Source Code of “ArisLocker” Ransomware Appears on the Dark Web
- The ArisLocker ransomware source code is being distributed on the dark web.
- The strain seems to have a weakness in its encryption system, so white-hat researchers could exploit it.
- We expect to see a spike in the deployment of ArisLocker against victims in the upcoming weeks.
According to the latest reports that come from Cyble’s researchers, actors have posted the source code of the “ArisLocker” ransomware on the dark web. The malware analysts in the team grabbed the code and tried to figure out whatever they could. This is a ransomware strain for which there are no available decryptors yet, and locating its source code will surely bring developments in this field. For now, the things that Cyble’s team could figure out about ArisLocker are the following:
- ArisLocker begins by urging the victim to enter their login credentials on a fake screen.
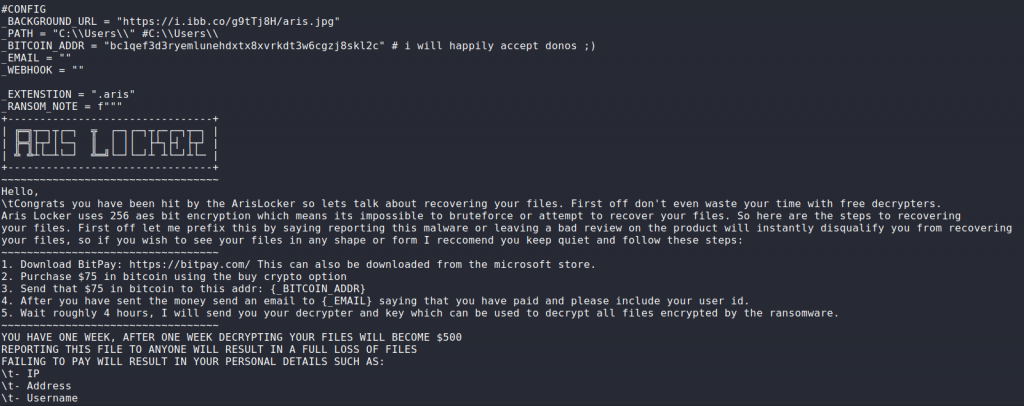
- The malware scans “C:\Users\” and “#C:\Users\,” enumerating files suitable for encryption.
- A queuing system pushes all files in order for the encryption thread.
- The encryption takes place using a key that is stored in a remote address. The type of encryption is 256-bit AES.
- The encrypted files are saved on their original paths using the “.aris” file extension.
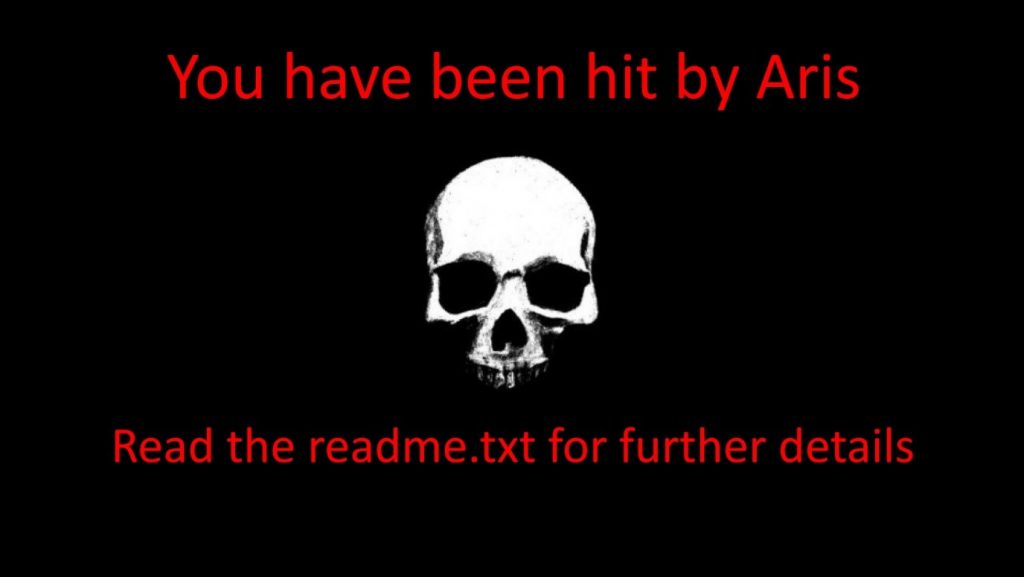
- A “readme.txt” is generated and placed on the desktop folder.
- The desktop background image is changed to warn the user about what happened.
The “default” ransom ArisLocker demands is set to $75, including a threat to go up to $500 if the victim fails to pay within a week. Of course, all may be changed to anything the actor would prefer to use, so these figures are merely indicative.
A hopeful part of Cyble’s report is that the use of “AES.MODE_ECB” wasn’t the wisest choice for the ArisLocker ransomware. This makes the decryption easier, but it also creates a platform for creating a free decryptor. ECB uses identical plain text blocks that are encrypted to identical cipher text blocks, and there we have a potential weakness. It may also mean that Aris operators are honest about their promise to deliver the decryption key, and also that the chances of having errors during the decryption process are low. Of course, an update could change this, but all of it applies to the leaked source code.
Actors will try to exploit this source code as soon as possible before white-hat researchers get the chance to release decryptors, so we expect to see a spike in ArisLocker infections now. That said, take backups, keep your precious files offline, avoid opening email attachments or clicking on email buttons/links, and don’t trust plugging any USBs on your computer.