Another Spectre-like CPU flaw disclosed by Google, Intel and Microsoft
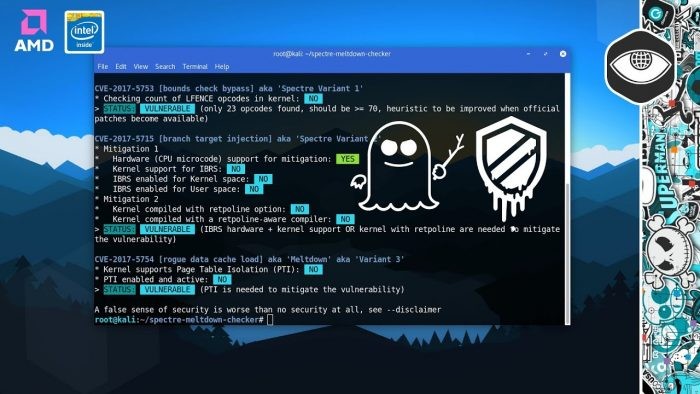
- Following the discovery of Meltdown and Spectre security flaws, we have yet another CPU flaw that was discovered.
- Google, Intel, and Microsoft have disclosed the Speculative Store Bypass which could allow attackers which can be used to exploit certain kinds of data on a computer.
- A patch for the bug has been sent out to OEMs, which can lead to a 2 to 8% drop in performance on Intel CPUs.
Following the discovery of the Meltdown and Spectre CPU exploits, we now have another exploit in our hands for Intel CPUs. The exploit being termed by Microsoft and Google as ‘Speculative Store Bypass (variant 4)’. According to the US Computer Emergency Readiness Team, the exploit can allow attackers to read old memory values that are stored in a CPU’s stack as well as other memory locations.
The exploit is available on some of the world’s most popular processors from Intel. The exploit was first found in November 2017. The variant 4 of the exploit uses speculative exploitation, which is known to be an optimization technique in CPUs to get access to specific kinds of restricted data. Attackers can use web browsers to run JavaScript exploits to get access to data stored in the CPU’s stack and other memory locations.
Image Courtesy of 9to5 Mac
Intel confirmed amidst worries that the exploit has not been seen running in the wild. Patches to counter the Meltdown and Spectre prevent the Speculative Store Bypass (variant 4) exploit from being used through web browsers as well. Further patches to prevent any form of exploitation have been sent over to OEMs by Intel to issue firmware updates for products for preventing any attacks.
The Speculative Store Bypass Protection is disabled by default and users will need to manually enable it which can lead to a 2 to 8% drop in CPU performance depending on the CPU variant. It is recommended to enable the protection despite the drop-in performance for added protection. The upcoming Intel chip designs will be free from this security flaw with the exploit being patched at a hardware level during the manufacturing process. All of the CPUs up to the 8th generation Intel CPUs have been marked as vulnerable.