Phishing Campaign “Soula” Steals Credentials from Visitors of Reputable Websites
- Trend Micro has noticed a new watering hole phishing campaign that compromised high-ranking websites.
- The malicious actors employed smart script settings that made their activity more believable and less suspicious.
- Upon their discovery and report, the actors have changed to another server and added obfuscation to their script.
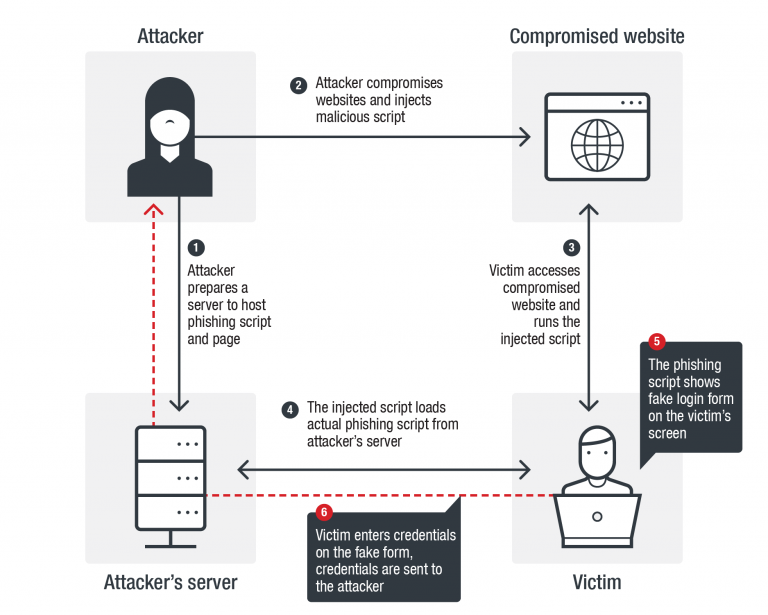
Trend Micro researchers have been following a new type of a phishing campaign that utilizes the watering hole technique to acquire login credentials from victims. Given the name “Soula”, this new campaign was found to target popular South Korean websites that are among the top 300 most visited in the country, and thus are considered especially trustworthy by their visitors. The infection of the websites is done through the injection of a JavaScript code that initiates a step-by-step exploitation process, leading to the tricking of the user into inputting their credentials in a fraudulent form.
The routine goes as follows. The victim visits the compromised website, and so the JavaScript code runs on their browser, loading the actual phishing script from the actors’ server. Depending on whether the victim is visiting the website using a mobile device or a laptop/PC, they are served with the corresponding version of the spoofed form. Should the victim get convinced by it, the entered credentials go directly to the attacker’s server. The script does not only identify the victim’s machine but also filters out bot crawlers and threat engine scanners, using header string checks.
image source: blog.trendmicro.com
Another way to prevent detection and suspicion from the website administrators is the methodical delivery of the phishing forms. The malicious script sets a browser cookie to the devices of the victims that were served with the fake forms, which sets an expiration period of 12 hours for the fake login. Moreover, the cookie is also counting the times the victim visits the compromised website and enables the pop-up that delivers the fake form only after the sixth visit. This is to trick the visitor into thinking that nothing weird is going on, as they will not be greeted with a login form right away but at a more believable point.
image source: blog.trendmicro.com
Trend Micro has managed to figure out that it was a Cloudflare domain that hosted the malicious server and contacted the network services company to remove it, which they did. However, that didn’t bruise the attackers, as they responded by moving to another compromised server and added heavier obfuscation to their JavaScript code. While the South Korean websites are not compromised anymore, Trend Micro researchers believe that this first stage was only a research and info-collecting phase for the cybercriminals. It is possible that “Soula” will grow bigger and stronger, entering the global exploitation scene soon.
What tools are you using for blocking malicious scripts and pop-ups? Share the details in the comments section below, and don’t forget that you can warn others by liking and sharing this story through our socials, on Facebook and Twitter.