Spammers Today Can Start a Phishing Business With a Handful of Dollars
- Actors who want to enter the phishing business can do it with less than $20.
- There are multiple forums, platforms, and tools on offer to support these activities.
- The problem is growing larger, as non-tech-savvy users are joining in to make a quick buck.
Phishing is a huge problem today, affecting both businesses and regular internet users. It can lead to the installation of ransomware, direct loss of money, stealing of information, or the planting of backdoors and trojans on the target system. The Photon Research team belonging to the 'Digital Shadows' cybersecurity firm has looked into the current state of the phishing scene. They are revealing how much it costs to enter the ecosystem, what forums and platforms support the actors, and which are the most prominent tools used in the field.
Phishing is an operation that constitutes of four elements, namely creating the phishing email, distributing the messages, collecting data from victims, and then cashing out. The cost of launching an operation like this has dropped to a record low, according to the above-mentioned researchers. Now, the actors don't need to have any technical knowledge whatsoever. Everything that they may need is already for sale out there, and it's preconfigured and ready to hit. Here's a breakdown of what amount phishing actors would need to pay in order to get their business started:
- Phishing tutorial on cybercriminal forums - $25
- Malvertising ad - $20 to $550
- Cloned banking webpage template - $25 to $70
- Phishing webpage template - $2 to $3
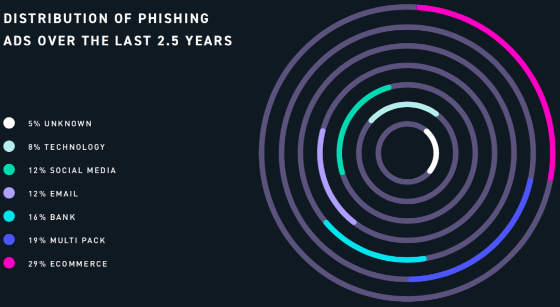
To lure people in, one would need advertisements - and the criminal's specific target determines the types of these ads. 'Digital Shadows' discovered that 29% of malvertising entries concerned the e-commerce field, while the banking sector accounts for 16%. Of all ad types, those that point to renowned investment companies sells for the highest price, with one example reaching up to $550.
Source: Digital Shadows
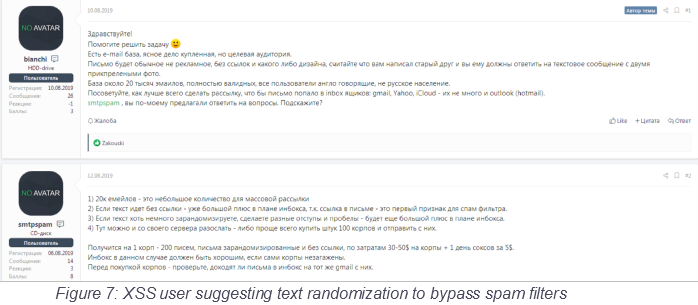
As for the email, these are almost always custom creations, loosely based on templates that circulate the darknet forums for free. Crooks are performing the required modifications to messages that often come directly from the spoofed entities, and then apply some anti-spam filtering and detection measures. They are incorporating formatting tricks, splitting up words, using Cyrillic characters, and generally do everything possible to fool the parsing algorithms.
Source: Digital Shadows
For those who don't want to consider all details on every step of the way, they may just buy their membership on a "phishing-as-a-service" (PHaaS) platform. This alleviates the need for setting up the backend of the operations and saves time and financial resources. Access to PHaaS is sold through monthly subscriptions that offer various tiers, each coming with different levels of features.
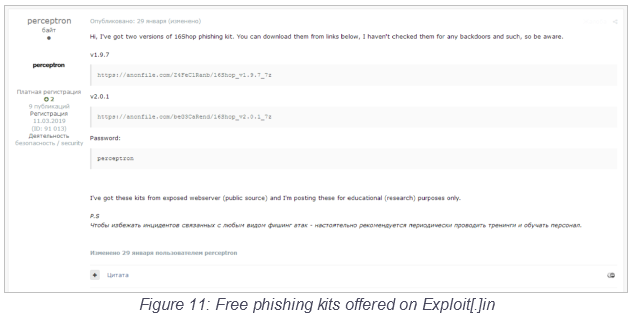
And then there are the "phishing kits" that still leave everything on the actor's hands, but they offer all of the required tools in a single package. These kits contain pre-built websites with a rich selection of login pages, so the user only picks the entity they would like to spoof. No technical knowledge is required, and so the barrier to enter the phishing scene is further lowered because of them. Usually, the kits cost as little as $15, but they are often even offered for free on cybercrime forums like "Exploit[.]in".
