SilkSpecter Scam Network’s 4,700 Fake Black Friday Shopping Sites Impersonate IKEA, The North Face, Lidl
- A new scam campaign targeting the e-commerce sector emerged, this time aimed at people looking to get a Black Friday deal.
- The extensive cluster of fake websites that seem legitimate includes domains mimicking Makita, Bath & Body Works, and more.
- SilkSpecter also integrates Google Translate to localize user language and utilizes trusted payment processor Stripe.
A new threat has emerged in the domain of e-commerce security as a financially motivated Chinese threat actor, dubbed "SilkSpecter," orchestrates an elaborate fraud campaign identified by EclecticIQ.
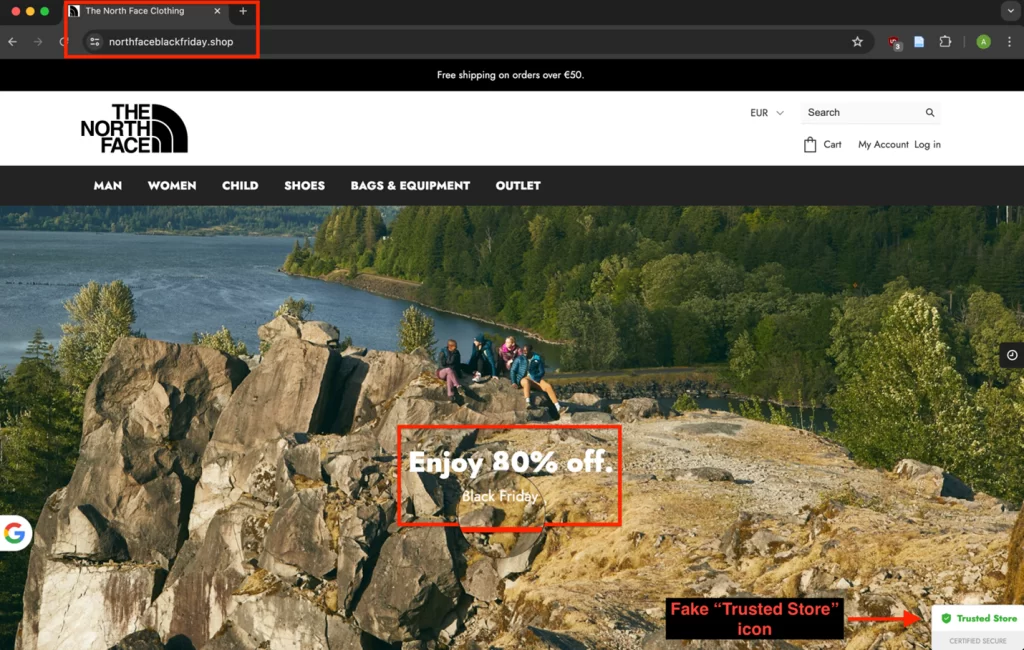
The operation leverages approximately 4,700 fake online stores to siphon off payment card details from unsuspecting shoppers, primarily in the U.S. and Europe. These fraudulent sites mimic well-known brands such as The North Face, Lidl, Bath & Body Works, L.L. Bean, Wayfair, Makita, IKEA, and Gardena.
The SilkSpecter operation began in October 2024, strategically timed to coincide with increased consumer spending.
The origins of SilkSpecter are believed to be Chinese, inferred from several indicators, including the use of Chinese IP addresses and ASNs, Chinese domain registrars, linguistic evidence in site code, and prior utilization of the Chinese SaaS platform "oemapps" before switching to Stripe.
They target bargain hunters specifically by incorporating the 'Black Friday' string into domain names of convincingly-crafted sites, often using top-level domains like '.shop,' '.store,' '.vip,' and '.top.' While these domains may lend an air of legitimacy, they are not commonly used by reputable brands, which should raise red flags for discerning consumers.
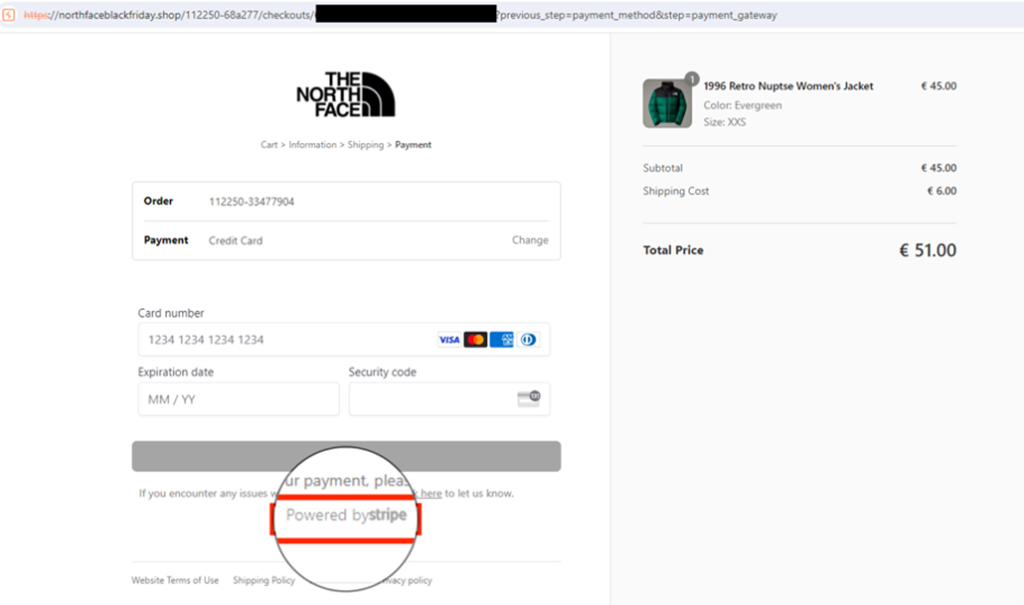
SilkSpecter goes a step further by integrating Google Translate to localize the language based on the user's location, making the sites appear more credible. They also utilize Stripe, a trusted payment processor, to handle transactions, which adds another layer of perceived authenticity.
In addition to processing payments, the phishing sites employ tracking tools such as OpenReplay, TikTok Pixel, and Meta Pixel. These tools enable SilkSpecter to analyze visitor behavior, potentially refining their tactics for greater success.
Upon attempting a purchase, users are directed to a payment page where they are prompted to enter credit/debit card information. A phone number is also requested, which EclecticIQ suggests could be used for subsequent phishing attacks targeting two-factor authentication processes.
To mitigate risk, Black Friday shoppers are advised to transact exclusively through official brand websites, avoiding links from ads, social media posts, or promoted search results. Additionally, they should activate all available security measures on financial accounts, such as multi-factor authentication, and vigilantly monitor their account statements.
In August, security researchers discovered a campaign that targeted Facebook users via a scam e-commerce network of 608 fake websites orchestrated by a single threat actor or group.