“StrandHogg” 2.0 Returns to the Android Ecosystem With Even Greater Ire
- StrandHogg is back, and this time it is more stealthy and dangerous than its predecessor.
- The flaw affects Android 8.0, 8.1, and 9, and Google is planning to push a fix with the May 2020 patch.
- There have been no cases of activity exploiting the particular vulnerability in the wild yet.
For those of you who have been following the news here, you must remember the ‘StrandHogg’ vulnerability that was discovered in December 2019. That flaw was pretty serious because it was easy to exploit, would have dire consequences for its targets, and, most importantly, it was already under active exploitation. According to a report by Zack Whittaker on TechCrunch, the Strandhogg has returned to the Android world and is way more stealthy than its predecessor. The discovery is the work of the same team that found the original vulnerability - the Oslo-based Promon.
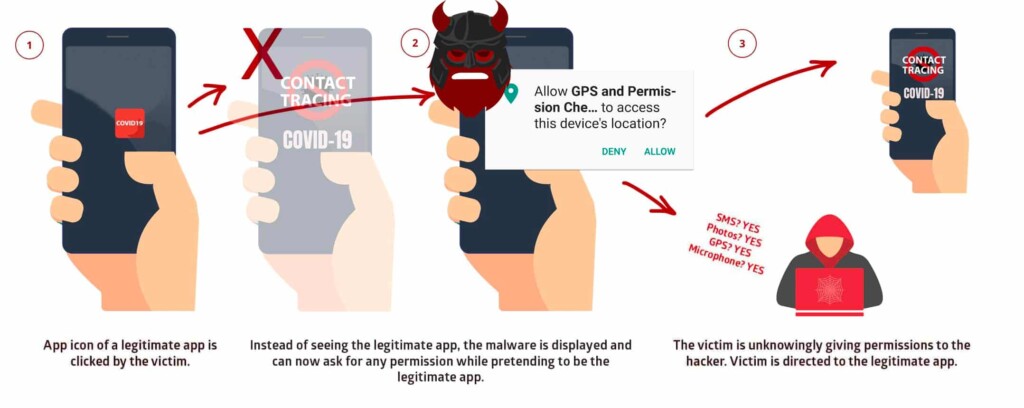
Officially carrying the identifier “CVE-2020-0096” and classified as “critical,” StrandHogg 2.0 enables an attacker to hijack almost any application installed on the target’s phone. This time, it doesn’t exploit the ‘TaskAffinity’ Android control setting, as this hole has been stuffed now. Instead, it waits for the user to click on a legitimate app, and once they do, the malware pops up and asks for the granting of permissions. SMS, Image access, Video recording, Microphone activation, access to GPS data - anything goes. The user falsely things that it is the legitimate app that is requesting the granting of the permission and casually clicks on “Allow.” The user is then directed to the legitimate app, and the malware continues to run silently on the background.
Source: Promon
To launch an attack via StrandHogg 2.0, hackers wouldn’t need to target a rooted device or even to set up a specific configuration on the spoofed apps. They could very easily push login overlay screens, steal login credentials, and eventually exfiltrate the information from the compromised device. All is done without the victim ever realizing that anything wrong has happened. As the Promon researchers add, even AV tools running on an Android device would have trouble detecting a malware tool that exploits StrangHogg 2.0.
Google has already rolled out a patch for this flaw on its partners in April 2020, and Android 8.0, 8.1, and 9 will be covered with a fixing patch in May 2020. There have been no instances of this vulnerability being exploited in the wild, so malicious actors haven’t discovered it yet. As for Android 10 users, StrandHogg 2.0 isn’t impacting the latest OS version. That said, the best method to protect yourself against this danger would be to upgrade to Android 10 - or at least to apply the May patches as soon as they arrive.