Stealerium Infostealer Introduces Automated Sextortion Capabilities via Adult Content Screenshots and Camera Access
- Infostealer surge: Security researchers have noticed a spike in Stealerium campaigns, which use a variety of lures.
- Potential sextortion: The malware's particularly concerning feature includes automated detection of adult content browsing sessions.
- Other stolen data: It can also exfiltrate browser credentials, banking data, crypto wallet access, VPN configurations, and more.
A Stealerium malware campaign surge reveals advanced information-stealing capabilities that include sextortion distributed through multiple attack vectors since May 2025, when threat actor groups TA2715 and TA2536 were seen leveraging open-source malware frameworks for extensive data exfiltration operations, moving away from Snake Keylogger, also known as VIP Recovery.
In August 2025, additional campaigns that employed several persuasive lures and delivery mechanisms were identified but not attributed to tracked threat actors.
Technical Infrastructure and Attack Methodologies
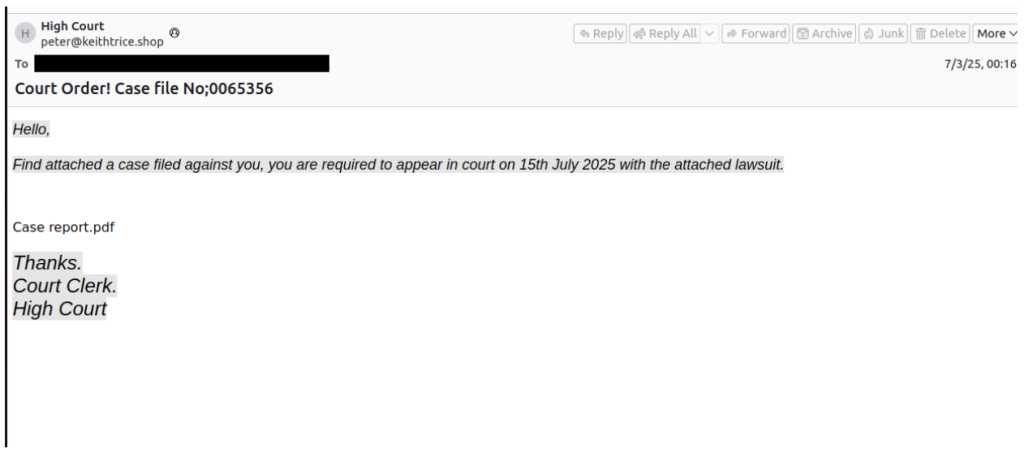
The Stealarium infostealer campaigns demonstrate unprecedented sophistication in social engineering techniques, utilizing diverse delivery mechanisms including compressed executables, JavaScript, VBScript, ISO, IMG, and ACE archive formats, Proofpoint threat research has documented.
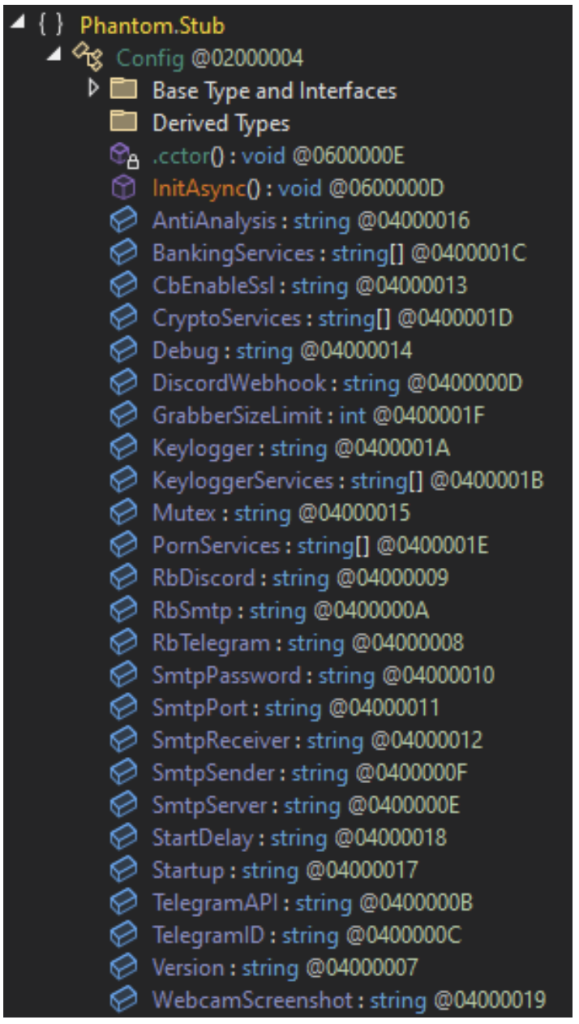
The report employs the name Stealerium to refer to multiple other infostealers that share significant overlap with the original Stealerium, such as Phantom Stealer.
