SpearSpecter Cyberespionage Campaign Linked to Iranian IRGC Targets High-Value Officials
Key Takeaways
- IRGC connection: A sophisticated espionage operation has been attributed to Iranian threat actors aligned with the IRGC-IO, also known as APT42.
- Social engineering: High-value senior defense and government officials are targeted with personalized lures, such as fake conference invitations, and via WhatsApp.
- Malware deployed: A modular, PowerShell-based backdoor known as TAMECAT malware features multi-channel C2 capabilities using Discord and Telegram.
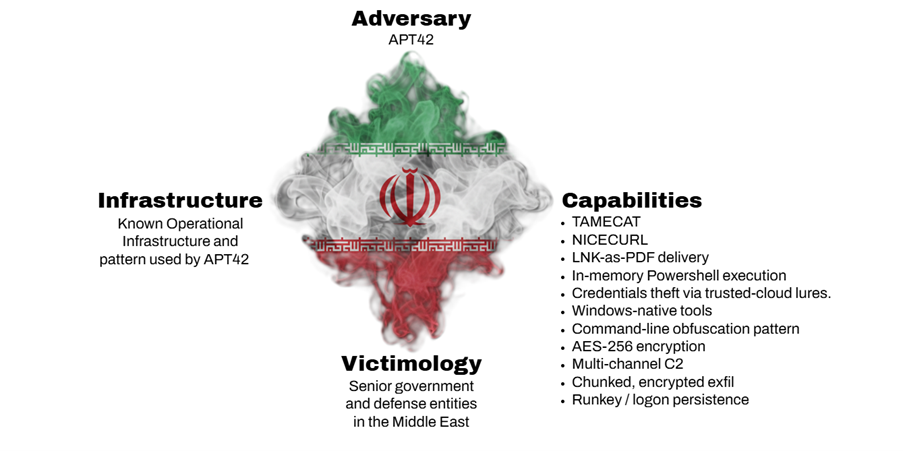
An ongoing espionage operation, dubbed the SpearSpecter campaign, conducted by Iranian state-aligned actors was linked to the Islamic Revolutionary Guard Corps Intelligence Organization (IRGC-IO), also tracked as APT42, Mint Sandstorm, Educated Manticore, and CharmingCypress.
It focuses on intelligence gathering from high-profile individuals in government and defense and their family members, researchers from Israel's National Digital Agency have uncovered.
Sophisticated Social Engineering and Malware Deployment
The operation is characterized by its patience and stealth, with attackers adapting their tactics to remain undetected while pursuing strategic objectives. SpearSpecter operators employ advanced social engineering, moving beyond simple spear-phishing.
They invest days or weeks cultivating relationships with their targets, often impersonating trusted individuals and using direct communication on platforms like WhatsApp to build credibility.
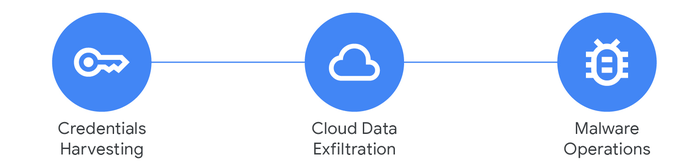
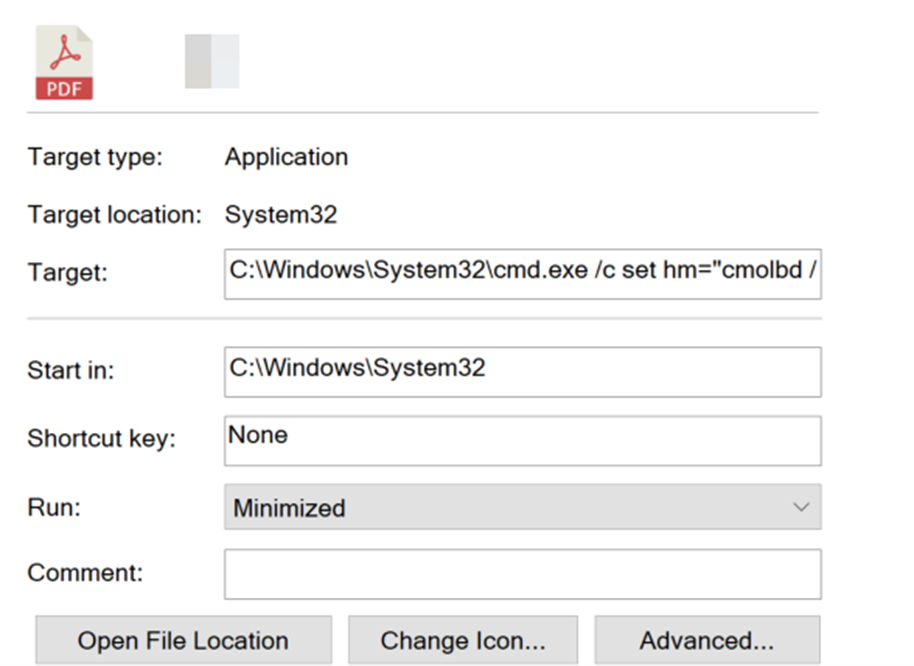
Once trust is established, victims are lured into executing malicious files. For long-term cyberespionage, the campaign deploys TAMECAT, a sophisticated PowerShell backdoor. Previously, APT42 was observed operating multiple infrastructure clusters in parallel, exploiting Google Sites fake logins, and distributing NICECURL and TAMECAT malware.
Attackers use a search-ms URI handler exploit to deliver an LNK file from a WebDAV server, which then fetches and executes the fileless malware in memory, a pattern publicly attributed to APT42 by Mandiant and Volexity.
Technical Details of TAMECAT and IRGC Cyber Operations
The TAMECAT malware is highly modular, enabling attackers to perform reconnaissance, exfiltrate data, and execute remote commands. A significant evolution in this campaign is its use of Discord and Telegram for command-and-control (C2) infrastructure, providing resilient and difficult-to-detect communication channels.
This use of legitimate services for C2, combined with custom tooling and specific TTPs, reinforces the attribution to IRGC cyber operations.
The campaign showcases the increasing technical sophistication of state-sponsored actors and their ability to blend malicious activity with normal network traffic. Specifically, TAMECAT leverages Cloudflare Workers as a serverless C2 edge.
Mitigation recommendations include, among other things:
- Enabling PowerShell script block logging,
- Installing and configuring Sysmon to report to a SIEM solution,
- Installing an EDR product
- Disabling the "search-ms" URI protocol handler,
- Use a proxy to filter network activity,
- Building behavior rules based on the outlined TTPs.
In September 2025, Israel seized over 180 crypto wallets reportedly tied to Iran's IRGC, and the U.S. charged three IRGC-linked Iranian nationals for election interference and cybercrimes. Last month, the British MI5 warned U.K. politicians of state-sponsored espionage threats from Iran, China, and Russia.
The cybercriminal landscape is clearly shifting towards advanced social engineering for successful attacks, a characteristic also of the new Scattered LAPSUS$ Hunters Extortion-as-a-Service cybercriminal alliance.