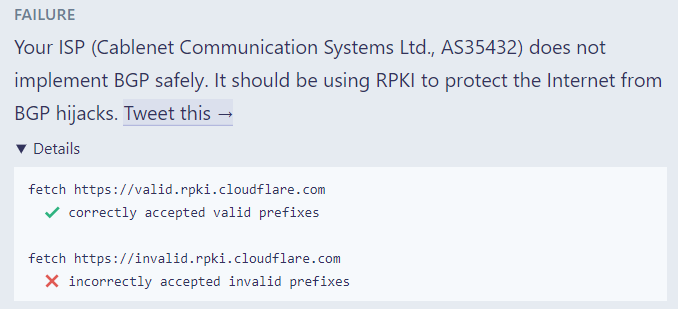
Test Your ISP to Find Out if it’s BGP Protected or Not
- If your internet service provider is not using any protection against BGP hijacking, you could get phished.
- ISPs haven’t responded to this risk with the appropriate urgency, so the situation remains bad.
- Customers should begin exerting pressure onto their ISPs, requesting the deployment of RPKI.
Knowing whether or not your ISP (Internet Service Provider) is protected against BGP (Border Gateway Protocol) hijacks or not is important for determining the risk that you’re running. By identifying the risks, internet users can take protective action or simply apply pressure on their providers to adopt safer technologies. To test your ISP, visit “isbgpsafeyet.com” and press the “Test you ISP” button. The service will announce a legitimate route via an invalid announcement and will check if your ISP accepts it or not.
BGP is unsafe by design, and it does not incorporate any security protocols. For this reason, some service providers implement filtering systems to stop BGP hijacks and traffic leaks, but not every system of this kind is absolutely effective, and nor everyone cares to implement them. We have seen BGP hijacking incidents before, with Google Services going down due to it in November 2018, China Telecom scrambling European internet traffic in June 2019, and Cloudflare having 15% of its global traffic rerouted onto the wrong places in June 2019 again. So, BGP hijacking isn’t something that we’re merely discussing in theory, but a tangible problem that is already affecting the global internet.
Source: isbgpsafeyet.com
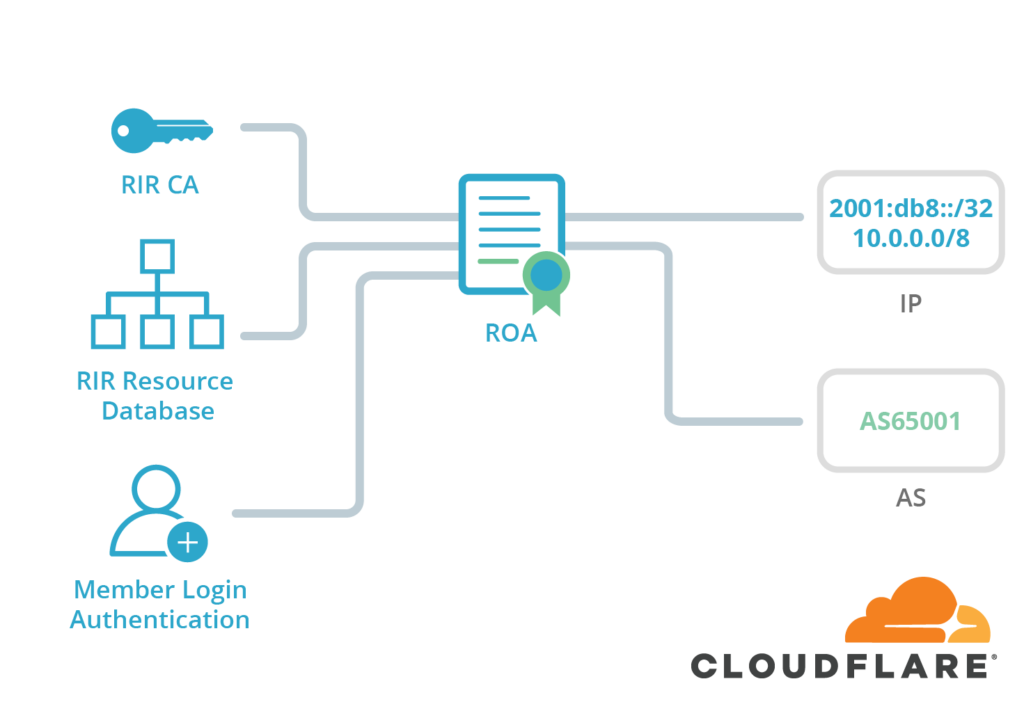
To put it simply, BGP hijacking is the purposeful redirection of network traffic to lead users to a malicious website that is made to look like the corresponding legitimate one. The purpose of this is phishing or information stealing. So, if your ISP doesn’t support a safe routing protocol, you are running the risk of visiting spoofed websites and getting phished. Sometimes, this happens by mistake or a misconfiguration, but it remains dangerous nonetheless. A system that was created specifically to address this security problem is the RPKI (Resource Public Key Infrastructure), which associates an announced route with an autonomous validation system by using cryptography. RPKI was introduced back in September 2018, but unfortunately, a tiny number of ISPs have already adopted the technology.
Source: Cloudflare
All that said, taking the test to figure out the state of BGP security on your ISP is meant to serve as a lever of pressure to compel the provider to adopt more secure technologies. You should tweet the results, ask your ISP to provide a (public) response, urge others to do the same, and try to raise awareness about the risks that stem from BGP hijacking. Moreover, you may contact your ISPs directly and ask them to deploy RPKI. The more ISPs do that, the safer the internet will become for everyone.