SVG Smuggling Attacks Elevate Phishing Campaign Techniques, Embedding Malicious JavaScript Code
- Phishing campaigns are leveraging a sophisticated method called SVG smuggling.
- Attackers exploit SVGs by disguising malicious JavaScript code as part of the graphic's structure.
- This approach helps cybercriminals circumvent traditional security measures.
Attackers embed malicious JavaScript directly into Scalable Vector Graphics (SVG) files to exploit the trust placed in this widely used image format, deploying browser redirects and launching phishing attacks.
This innovative technique has significant implications for cybersecurity, as it enables attackers to bypass detection systems and execute highly targeted campaigns, according to the most recent Ontinue security report.
SVG files, typically considered harmless visual assets, can contain embedded JavaScript code within <script><![CDATA[...]]></script> tags. Attackers exploit this capability by disguising malicious scripts as part of the graphic's structure.
In a typical SVG smuggling attack, the embedded script includes obfuscated code designed to evade detection.
Upon execution, the code uses browser-native functionalities to decode and redirect the victim to a malicious URL. These URLs often include Base64-encoded strings, enabling attackers to track victims or tailor subsequent payloads.
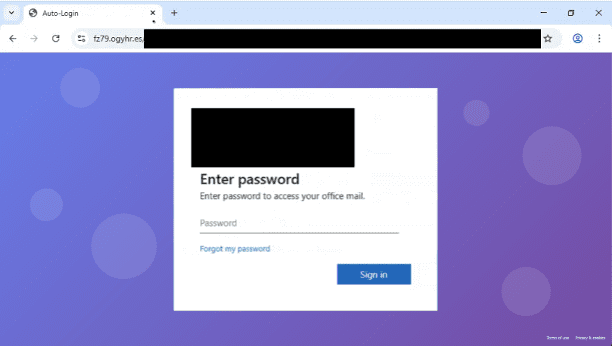
The phishing campaigns employing SVG smuggling are meticulously crafted. Attackers distribute the malicious SVG files through spoofed email attachments or links to externally hosted images.
Emails often leverage weakly secured domains (lacking SPF, DKIM, and DMARC records) to impersonate trusted brands or individuals effectively.
The minimalist presentation of these messages, paired with lookalike domains and cleverly engineered subject lines, reduces suspicion. Once recipients open the SVG file in a browser, the embedded script executes silently, redirecting them to attacker-controlled infrastructure or phishing sites.
SVG smuggling highlights a growing shift in phishing tactics, where attackers prioritize file formats that can deliver client-side JavaScript without requiring user downloads or macros. This tactic bypasses traditional malware detection systems by avoiding executable payloads altogether.
Security researchers observed this campaign focused on B2B Service Providers that handle valuable Corporate Data regularly, including Financial and Employee data, Utilities, and Software-as-a-Service providers.
This SVG attack vector shows attackers are moving beyond text-based social engineering, leveraging creative content payloads to execute malicious code, J. Stephen Kowski, Field CTO at SlashNext Email Security+ stated.
SVG files appear harmless but can contain embedded JavaScript that executes on open, bypassing traditional email security, which typically targets executable attachments. The challenge is that traditional security often inspects URLs and content only after redirection, necessitating real-time analysis to detect weaponized image scripts, Kowski further added.
Enhancing email security measures and monitoring dynamic script activity within non-traditional file types are key to combating this emergent cybersecurity threat.
Jason Soroko, Senior Fellow at Sectigo, emphasizes the need to treat SVG files as potential executables and implement robust defenses to counter SVG smuggling attacks. He advocates for stripping or blocking script tags, enforcing strict DMARC alignment, and using layered controls like Safe Links and lookalike domain monitoring to disrupt attackers' strategies.
"Defenders must collapse the old distinction between code and content. Treat every inbound SVG as a potential executable. Strip or block script tags. Enforce strict DMARC alignment and auto purge questionable mail," Soroko said.
"The attackers have to rely on complacency ('it’s only an image, it doesn’t execute code') to lull organizations into accepting this content and getting it on the inside of a network," John Bambenek, President at Bambenek Consulting, commented.
He warned that organizations without dedicated security teams remain particularly vulnerable to such techniques, despite the value of research and detection tools for enterprises.