Source: Digital Shadows
When it comes to the distribution of the spam email, actors prefer to use cracked versions of legitimate software. Powerful and versatile tools like the "Atomic Email Tracker" are sold for a mere $2 on darknet marketplaces, or even offered for free on forums. The ideal scenario in this step is to compromise the target's SMTP and send nefarious emails from corporate email servers. Otherwise, the messages may end up straight in the recipient's spam folder.
Source: Digital Shadows
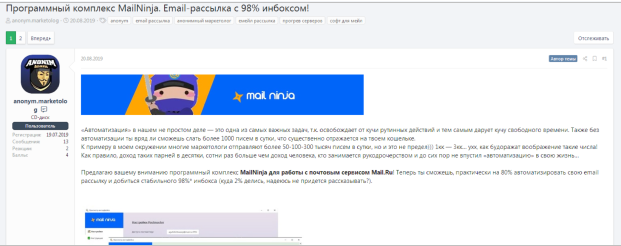
Another popular option through which actors add legitimacy to their spam emails is to use public infrastructure and trusty email provider services. The most popular is "Mail Ninja," which sends messages through mail[.]ru and promises a successful delivery rate of 98%. As expected, these services are advertised on cyber-criminal forums like the XSS.
Source: Digital Shadows
Spam lists are one of the most valuable resources for phishing actors. Once you have a good list of real email addresses pointing to high-standing individuals, you basically have two paths in front of you. You may either engage in phishing yourself or sell the list on forums like the "BlackHatWorld." The pricing depends more on the status of the targets rather than the number of entries. For example, a list containing 10,000,000 random emails costs around $13, while a list offering 150,000 emails of wealthy persons from the UK sells for $20.
Source: Digital Shadows
Phishing actors also need tools that can help them perform "man-in-the-middle" attacks on corporate networks, and which enable them to steal valuable information that they could use at a later stage. Right now, the most popular tools that act as reverse proxies and intercept network traffic are the "Evilginx 2" and the "Modlishka." Both can also bypass MFA (multi-factor authentication), allowing the attacker to infiltrate into the network as a user, and then harvest data without raising any suspicions.
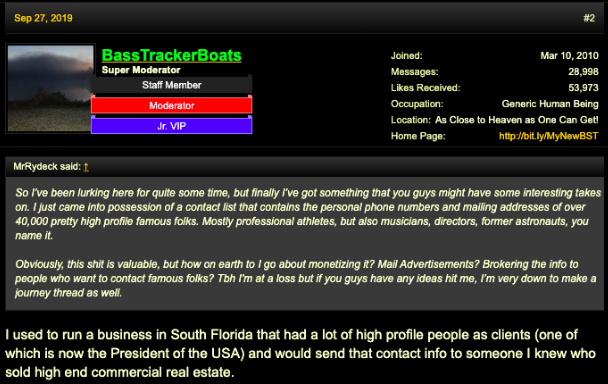
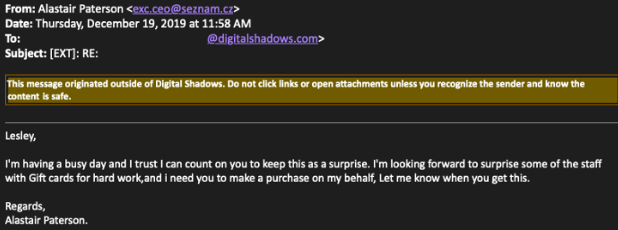
Ultimately, "Social Engineering" remains the king when it comes to fraud rates, as untrained employees remain the weakest link of the chain. Nowadays, actors engage in lengthy reconnaissance only to figure out how a company's CEO writes their emails, and only then they try to trick his/her subordinates with an BEC-derived message.
Source: Digital Shadows
In the end, it's all about cashing the money, and this is done almost exclusively with cryptocurrency. BTC, XMR, LTC, BCH, and anything that offers a shroud of anonymity for the actors, come into play in the final stage. The following stats provide an idea of the size of "Sextortion," which is just a subcategory of social-engineering-based phishing. The counters below started in the latter half of 2018, and they surely paint a dire picture.
Source: Digital Shadows
With all that's going on, and the forecast being pretty bleak for 2020, organizations should finally implement phishing mitigation strategies. If you want to lower the chances of falling victim to phishing actors, the most essential and effective strategies are the following:
- Train your personnel on how to identify phishing emails and BEC-based social engineering attempts.
- Apply two-factor authentication everywhere, so as to make it harder for actors to steal internal email accounts.
- Implement security measures such as Sender Policy Framework (SPF), Domain Message Authentication Reporting and Conformance (DMARC), and DomainKeys Identified Mail (DKIM).
- Monitor the registration of typo-squatted domains and prepare for upcoming waves.
- Impose strict policies that severely limit the information your employees are allowed to share on social media.