‘SitePoint’ Data Breach Ends up in a User Database Leak
- ‘SitePoint’ has had a data breach that escalated to user data access, exfiltration, and leak.
- The actors who got their hands on this data launched a crypto-themed phishing campaign.
- The platform admitted the incident now and reset all user passwords while also upping the character number requirement.
Hackers have breached ‘SitePoint,’ the Australian web developer-focused book publishing, forum, job finding, and newsletter distribution platform. The website was launched over two decades ago, and today it enjoys a big and vibrant community of programmers and IT professionals in general.
Unfortunately for the platform and its members, hackers have managed to gain access to a third-party tool the admins used for GitHub account monitoring, stole API keys from there, and eventually accessed the codebase and system.
The actors then proceeded to steal user data from the backend and then started distributing fake cryptocurrency giveaway emails to the members, making SitePoint appear as the sender. Many of the recipients reported this to the platform, realizing that they were being phished, so a subsequent investigation confirmed the breach.
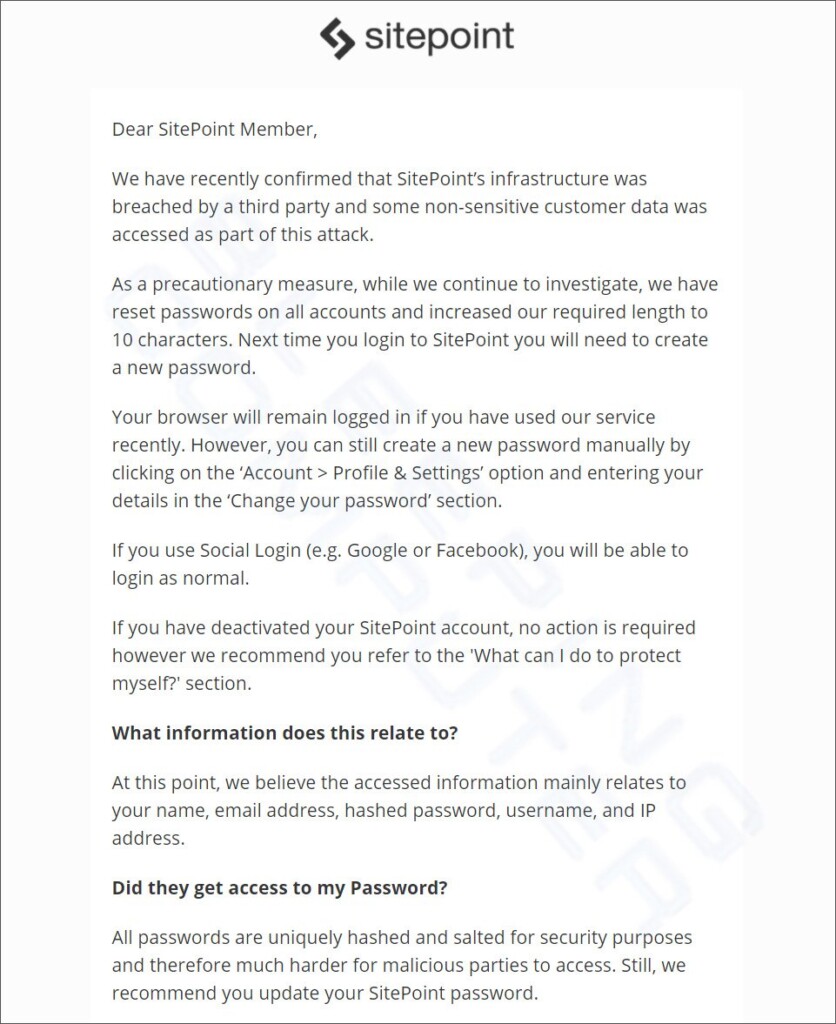
Now, SitePoint distributes real messages to its members, informing them that a third-party has accessed its infrastructure and that their accounts have been reset as a precautionary measure.
Users will have to use a new password that has a minimum length of 10 characters from now on. As for those already stolen, the platform says they were properly hashed, so it’s unlikely that the hackers will ever get to decrypt them. Still, though, to avoid any credential stuffing surprises elsewhere, you should perform resets to wherever you may be using the same password and email address.
SitePoint also offers a paid subscription that gives users access to hundreds of publications. However, as the platform clarified, they keep no financial information like credit card data on their systems, so that kind of details cannot have been leaked.
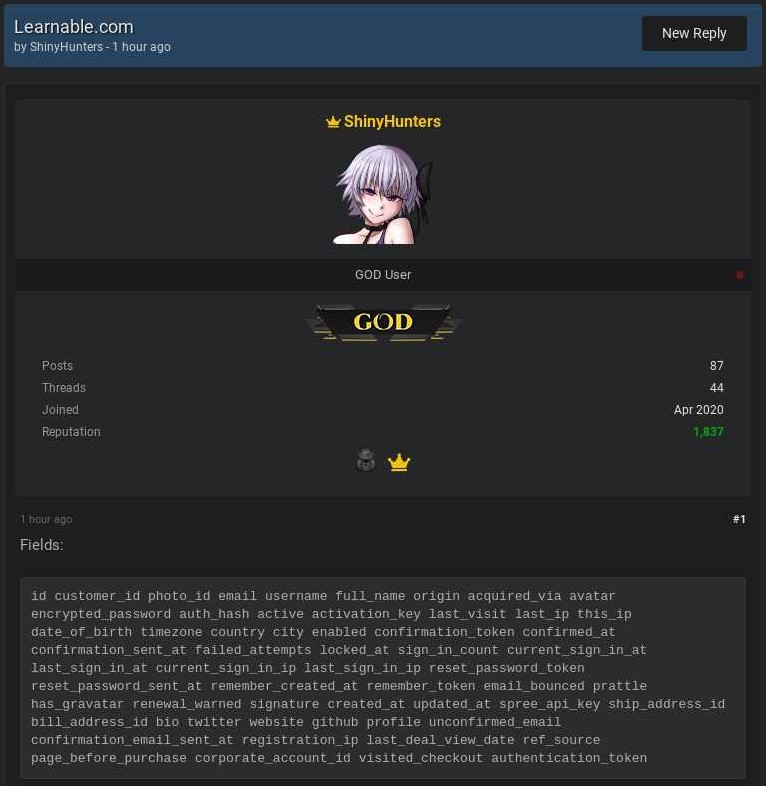
However, though, what has been leaked is a dataset that is being offered for free by the notorious data broker ShinyHunters, who defined 'Learnable.com' as the owner. Since that domain redirects to Sitepoint’s site, it is clear that the exfiltration that took place during the breach has already changed many hands in the underground.
The database consists of just over a million records and contains usernames, email addresses, bcrypted passwords, DoB, IP address, authentication tokens, user photo, and more.
Using KELA’s cyber-intelligence tools, we have found that the first post of this dataset came out on January 26, 2021, so it’s been ten days already. So, it’s possible that SitePoint knew about this and chose not to disclose the incident but admitted it only when the phishing emails started to reach users. Obviously, that was the second stage of the development, with other actors using the data shared by ShinyHunters to launch phishing campaigns.