STOP Ransomware Finds New Infection Channels Through Software Cracks
- A new variant of the STOP ransomware is out on the hunt for victims, hitting new distribution highs.
- The infections find their way to the victims’ machines through popular software cracks.
- A decryptor that has been around for some time now is still the best hope for the victims.
Security researchers have noticed a spike in the distribution of a new variant of the STOP ransomware, that can encrypt the files of the infected computers and ask victims to pay a redemption fee to get them back. The new channel of delivery seems to be various cracks that people use to activate pirated software such as professional tools and games. These cracks are executable files, and most people voluntarily give them a go on their computer in spite of the usual anti-virus warnings, as cracks trigger these system responses anyway.
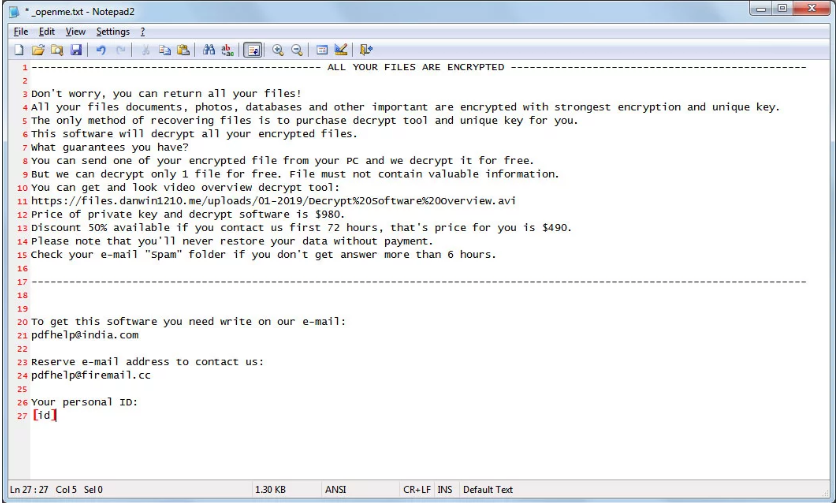
Usually, cracks come with adware tools that install ad-serving and ad-clicking extensions on the users’ browsers. However, the appearance of the STOP ransomware makes things riskier now, with users reporting infections coming from Photoshop, Windows, KMSPico, and Cubase cracks. As the reports arrive from all corners of the internet, it is evident that the infection has spread across many crack hosting websites. The attackers are asking for $980 in order to share the decryption software and the private key with their victims, while they even offer a 50% discount to those who will contact them within 72 hours! The full ransom message is the following:
Image Source: bleepcomputers.com
As it is always the case with ransomware attacks, you are recommended not to give in and pay the attackers, as you will have no guarantee that you’ll get your files back anyway. One possible way to get out of this adverse situation is by using Michael Gillespie’s decryptor that is known to work well with .djvu, .tro, and .rumba extensions.
If you are infected by STOP Djvu #Ransomware with extension ".rumba" and HAVE NOT contacted me already, please do so NOW. I need your ID from the ransom note, and the MAC address of the infected PC. LIMITED TIME.
— Michael Gillespie (@demonslay335) January 21, 2019
Victims will have to use their personal IDs in order to get help, which is found in the last line of the ransom note and is unique to each infection. Please note that with the way the STOP ransomware works, any new files created on the infected system will also get encrypted after a while, as the malicious software is creating a scheduled task on Windows’ “Time Trigger”, so nothing is left unaffected by its bothersome presence. That said, using an infected computer any further is not a recommended practice. Indicators of compromise by the STOP ransomware include the presence of the “openme.txt” ransom note and the fact that all of your files will now get a “rumba” file extension in their name.
Have you ever gone through this unfortunate process? Let us know of your experience in the comments below, and don’t forget to warn others by sharing this story through our socials on Facebook and Twitter.