Top Threats in 2025: Cl0p Ransomware, Lumma Stealer, and Several Flaw Exploits
- Infostealer activity: Lumma, Redline, and Raccoon2 were responsible for most of the global infections.
- Top ransomware: Cl0p, Akira, and Qilin remain the three most prevalent ransomware cases this year.
- Vulnerability exploits: Microsoft and Ivanti were among the most abused 2025 flaws in the cybercriminal world.
Kela’s 2025 Midyear Threat Report has shed light on the growing influence of top ransomware gangs, flaw exploits, and infostealers. The rise of multi-extortion tactics and the proliferation of advanced malware strains demonstrate the adaptability and persistence of cybercriminals in the current threat landscape.
Leading Ransomware Gangs
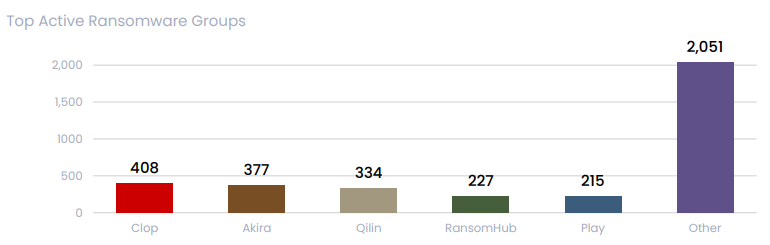
The Cl0p ransomware group emerged as the most active threat actor in the first half of 2025, claiming over 408 victims globally. Notably, their exploitation of Cleo software vulnerabilities showcased the increasing reliance on supply chain attacks to maximize disruption.
Other significant actors included the Akira group, witnessing a 202% surge in activity compared to the previous year, and Qilin, responsible for the high-profile breach of Lee Enterprises.
RansomHub and Play Ransomware occupied the last two spots in this top five, while over 2,000 cases were attributed to around 90 other actors. In March, RansomHub was linked to the Play, Medusa, and BianLian ransomware groups via Shared EDRKillShifter Use.
These groups are focusing on supply chain attacks and shifting to data theft.
Dominant Infostealer Strains
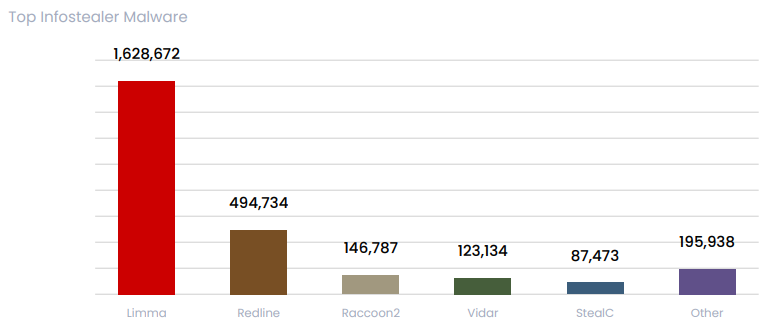
Similar to ransomware, infostealers played a critical role in enabling advanced cyberattacks. Lumma led the malware landscape by far, and combined with Redline and Raccoon2, accounted for 85% of infections globally. Vidar and StealC were also in the top five.
The report mentions a drop in infected bots per month that coincided with the takedown of LummaC2 in May 2025. Yet, a few days later, Lumma operators returned access to the servers that law enforcement had formatted twice.
In July, Hudson Rock linked over 30,000 Lumma, StealC, Vidar, Raccoon, and RedLine infections to the FMovies pirate website.
These infostealers targeted both macOS and Windows systems, indicating a shift toward cross-platform capabilities. Known for stealthily collecting credentials, they served as a precursor to ransomware deployments and espionage activities.
Key victims included major ISPs and multinational corporations, where attackers leveraged stolen credentials to compromise sensitive systems. Kela notes that more than 1.3 billion credentials, apparently sourced from infostealer logs, were shared via credential lists.
Top Exploited Vulnerabilities
Among the most exploited vulnerabilities in the first half of 2025 were CVE-2025-0282 (Ivanti Connect Secure) and CVE-2025-26633 (Microsoft Management Console).
Kela’s report mentions observing dark web chats predominantly on:
- CVE-2025-49113 (Roundcube)
- CVE-2025-32433 (Erlang/OTP SSH server used in Cisco platforms)
- Microsoft’s CVE-2025-24071 and CVE-2025-26633
- CVE-2025-0108 (Palo Alto Networks)
Trends in Cybercrime
Throughout 2025, ransomware and infostealers demonstrated increased operational sophistication, blending tactics like credential harvesting, data theft, and extortion. Kela predicts infostealers will continue to be the top initial access vector in the form of MaaS (Malware-as-a-Service).