‘Siloscape’ Is the First Known Malware to Target Windows Containers
- A novel cloud malware called ‘Siloscape’ is the first one to be targeting Windows containers.
- The particular malware opens a backdoor to a set of malicious possibilities, including cryptojacking and data exfiltration.
- The obfuscation in the code and operation of Siloscape is particularly high-level and very sophisticated.
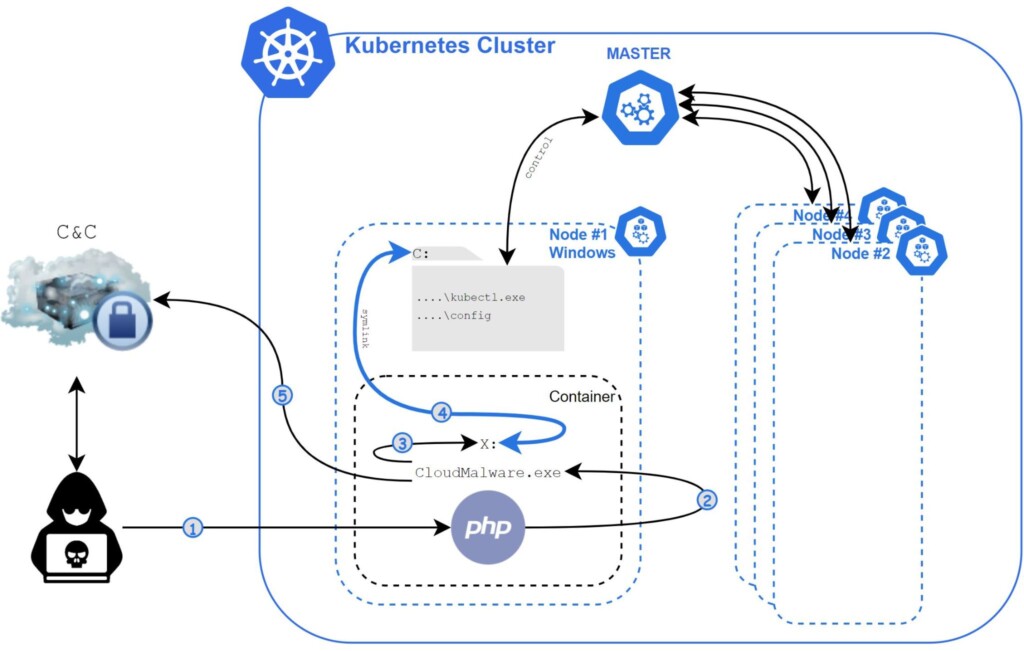
Researchers at Unit 42 have discovered the first known malware that is actively targeting Windows containers, naming it the ‘Siloscape,’ because its primary goal is to escape the container (silo) through a technique called “Thread Impersonation.” Siloscape is a pretty sophisticated malware that features heavy code obfuscation techniques. At the same time, it communicates with the C2 over Tor, which is an excellent way to evade detection and flagging from network traffic monitors. According to the Unit 42 report, Siloscape has been under active deployment for more than a year already, with 23 entities having been identified as victims.
The main trick pulled by Siloscape is to open a backdoor into poorly configured Kubernetes clusters in order to run malicious containers like cryptojackers, for example. Exfiltrating data from the compromised systems is also a frequent occurrence. To expand its presence in the cluster, the malware abuses the node’s credentials. As for the vulnerabilities that are used for initial access, these are known and published RCE flaws, with some even having a publicly available exploit.
Siloscape operates in a parasitic manner, trying not to harm the cluster - but instead, they maintain its presence and continue its malicious operation without being detected. To achieve this, it obfuscates everything, even simple API calls. Function and module names are obfuscated too and are deobfuscated only at runtime. The C2 password is decrypted through a pair of keys, one that is hardcoded into the binary and one that is supplied as a command-line argument. Each attack uses a unique compilation of the Soloscape binary, so it has a monadical pair of keys.
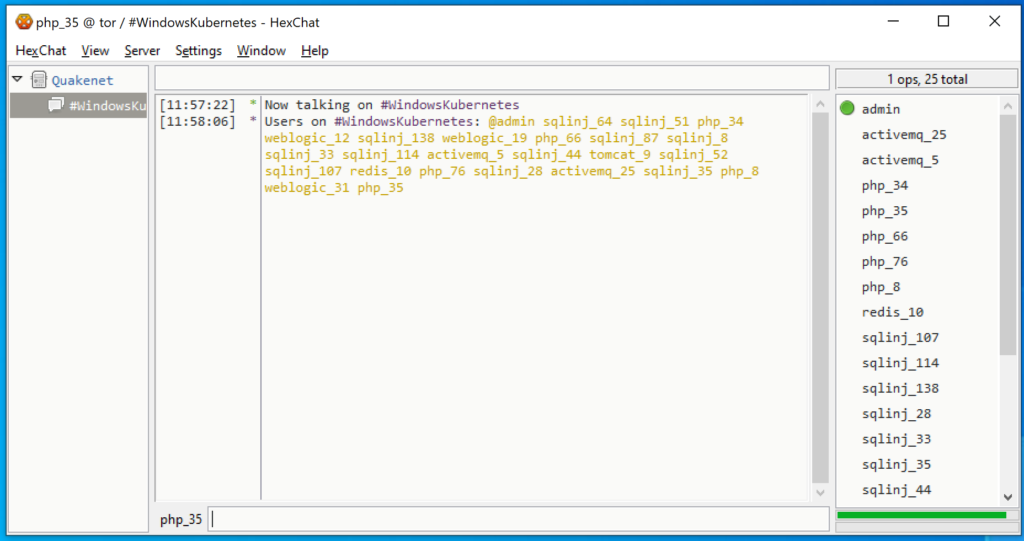
The Siloscape campaign is still pretty much active, even though the actors jumped to a new onion domain for their C2 communications after Unit 42 researchers were discovered while trying to figure out the status of the malicious operation. Based on a discrepancy between the number of active users on the C2 server and the #WindowsKubernetes IRC channel, the researchers concluded that the Siloscape malware is actually just a small part of a larger campaign.
In summary, we can say that Siloscape is a particularly nasty piece of malware because it isn’t limited to the typical resource-hijacking or DDoS tricks. Instead, it opens a backdoor that could be used for a wide range of malicious activities, so the threat is severe. Therefore, admins should secure their Kubernetes clusters properly by setting the node’s privileges to a level that doesn’t allow new deployments - and they should also use Hyper-V containers where possible.