SideWinder APT Group Evolves Tactics, Deploys New ClickOnce Malware
- Targeted campaign: SideWinder APT launched a multi-wave phishing campaign targeting diplomatic entities in India, Sri Lanka, Pakistan, and Bangladesh.
- Novel infection chain: The campaign’s infection vector involves malicious PDF files and the Microsoft ClickOnce application deployment technology.
- Espionage malware: The goal is to deploy custom espionage tools, including the ModuleInstaller and StealerBot malware, for intelligence gathering.
A new and sophisticated espionage campaign attributed to the SideWinder APT group has been identified targeting governmental and diplomatic entities across South Asia. The campaign, which ran in multiple waves throughout 2025, showcases an evolution in the group's tactics, techniques, and procedures (TTPs).
Analysis of the ClickOnce Malware Infection Chain
While SideWinder has historically relied on malicious Microsoft Word documents, this latest operation introduces a novel infection chain based on malicious PDF files and Microsoft's ClickOnce application framework, according to Trellix threat intelligence.
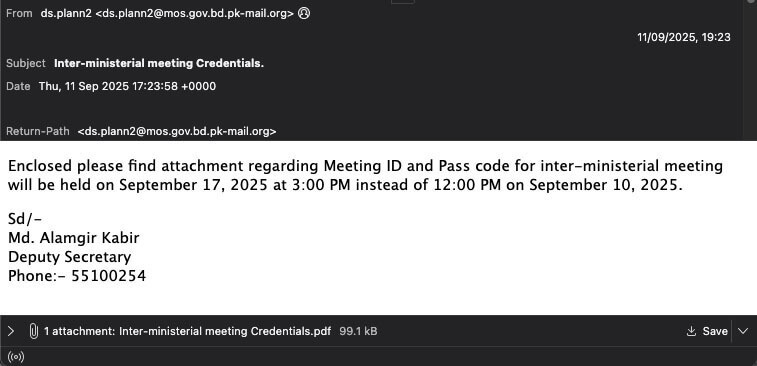
The cyberespionage campaign begins with spear-phishing emails containing lures tailored to specific targets, such as documents titled "Annual Transfers of Officers" or "India-Pakistan Conflict."
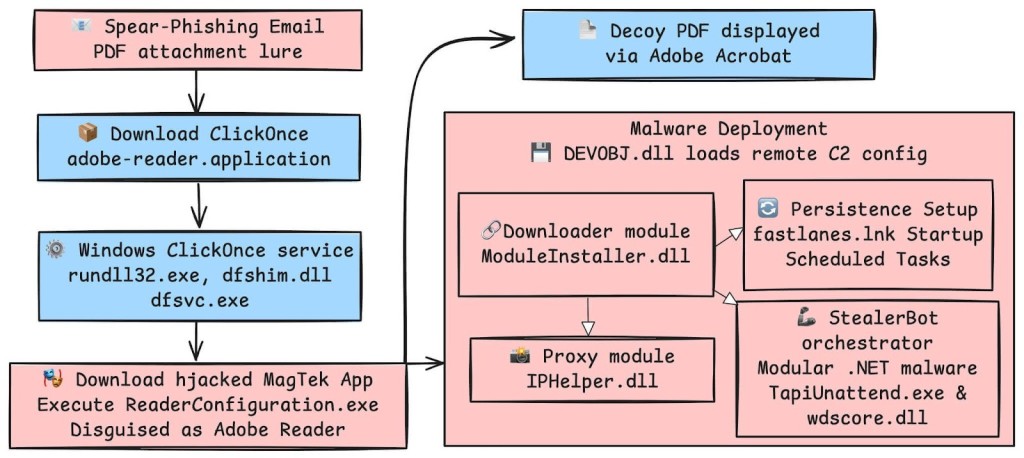
The attached PDF files prompt the victim to download a fake Adobe Reader update. This action downloads and executes a malicious ClickOnce malware application.
The attackers cleverly abuse a legitimate, signed application from MagTek Inc., side-loading their own malicious DLL (DEVOBJ.dll) to bypass initial security checks.
This first-stage payload decrypts and executes a .NET loader, which in turn downloads the main "ModuleInstaller" component. This installer then deploys the final payload, "StealerBot," using process injection to remain fileless and evade detection.
Geopolitical Espionage and Infrastructure
SideWinder’s infrastructure demonstrates a high degree of operational security. The command-and-control (C2) servers utilize geofencing to restrict payload delivery only to IPs from the intended target regions, as the server would respond with 404 content to users outside South Asia.
The campaign uses lookalike domains mimicking government institutions to add a layer of legitimacy to their phishing attempts.
Trellix attributes this activity to SideWinder with high confidence based on the specific victimology, the use of proprietary malware like ModuleInstaller and StealerBot, and overlapping infrastructure with previously documented attacks.
The campaign's focus on diplomatic and government targets underscores its objective of regional espionage.
In other recent news, another cyberespionage campaign targets global organizations in the government, financial, and industrial sectors with custom APT implants, including a C++ modular backdoor and a .NET implant.
This month, the Phantom Taurus APT targeted government and telecom organizations in a NET-STAR malware espionage campaign.