SIM Card Flaw Under Active Exploitation Affecting Over a Billion People
- A previously undisclosed SIM card vulnerability is already under exploitation by surveillance firms.
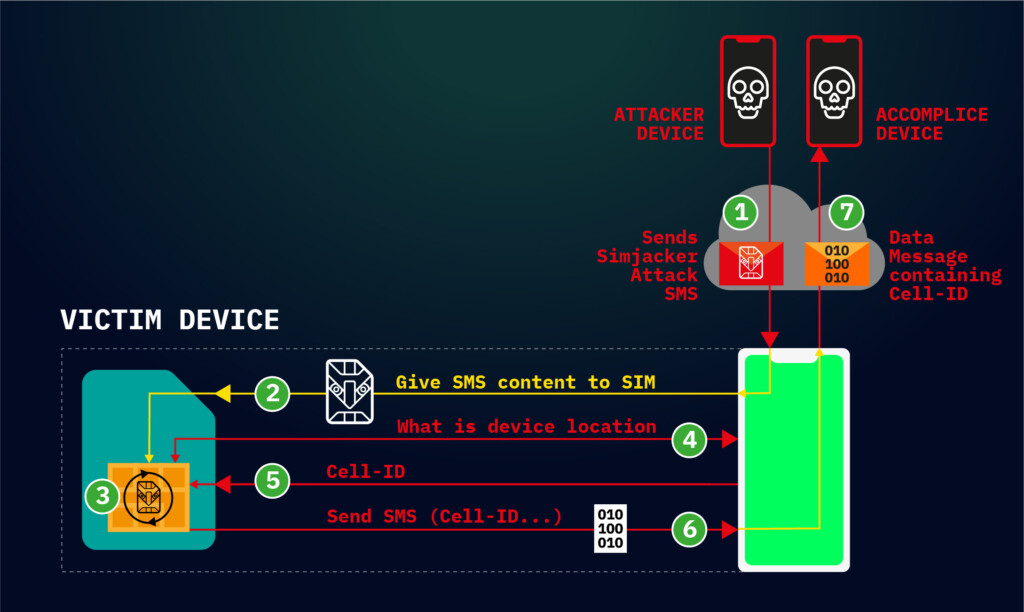
- The attack is called “Simjacker” and involves the sending of a special SMS message to the target.
- The GSM Association is already in the process of helping the operators incorporate the mitigations.
Researchers from Adaptive Mobile Security have discovered a vulnerability in SIM cards, which they call “Simjacker”. According to the report, the particular flaw is under active exploitation by surveillance companies who are engaged in espionage operations, usually supported and funded by governments. The main path of exploitation involves sending an SMS which contains a spyware-like code, which then instructs the SIM card of the phone to execute commands with the highest rights. Usually, the data that is exfiltrated via Simjacker is geolocational information, but the potential of the particular SIM attack is a lot wider.
The only equipment that the attackers need in order to carry out a successful Simjacker attack is a GSM modem which costs as little as $10. The information that is required is the victim’s phone number, and nothing else. From there, the actors may retrieve the device’s IMEI, GPS coordinates, dial numbers, eavesdrop by activating the microphone of the device, open web pages, execute downloaded files (like malware), render the device a member of a DDoS swarm, and even check the language settings or the battery levels. All of the above can take place without the user seeing any indication of the activity on the phone, and thus without realizing that something wrong is going on.
Source: adaptivemobile.com
What makes this SIM card flaw so special is the fact that it’s the first time we see the possibility of sending spyware code embedded within an SMS message. The other element that makes Simjacker unique is the fact that it uses the SIMalliance Toolbox (S@T) Browser software as an execution environment. This is compatible with a wide variety of UICC SIM cards, covering even eSIMs, as its protocol is currently being used by mobile operators in at least 30 countries. This corresponds to a population of approximately a billion people, which is the number of people who are currently vulnerable to Simjacker attacks.
So, if that is the case, then what can the users do about it in order to protect themselves? Unfortunately, not a lot. We rely on the GSM Association and the SIM alliance who determine the security and protection measures for SIM card manufacturers and protocols, and they are trying to address this vulnerability as soon as possible. The only thing that users can do is to contact their network provider and ask if they have configured their equipment to filter binary SMS messages that come from unauthorized sources. This will at least inform you if you're vulnerable or not. GSMA is already actively working with operators to help them address the SIM flaw by implementing the relevant mitigations.
Do you have a comment to make on the above? Please leave it in the dedicated section down below, or on our socials, on Facebook and Twitter.