Targeting Customer Support: After Air France and KLM Confirm Supply Chain Attack, Dark Web Vendor ‘Chucky_BF’ Puts Airline CRM Data for Sale
- Threat Platform Update: Chucky_BF, a dark web seller, is claiming to offer KLM loyalty CRM data for sale.
- Background Data: Air France and KLM disclosed a vendor breach earlier this week.
- Possible Connections: Whether the CRM data for sale and the third-party customer service breach involve the same incident remains unverified.
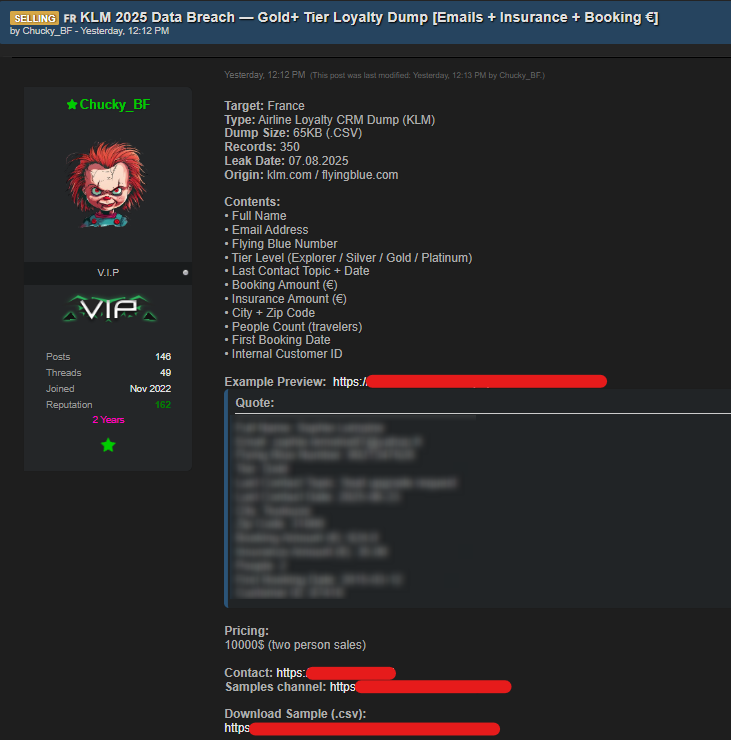
A cybercrime vendor, Chucky_BF, announced possessing data from KLM’s loyalty CRM, a customer relationship management system for its Flying Blue frequent flyer program, and has put up samples as proof on the dark web.
The update follows Air France’s recent official confirmation of a vendor breach.
CTI on the Sale of KLM Airline Loyalty Data
The threat actor says the dataset contains 350 records with passenger names, contact details, Flying Blue numbers and statuses, booking and insurance amounts, and other loyalty program information.
The post mentioned France as the target, and ‘Airline Loyalty CRM Dump (KLM)’ as the data type. They placed a sample of the stolen data as proof of the hacking and have put the impacted individuals' data on sale for $10,000 for two persons' records.
KLM and Air France’s Public Disclosure
“A few days ago, KLM and Air France disclosed a data breach stemming from a customer service provider, stating that the compromised data appeared to be limited to travelers who previously contacted customer service….,” read a HackManac post on X.
The breach affected travelers' data related to customer service, which typically includes names, phone numbers, email addresses, support tickets, and more.
KLM and Air France
KLM Royal Dutch Airlines is the national airline of the Netherlands. It merged with Air France in 2004 to form the Air France-KLM Group. Air France is France’s flag carrier airline, providing international and domestic services.
Based on the airlines’ statements, the third-party provider handles customer service interactions, which could include contact information and loyalty program account lookups. The cybersecurity incident did not directly impact KLM or Air France’s systems.
The likelihood of human error could not be ruled out in this incident. It is possible that the KLM loyalty CRM breach resulted from a social engineering attack in which threat actors posed as staff or vendors, sounded urgent, or claimed to be in an emergency to pressure help desk personnel into disclosing credentials or granting access.
After all, with all the security measures in place, threat actors now have to maintain stealth, which is possible when they are using legitimate access and account credentials.
The FBI in June warned that the cybercriminal group Scattered Spider is expanding into the aviation sector with social engineering schemes. They may impersonate airline staff, contractors, or vendors to trick IT help desks into granting access.
The KLM CRM breach also targets customer support, raising the question of a possible connection. Threat actors may seek travelers’ data for identity theft, financial fraud, or surveillance, motives that could even align with deportation intelligence gathering.