There Are Still a Million of Unpatched Exim Servers Online
- Exim has recently been the source of trouble, with the “Sandworm” team using scripts to compromise corporate networks.
- The mail server agent has issued fixing patches, but many instances are still using vulnerable versions.
- Russian hackers are still happy to choose targets between roughly a million of exploitable systems.
It’s been about a week since the NSA (National Security Agency) warned the public about Russian hackers targeting Exim mail servers. While the patching started about immediately, there are still many vulnerable systems out there. The vulnerability under exploitation is CVE-2019-10149, which enables a remote attacker to execute arbitrary commands on the target system. The actors were reportedly engaging in disabling security settings, executing scripts that helped them explore corporate networks, and adding privileged users that could move laterally and in-depth into the target organization. All that said, updating to Exim 4.93 or later is considered absolutely critical, and should be done immediately no matter what.
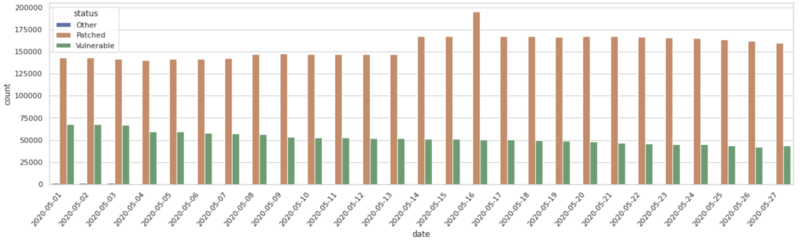
Yet, despite the official warnings and the ample press coverage that the matter enjoyed, there are about a million systems that remain stuck in using vulnerable versions. Exim 4.87 to 4.91 are all vulnerable to the aforementioned bug. In addition to that, versions 4.92.1 and 4.92.2 are also susceptible to CVE-2019-15846 and CVE-2019-16928, respectively, which are two separate bugs discovered by the RiskIQ team. According to the same group of experts, there are still about a million vulnerable instances that remain online out there, so Russian hackers still have too many options.
Source: RiskIQ
All three bugs concern remote code execution scenarios, and they are all being actively exploited in the wild. In fact, they have been under exploitation for many months now, so upgrading Exim to 4.93 is now way overdue. The group that is engaging in the exploitation of Exim Internet Mailer vulnerabilities is the “Sandworm” team. The IP addresses and domains that have been associated with this activity were determined to be the following:
- 95.216.13.196
- 103.94.157.5
- hostapp.be
Source: RiskIQ
This is yet another stone to be added in the pile of warnings that have amassed urging system administrators to act responsibly and patch their Exim systems. With every day that passes, vulnerable systems are seeing their chances of getting hacked increase exponentially, as the number of unpatched systems decreases, and the actors narrow down their targeting scope. If patching is impossible for any reason, you should direct your efforts towards detecting exploit attempts and unauthorized network setting changes as soon as possible, and trying to block them. Applying network segmentation and defense zoning - while also implementing aggressive firewall rules - would be great as well.