Stealerium's comprehensive data extraction portfolio encompasses browser credentials, banking information, gaming platform tokens, cryptocurrency wallet access, VPN configurations, and sensitive document repositories.
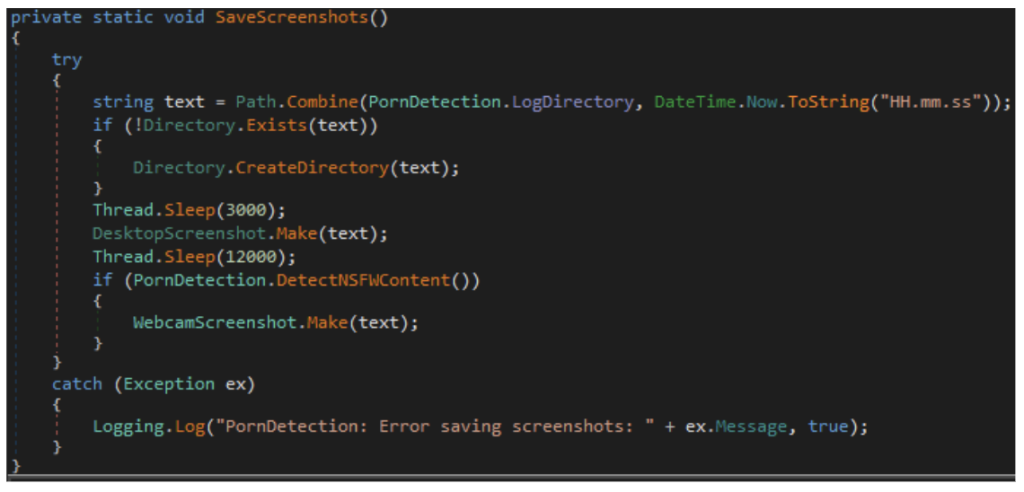
The malware's particularly concerning feature includes automated detection of adult content in open browsing sessions, combining desktop and webcam screenshots for potential sextortion operations.
The malware's reconnaissance capabilities extend beyond traditional credential harvesting, incorporating comprehensive system profiling, including hardware specifications, installed applications, and network topology mapping.
Advanced variants utilize Chrome Remote Debugging functionality to bypass browser security features, enabling the extraction of encrypted cookies and session tokens.
Threat actors employed convincing organizational impersonations spanning charitable foundations, financial institutions, legal entities, and document services to maximize victim engagement rates.
Technical analysis revealed systematic exploitation of "netsh wlan" commands for Wi-Fi profile enumeration and sometimes PowerShell-based Windows Defender exclusion manipulation, as well as scheduled task persistence mechanisms.
The initial TA2715 activity marked the first observed use of Stealerium in Proofpoint threat data in over a year.
Cybersecurity Risks and Organizational Impact
The threat landscape analysis indicates a shift in cybercriminal preferences toward lower-profile operations, with a focus on avoiding large-scale ransomware campaigns that attract law enforcement attention.
Multiple exfiltration channels, including SMTP, Discord webhooks, Telegram APIs, Gofile cloud storage, and Zulip chat services, provide operational redundancy and detection evasion capabilities.
Dynamic anti-analysis implementations incorporate real-time blocklist updates from public repositories, sophisticated timing-based emulation detection, and comprehensive sandbox environment identification protocols.
Organizations must implement comprehensive monitoring for suspicious PowerShell activity, unauthorized network reconnaissance commands, and anomalous data egress patterns to cloud-based services unauthorized for corporate use.