Three New Ransomware Decryptors Are Up for Grabs
- Kaspersky managed to unlock FortuneCrypt and Yatron, adding two new decryptors on their RakhniDecryptor tool.
- Emsisoft has released a free decryptor for the WannaCryFake ransomware.
- The best way to stay unaffected by ransomware is to take regular backups and keep them offline.
Not all cybersecurity news is bad news. Every once in awhile we are in the happy position to inform you of the release of a ransomware decryptor. Some concern niche malware, while others may be vastly popular tools that have caused a great disturbance in the IT world. This time, the good news comes from Kaspersky and Emsisoft, who have released three decryptors for Yatron, FortuneCrypt, and the WannaCryFake ransomware variants. If you were hit by one of these three and you've waited patiently until something that will help you unlock your files pops up, you have just been vindicated.
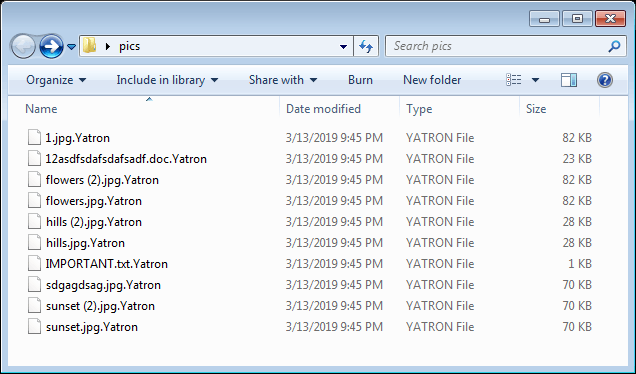
Kaspersky has added the decryptors for Yatron and FortuneCrypt on its “RakhniDecryptor” tool, which is their Omni-solution, offered free of any charge. Yatron is based on Hidden Tear, the popular open-source ransomware, and has mostly targeted people in Germany, China, Russia, India, and Myanmar. Kaspersky managed to exploit mistakes in the cryptographic scheme, attributed to careless copying of Hidden Tear code which carried specific vulnerabilities.
Source: securelist.com
The FortuneCrypt ransomware is much more popular, affecting many thousands of users in Russia, Brazil, Germany, South Korea, and Iran. This is one of the rare tools that don’t add a characteristic file extension at the end of the encrypted files but instead adds a text string to the beginning of the filenames. The particular ransomware is written in Blitz, a programming language that is meant to be used in game development. Kaspersky broke this malware by finding a vulnerability in its cryptographic scheme, characterizing the recovery of the encrypted files “easy”.
Source: securelist.com
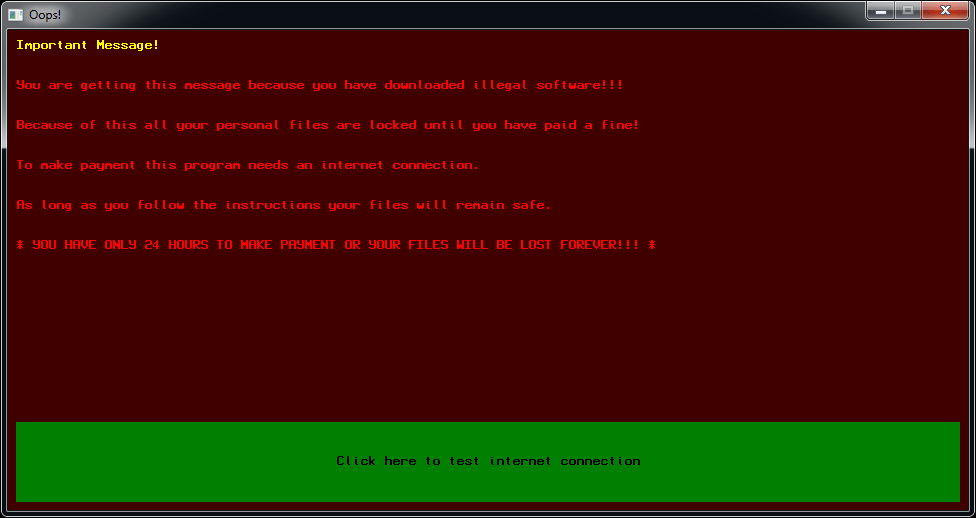
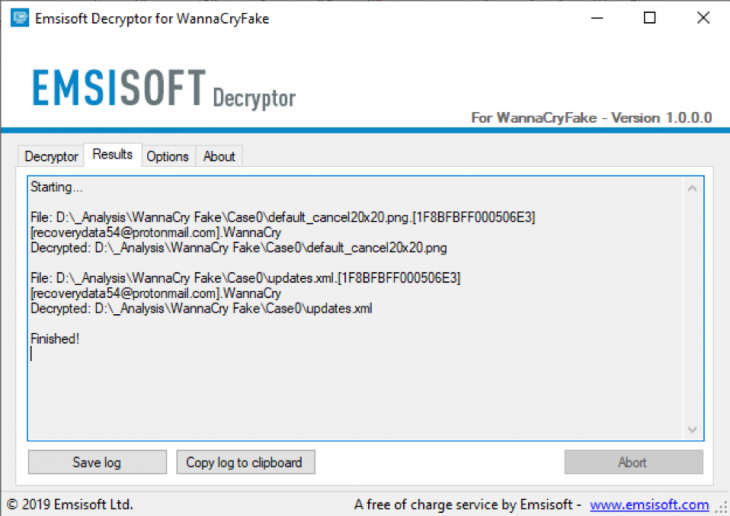
Finally, Emsisoft, a company that is devoted to the fight against ransomware has released yet another free decryptor, and this one is for the WannaCryFake strain. This malware uses AES-256 to encrypt the user’s files, and the resulting files carry the “WannaCry” extension. The actors are claiming to provide a versatile payment plan for the victims, promising lower costs for those who contact them immediately after getting infected. Of course, paying ransomware actors is never the right thing to do, as there’s no guarantee that you’ll get a decryptor or key for your money.
Source: blog.emsisoft.com
If you want to stay safe against this type of attacks, and if you don’t want to wait for a decryptor to be released in the future, there’s one simple thing that you can do. Take regular backups and store them on offline media like an external hard drive. If you have been infected by ransomware, do not try to plug the disk that contains your backup before you’re confident that your system has been 100% cleaned, otherwise you may lose everything.
Have you fallen victim of one of the above ransomware strains? Let us know of the details in the comments down below, or on our socials, on Facebook and Twitter.