State-Sponsored DNS Hijacking Campaigns Are Targeting North Africa and the Middle East
- Highly advanced malicious actors are targeting critical organizations including ministries, energy companies, national security agencies, and more.
- The campaign is called “Sea Turtle” and it’s based on the manipulation of DNS records.
- Stopping the effectiveness of these methods immediately is crucial before it goes global.
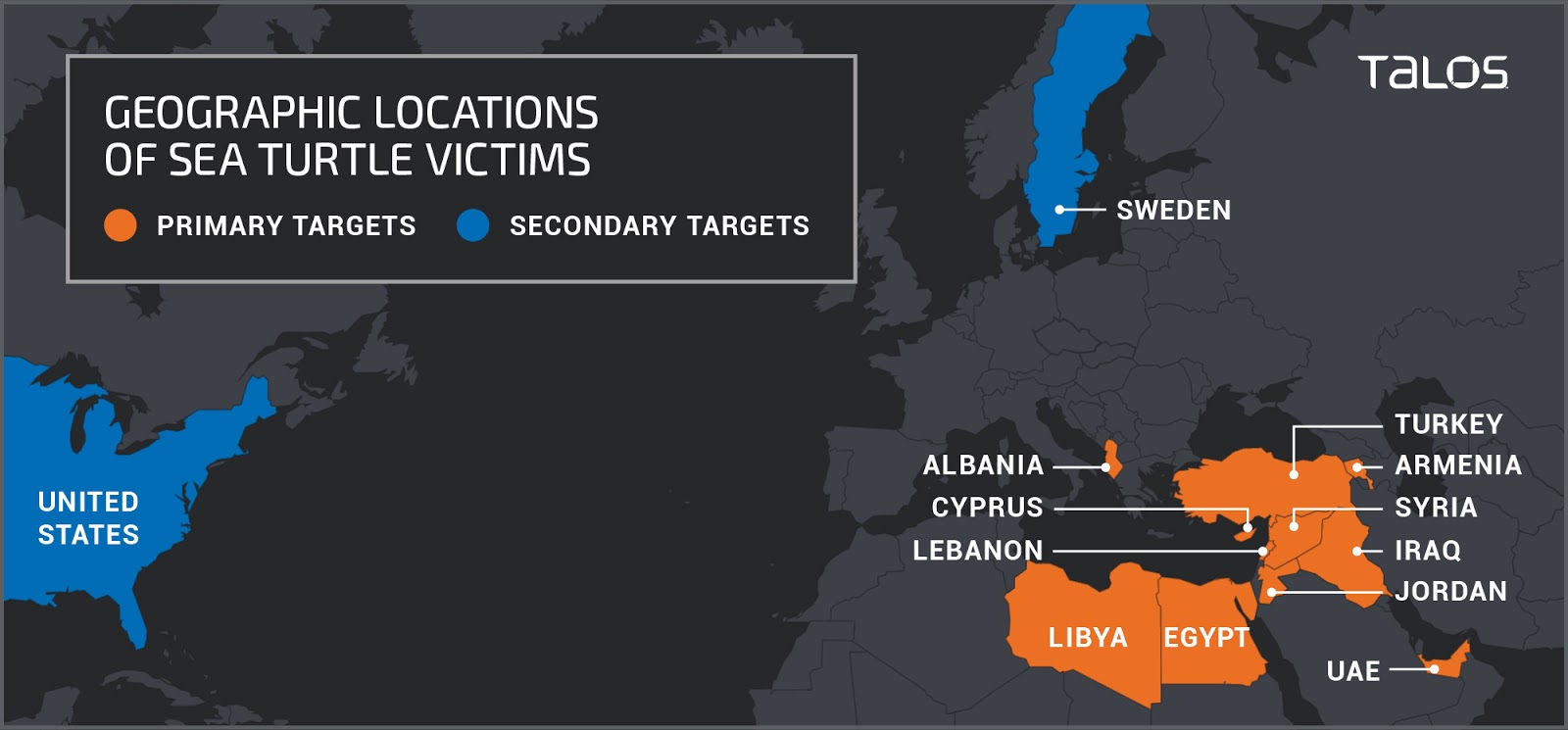
Cisco Talos is warning the world of a malicious campaign that they call “Sea Turtle”, and which has been going on since January 2017. According to the researchers, the campaign has targeted at least 40 national security and other critical organizations in 13 countries located in North Africa and the Middle East. According to the researchers, the kind of DNS hijacking that was employed in the context of this campaign indicates that the actors behind it are state-sponsored and knowledgeable experts who want to establish persistent access to highly-valuable networks.
