Someone Has Leaked the Key Used by REvil in the Kaseya Attack
- An unknown person has posted the REvil universal decryptor key for the Kaseya attack.
- Unfortunately, the key isn’t of any use to victims of REvil outside the Kaseya incident.
- REvil has gone offline for a while now, but private keys remain a tightly held asset.
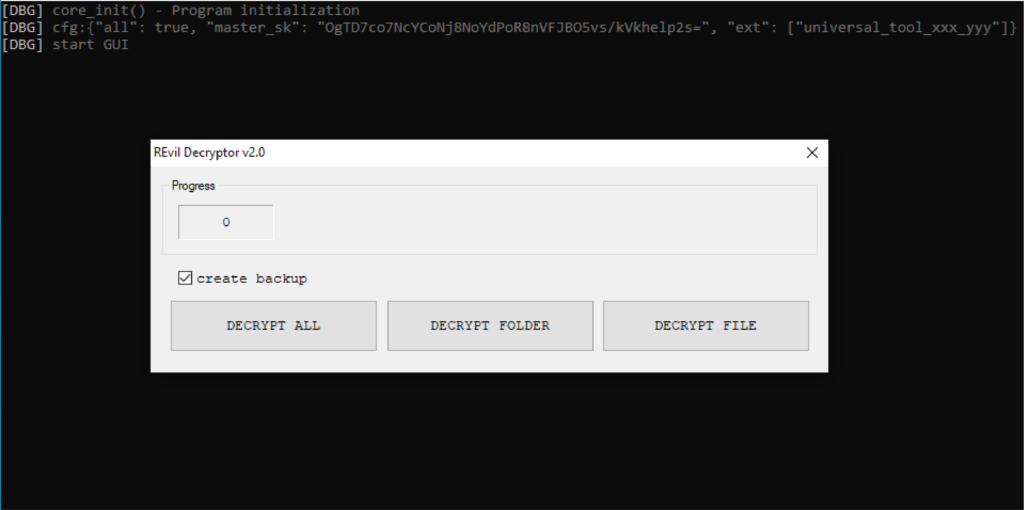
A user named “Ekranoplan” has posted a link to GitHub on the XSS forums, sharing a screenshot that appears to contain the master key to unlock files encrypted by REvil during the Kaseya attack. The notorious ransomware group compromised the managed service provider and then proceeded to encrypt the systems of about 60 of its clients (affecting 1,500 businesses), demonstrating state-of-the-art operational priggery. Two weeks later, the firm obtained a universal decryption key without disclosing how exactly they got it and whether or not they had paid a ransom to the crooks.
Now, an unknown person decided to just share what is supposedly the same key with everyone - and indeed, the first conclusions that come from experts in the field is that the particular decryptor key is linked to the Kaseya incident. Those who have received the key from Kaseya were under a non-disclosure agreement, so the poster could be an employee of one of Kaseya’s clients who wanted to share it anonymously, but that’s just a guess. Another possibility is that the post is from one of REvil’s affiliates or even core members, as the group is believed to have gone defunct by now.
For Kaseya and its clients, the decryption procedure is already behind them, so the question is how useful this key could be to REvil victims in general. As decryption experts point out, this key won’t be very helpful to victims of other campaigns as REvil was using a different operation master key each time. In fact, REvil used a pair of one public and one private key for each sample and each victim, and since this is a public master key, we only got half of what’s needed and not the most valuable of the two.
Still, some researchers tested the key against non-Kaseya samples, and most of them just confirmed that the key wouldn’t decrypt any systems locked by REvil, outside of the Kaseya incident. So, this is a ‘universal’ key, but only within the Kaseya sphere. Also, it doesn’t seem to hold any value for decryptor developers, so its publication doesn’t change a lot on that front either. For history, the key is: “OgTD7co7NcYCoNj8NoYdPoR8nVFJBO5vs/kVkhelp2s=”.