Tomiris APT Targets Diplomatic Entities in New Campaign Using Multi-Language Reverse Shells, Havoc and AdaptixC2 Open-Source Frameworks
Key Takeaways
- Target profile: Tomiris APT is targeting foreign ministries and intergovernmental and government entities, focusing on Russian speakers and Central Asian countries.
- Novel C2 tactics: Attackers are increasingly using public services like Telegram and Discord for command-and-control (C2) communications to evade detection.
- Malware deployed: The campaign uses reverse shell tools in various languages and deploys open-source post-exploitation frameworks like Havoc and AdaptixC2.
Security researchers have identified a new wave of malicious operations by the Tomiris APT (Storm-0473) group, which began in early 2025. These sophisticated attacks are directed at high-value political and diplomatic targets, including foreign ministries and intergovernmental organizations.
The group shows a particular focus on Russian-speaking users or entities in Central Asian countries like Turkmenistan, Kyrgyzstan, Tajikistan, and Uzbekistan.
Use of Telegram and Discord for Command-and-Control
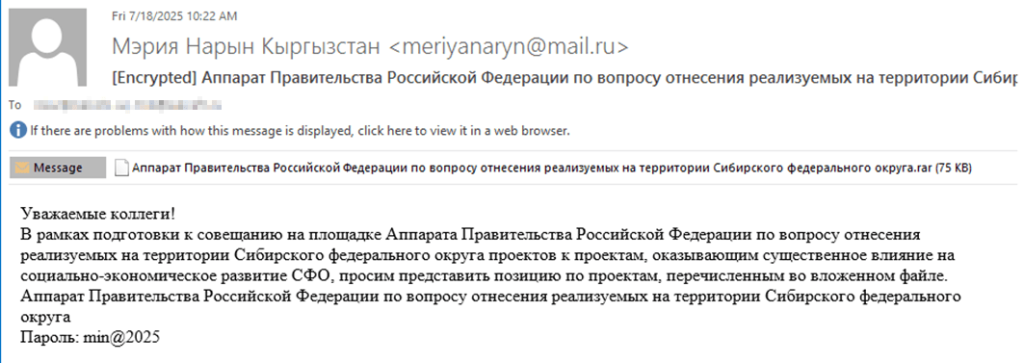
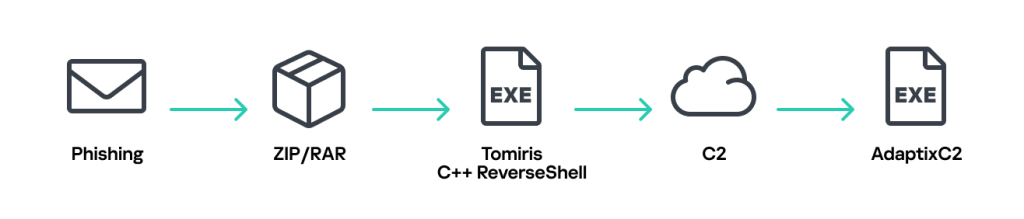
The campaign primarily initiates infection through phishing emails containing password-protected archives, according to new research from Kaspersky’s SecureList. These archives hold executables disguised as office documents, which, when run, infect the target system.
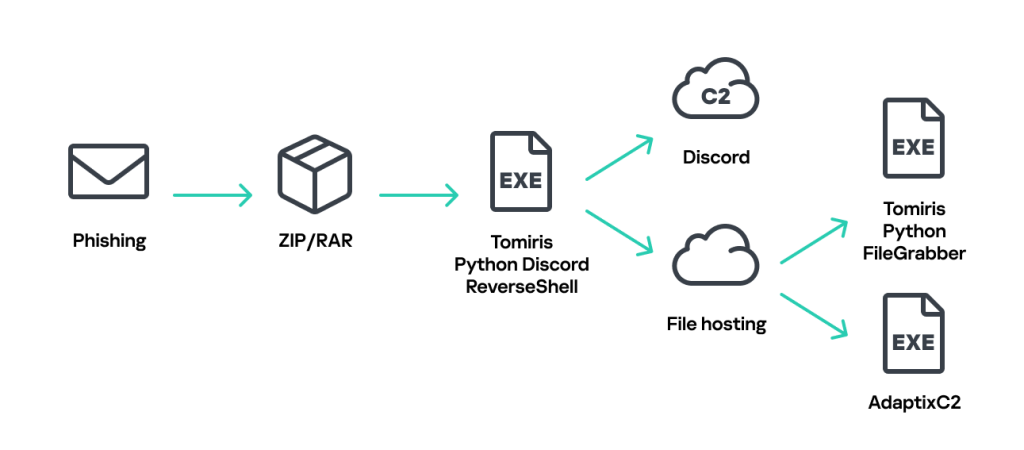
A notable evolution in the group's tactics is the increased use of implants that leverage public services for C2. The campaign employs Telegram C2 malware and Discord-based reverse shells to blend their malicious traffic with legitimate network activity, making detection by security solutions more challenging.
These implants, written in languages such as Go, Rust, and Python, are used for initial reconnaissance and to download subsequent payloads. In one observed case, a Python-based Trojan used the Discord API to act as a reverse shell, executing commands and exfiltrating data.
The identified ones are:
- Tomiris C/C++ ReverseShell
- Tomiris Rust Downloader
- Tomiris Python Discord ReverseShell
- Tomiris Python FileGrabber
- Distopia backdoor
- Tomiris Python Telegram ReverseShell
- Tomiris C# Telegram ReverseShell
- JLORAT
- Tomiris Rust ReverseShell
- Tomiris Go ReverseShell
- Tomiris PowerShell Telegram Backdoor
- Tomiris C# ReverseShell
- Tomiris C++ ReverseSocks (based on GitHub Neosama/Reverse-SOCKS5)
- Tomiris Go ReverseSocks (based on GitHub Acebond/ReverseSocks5)
Post-Exploitation Frameworks and Attribution
Following initial access, the Tomiris cyberattacks in 2025 often involve deploying open-source post-exploitation frameworks, including Havoc and AdaptixC2. These tools give attackers advanced capabilities for lateral movement and data exfiltration within the compromised network.
Attribution to the Tomiris APT group is based on overlapping tactics, techniques, and procedures (TTPs) from previous campaigns, such as the use of specific file-naming conventions and password-protected archives.
The deployment of different malware types under the same filenames further strengthens the connection to this specific Russian-speaking threat actor.
Last month, the Adaptix framework was exploited by cybercriminals with Russian ties, including Akira.
In other recent news, the Russia-aligned RomCom gang was seen using SocGholish to deploy Mythic Agent on Ukraine supporters in a new campaign linked to GRU Unit 29155.