image source: blog.talosintelligence.com
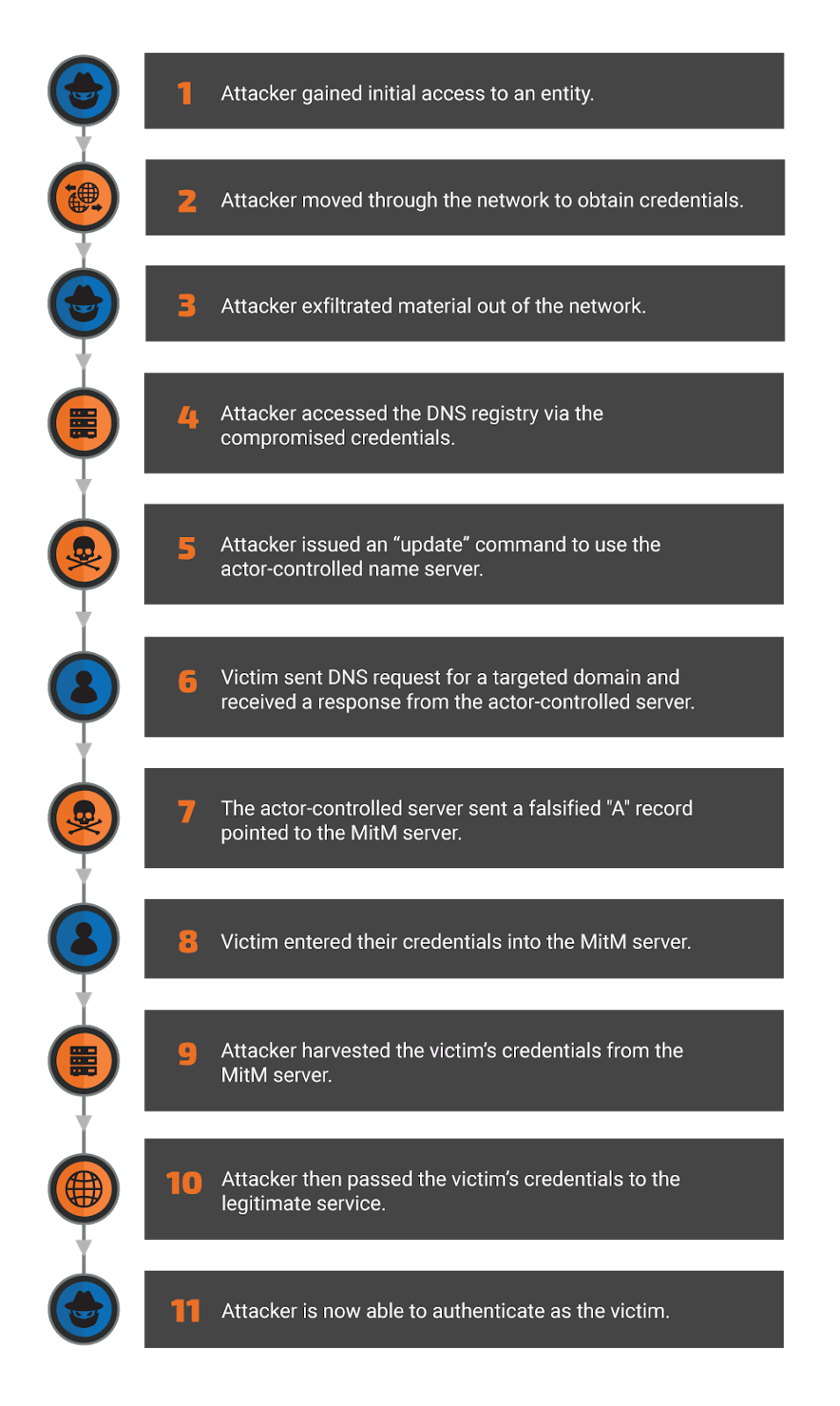
The primary victims of the “Sea Turtle” campaign are ministries, energy companies, telecommunication infrastructure organizations, and national security agencies. The malicious actors target various DNS registrars and registries - and successfully compromise them. The methodology of the attackers includes the establishment of the control of the target’s DNS records, the modification of those records to point the victims to malicious servers, and the capturing of their credentials through a form of advanced phishing. As this goes on at such a fundamental level, even VPN applications are not safe from MitM (man in the middle) attacks, which are intercepting sensitive data and gaining remote access.
image source: blog.talosintelligence.com
Having hijacked the DNS registries and registrars, the actors employ self-signed certificates from Sectigo, Comodo, and Let’s Encrypts, gathering the organizations’ SSL certificates through MitM. This takes them to the next step, which is the seamless access to the targeted networks as the SSL certificates are used on the malicious servers. Cisco researchers share multiple examples that point to this methodology, from the deployment of their own ASA (Cisco Adaptive Security Appliance) certificate to steal VPN credentials, to a NetNod compromise through DNS records manipulation and a recent targeting of the Cafax consulting firm.
Besides the fact that the actors seem to be state-sponsored, and aside from the fact that the targeted organizations are neuralgic to the operation of their respective countries, the “Sea Turtle” campaign is very important because it threatens to blow up the very trust that users have on the global DNS system, and by extension, the internet. While the campaign was limited to North Africa and the Middle East, the actors could extend their scope and render the internet an untrustworthy communications platform, pulling the rug from under the feet of the global economy.
Cisco urges companies, agencies, and organizations to use a registry lock service so as to prevent DNS record manipulation, or to implement multi-factor authentication for accessing the DNS records. Also, applying patches, conducting frequent network-wide password resets, and monitoring DNS records on key network domains will be crucial in the effort to stop the Sea Turtle actors. If they face such obstacles right now, the chances of having the campaign go global will be reduced.
Care to share your views on the above? Do so in the comments section beneath, and don’t forget to help us spread the word by sharing this post through our socials, on Facebook and Twitter.