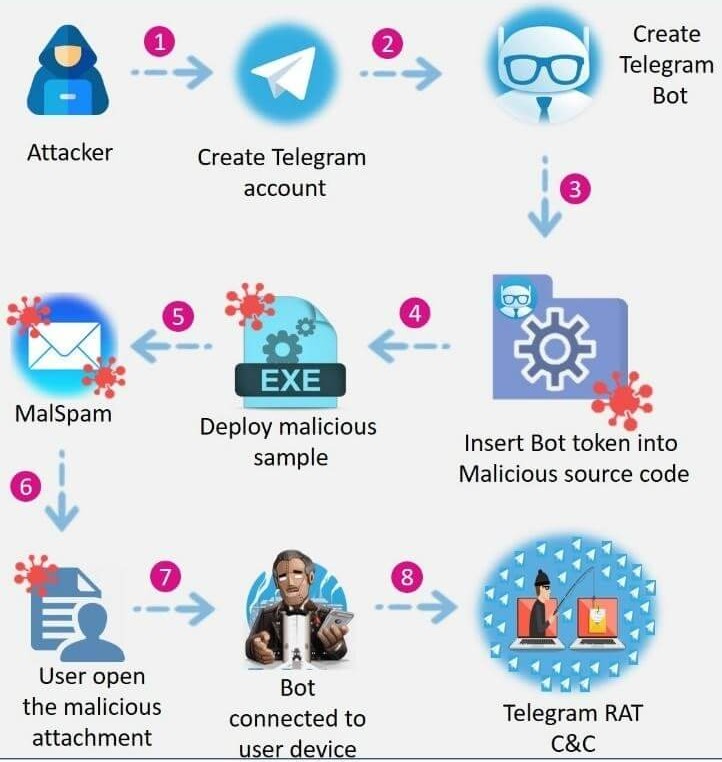
There’s a rising trend of malware authors abusing Telegram for their malicious operations, using it as a ready-made command and control (C&C) system. The latest notable entry in this category is a remote access trojan named ‘ToxicEye’, which has been spotted, sampled, analyzed, and detailed in a write-up by Check Point.
The benefits of using Telegram as C&C can be analyzed in the following:
- Telegram is a legitimate service, and as such, it can help malware authors evade AV detection.
- Telegram is a big and reliable service, offering a stable and “always-online” infrastructure.
- Telegram can be used for data exfiltration or payload fetching and planting.
- The platform requires no ID verification upon registration, so crooks can simply use an anonymous phone number.
- The attackers can use Telegram to access infected computers right from their mobile devices.
‘ToxicEye’ is notable because it is one of the nastiest pieces of RATs that are circulating out there. Check Point has seen it in over 130 attacks, spreading via phishing emails that come with a .exe file as an attachment. Users who are convinced to download and execute the binary are infected and then run the following risks:
- Having their data exfiltrated
- Having their files deleted
- Having running processes killed
- Having their microphone or camera hijacked
- Having their files encrypted
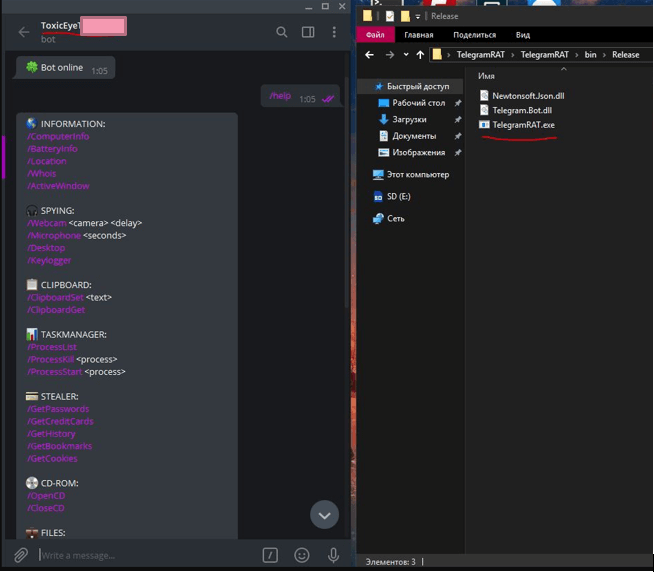
ToxicEye can steal the data, including browser history and cookies, PC information, or credentials and passwords. The RAT can also deploy a keylogger, monitor and exfiltrate clipboard data, and support ransomware operation with both encryption and decryption features built-in.
To protect yourself against dangers of this kind, you should first and foremost avoid downloading any attachments that have arrived via unsolicited emails. No matter what these messages claim, or what emergencies are presented, you should always treat them with caution.
If you suspect that you may already be in trouble, search for the following file on your computer ‘C:\Users\ToxicEye\rat.exe’. Additionally, you could scrutinize your organization's network traffic to see if any of your systems communicate with Telegram, even though the IM software isn’t installed on them.
Only yesterday, we analyzed how malware authors are increasingly turning to the abuse of legitimate services and cloud platforms, and why stopping it is both difficult and complicated. The ToxicEye RAT is yet another example of that, and one that’s added on top of a rapidly growing pile.