Steam Remains a Susceptibility for Windows as the Latest Fix Gets Bypassed
- Researcher confirms everyone’s hypothesis that the Steam Client is still a susceptibility for Windows.
- The latest fix can be easily bypassed through the replacement of a Steam DLL and an executable with their older versions.
- This replacement is the direct consequence of an intrinsic security flaw that plagues Steam in general.
Steam has been under the spotlight recently for following risky operational practices that could lead to a full system takeover on Windows installations. As we reported last week, Valve tried to fix a privilege escalation zero-day that was based in the way that the Steam Client Service works. However, security researchers warned that this fix would mean nothing, as it could be easily bypassed. A few days after that, a security researcher named Xiaoyin Liu has published a way to bypass the reg-symlink fix and didn’t even bother to contact Valve first.
I found a way to bypass the fix. The bypass requires dropping a file in a nonadmin-writable location, so I think it's out-of-scope for Valve. Write-up: https://t.co/Lalum8LTvY cc @PsiDragon @enigma0x3 @steam_games #infosec #steam #bugbounty https://t.co/qIylEG7u2L
— Xiaoyin Liu (@general_nfs) August 15, 2019
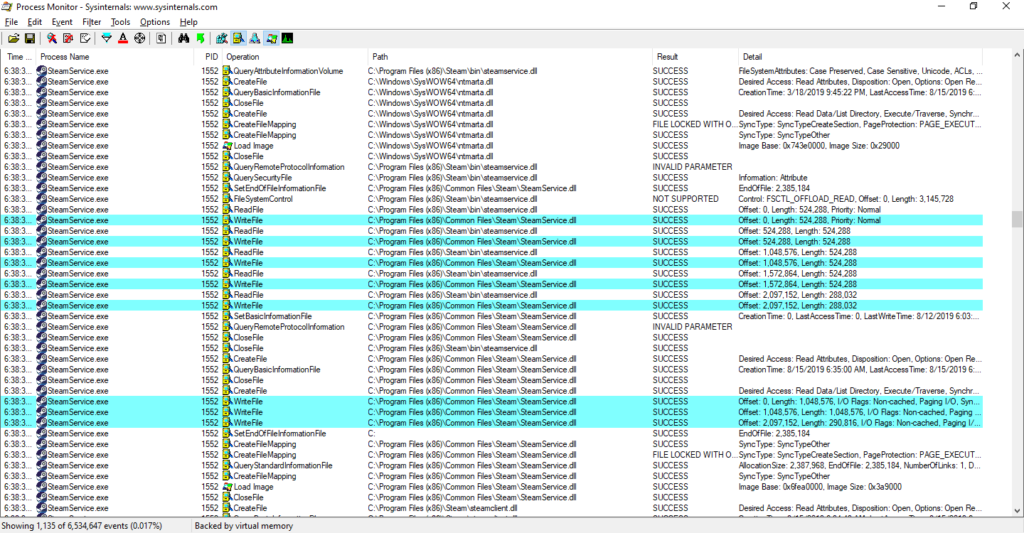
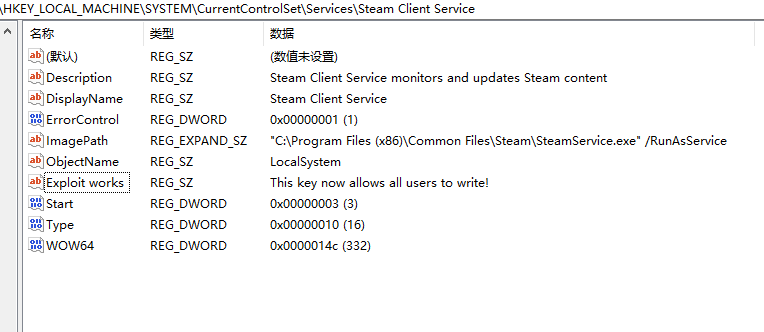
As the researcher demonstrated, by replacing the SteamService.exe and SteamService.dll files that are under C:\Program Files (x86)\Steam\bin\ with older versions, the privilege escalation problem returns. As it was already theoretically known, Steam’s key security issue is the fact that anyone is granted full access to the USERS groups, so the files can be modified or replaced as needed. This could be done either manually or via a specially crafted malware that would have the older Steam Service DLL and executable bundled into it. This is how Steam works, and it means that any Windows system with Steam installed is vulnerable to a rich set of severe threats with highly destructive potential.
image source: https://xiaoyinl.github.io
image source: https://xiaoyinl.github.io
All that said, if you’re wondering why Xiaoyin Liu has decided to straight out publish the details of his bypassing method instead of warning Valve, the answer goes back to how we have ended up to where we are today in the first place. Previously, researcher Vasily Kravets sent an urgent notice about the zero-day exploit that plagued the Steam Client Service, only to receive a disregarding message that deemed the flaw as “out of scope” and “not applicable”. This hasn’t resonated well with the bug bounty and white-hat hacking community, so here is what Liu had to say about this:
“Since Valve explicitly excludes 'attacks that require the ability to drop files in arbitrary locations on the user's filesystem', I don't think they are interested in fixing this one. In my opinion, even allowing all users to have write access to C:\Program Files (x86)\Steam itself is a vulnerability because any standard user can replace Steam.exe in this folder, and when admin users log in and launch Steam.exe, a malicious executable code runs, and they won't notice it. I reported this to Valve in Feb 2017, and I got no reply except an acknowledgment of receipt. Given that, I decided not to report this bypass to Valve, but rather disclose it.”
As we predicted last week, Valve will be forced to deal with this as the clock is ticking against them. The danger of having a specially crafted malware that targets millions of gamers out there is real, so there’s no more margin for denial at this point. Steam is a susceptibility, and for anyone who cares about the safety and security of their Windows system right now, you should consider limiting your access to this game launcher.
Are you still comfortable with using Steam, or have you taken any precautionary measures? Let us know in the comments section down below, and don’t hesitate to join the discussion on our socials, on Facebook and Twitter.