TouchID Flaw Could Open the Way to iCloud Account Hijacking
- A flaw in TouchID and Apple’s online authentication could have enabled hackers to access iCloud data.
- The vulnerability was easy to fix, but it was tricky to miss during the testing phase, nonetheless.
- Apple fixed the vulnerability on the same day is was reported to them, applying a fix on the server-side.
The TouchID is one of Apple’s user authentication systems, with the other being the FaceID. However, in the days of COVID-19 that have people wearing masks and hiding their faces, the TouchID has grown more popular and widely used.
As a security researcher of Computest warns, TouchID had a serious security issue that could have enabled an attacker to hijack the user’s iCloud account. When he reported the discovered vulnerability to Apple, the tech company was very quick to fix it by applying a patch on the server-side.
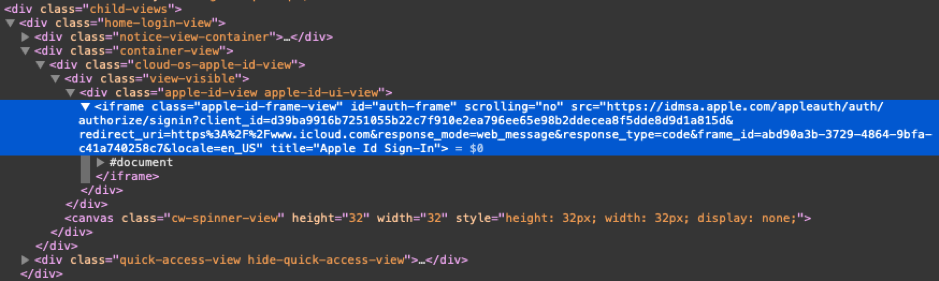
The exploit process can begin on any website that requires Apple ID to sign in. This essentially bypasses 2FA since the TouchID is also considered multi-factor authentication. Due to a lack of checking whether or not the redirect URI matches the client ID, an attacker could potentially trigger a cross-site scripting vulnerability on an Apple subdomain and run a malicious JavaScript snippet to steal the authentication token.
That would open a valid icloud.com session for the attacker, but the potential for exploitation doesn’t end there.
If the attacker embeds malicious JavaScript on a web page that pops up when connecting to a Wi-Fi network for the first time, they could serve the victim with a TouchID prompt and steal their tokens. The implications of this would be the compromise of personal data by accessing several iCloud accounts.
The setting for such an attack could be a hotel, airport, or a cafe network. Obviously, the attacker wouldn’t have to compromise the actual network for this purpose, but merely set up a fake hotspot and give it a convincing name.
As the researcher comments, the vulnerability was simple in type and quite easy to fix entirely on the server-side. The reason why Apple’s engineers missed it in the first place could be because testers naturally focused on using untrusted domains for the redirection, but the trick only works for Apple subdomains.
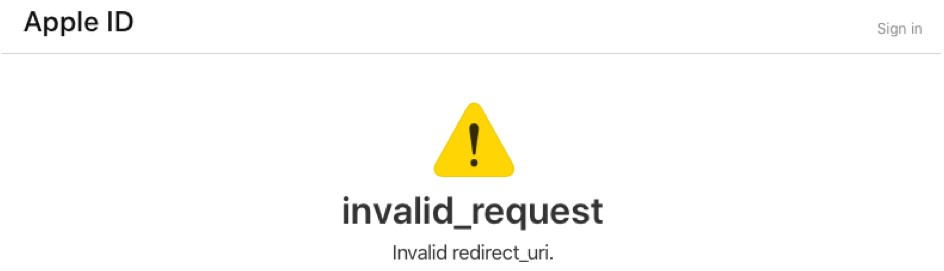
The man confirmed that anything ending with “apple.com,” “icloud.com,” and “icloud.com.cn” would work perfectly. Now, the authentication server validates the redirect URI correctly, so if you try to draw the token to a malicious webpage, you’ll get an “invalid request” error.
Source: Computest
This means that as a user, there’s nothing that you need to do right now. Apple has fixed the problem, and so you are safe to use TouchID for authentication.
In general, when trying to access the net via a public Wi-Fi, you should be using a VPN tool at all times, opt for 2FA, and only connect when it’s really necessary. As for the possibility of this bug having been exploited in the wild, no comments on this have been made, but it’s quite likely.