The “TikTok Pro” App Is Essentially Spyware Under Disguise
- A spyware app presenting itself as “TikTok Pro” is actually a powerful spyware that can steal various types of user data.
- The malware’s functionality covers a lot from call logs to SMS content, and from capturing screenshots to launching FB phishing pages
- People’s uncertainty and app bans lead to users looking for the APK on unofficial sources, and this is an opportunity for crooks.
There’s a new spyware app out there targeting Android users and pretending to be the “Pro” version of the extremely popular TikTok app. Named “TikTok Pro,” the app is looking to cash in people’s fear on the regular TikTok, as there’s an overwhelming amount of negative publicity that targeted that application during the last couple of months.
Also, there’s a ban of the app on several countries, and Trump’s order to American companies to acquire TikTok by September 15, or it will be blocked from the US app market. All this creates a situation where people may falsely think that the “Pro” version, even though it’s still offered free of charge, will respect its users’ privacy and not log sensitive data about them.
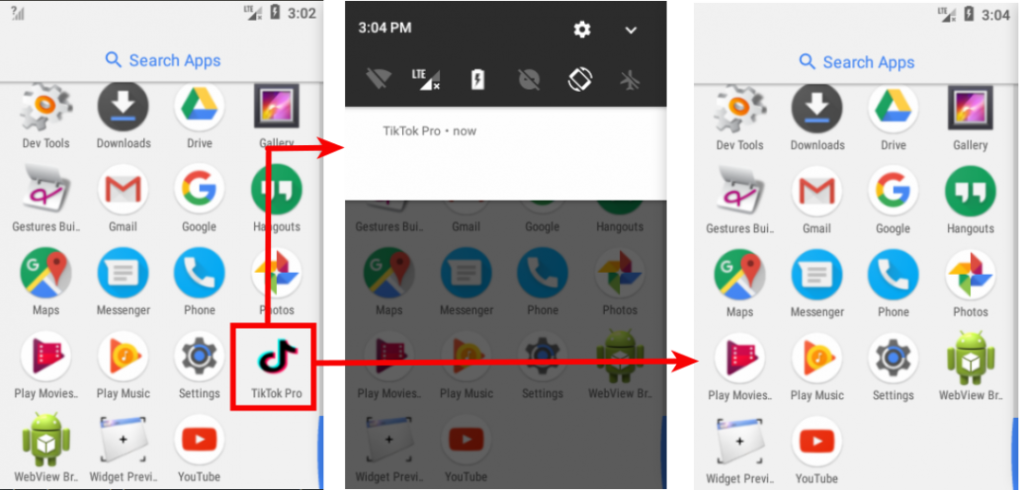
The spyware app uses the TikTok icon on the app drawer, starting its trickery with a dose of familiarity. Upon launching it, the icon hides, and a notification is displayed to shift the user’s attention elsewhere. Under the hood, the spyware initiates an Android service named “MainService”, which is the core of the malware.
MainService enables the malware to do the following:
- Steal SMS messages
- Send SMS messages
- Steal the victim’s location
- Capture photos
- Execute commands
- Capture screenshots
- Call phone numbers
- Initiate other apps
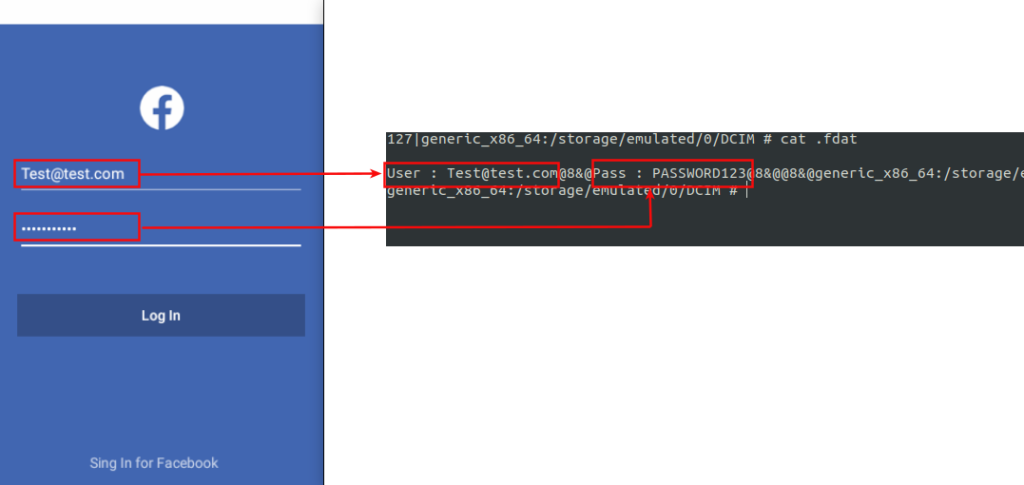
- Steal Facebook credentials
The stolen data is stored on the external storage and in a hidden sub-directory named “.dat”. Call details, for example, are stored in .mp3 format in the SD card, and from there, they are exfiltrated to the C2 server upon command.
Source: Zscaler
In the meantime, and because the app icon has been hidden, the user is likely to believe that the app was faulty, crashed upon launch, and removed itself.
Source: Zscaler
The C&C can pass a wide array of commands to the spyware, including one that fetches the latitude and longitude of the infected device, one that launches Facebook, another one that launches a fake Facebook login page, one that plays a ringtone, and many more.
The Facebook page is obviously there to steal user credentials, which are again stored in the SD card in ZIP form.
Source: Zscaler
Banning TikTok from the Google Play Store forces users to look elsewhere for the “precious” APK, but you should never trust external app sources. Crooks are always on the lookout for opportunities that arise, and the volatile situation with the real TikTok is creating a first-class opportunity.