SharePoint Exploits Impact 100 Entities, Google Says Some Hacks Are Tied to Chinese Hackers
- What happened: A new SharePoint RCE vulnerability chain exploit affected almost 100 entities.
- Victim impact: Most victims were in the U.S. and Germany and included government organizations.
- Campaign attribution: One or more attackers could have orchestrated the attacks, with some attributed to a China-nexus threat actor.
A large-scale exploitation of a new SharePoint remote code execution (RCE) vulnerability chain in the wild is being used to compromise on-premise SharePoint Servers worldwide. Recent cybersecurity reports indicate that almost 100 victims have been identified to date, and some hacks were tied to Chinese threat actors.
Exploit Victims
Netherlands-based cybersecurity firm Eye Security made the discovery and published a report on July 19. Nearly 100 victims were found – most in the U.S. and Germany – revealed Vaisha Bernard, co-owner of the security company, who declined to identify the impacted entities that include government organizations.
"It's unambiguous," Bernard said via Reuters. "Who knows what other adversaries have done since to place other backdoors."
Eye Security scanned more than 8,000 SharePoint servers worldwide, with evidence of dozens of compromised servers. Silas Cutler, the principal researcher at Censys, mentioned seeing between 9,000 and 10,000 vulnerable instances accessible from the internet.
Details of the Hack
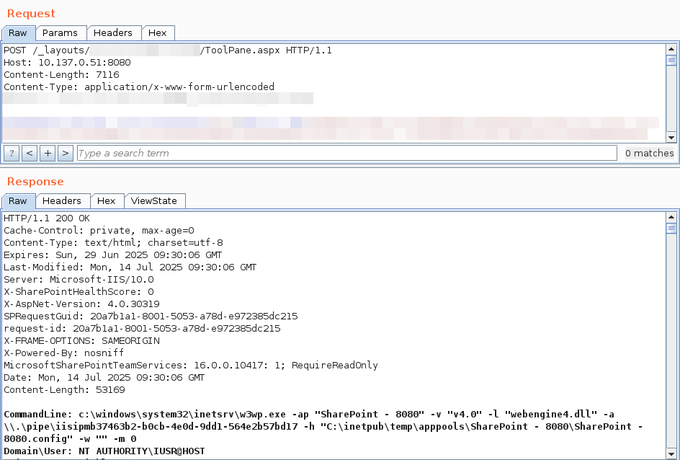
Microsoft issued a critical alert regarding two new SharePoint Server vulnerabilities, CVE‑2025‑53770 and CVE‑2025‑53771, following earlier exploitation of related flaws, CVE‑2025‑49704 and CVE‑2025‑49706, used in the ToolShell exploit chain.
The latter were recently exploited despite being fixed via a Patch Tuesday advisory.
CVE-2025-49706 & CVE-2025-49704 were exploited together in a ToolShell attack – a critical SharePoint RCE (remote code execution) exploit chain. This exploit was also demonstrated a few days ago on X (formerly Twitter).
Palo Alto Networks Unit42 detailed the exploit on GitHub, stating that CVE-2025-49704 and CVE-2025-49706 allow unauthenticated attackers to access restricted functionality; however, chaining them enables malicious actors to execute arbitrary commands on vulnerable SharePoint servers.
CISA added the vulnerability to its Known Exploited Vulnerabilities (KEV) catalog on July 20, 2025, and says the ToolShell exploit allows full SharePoint content access to unauthenticated users, including file systems and internal configurations.
Who Is Behind the Hack
According to Reuters, Google tied some of the hacks to a "China-nexus threat actor," and another researcher considers that a single hacker or set of hackers could be behind the attacks.
Mayuresh Dani, Security Research Manager at Qualys Threat Research Unit, believes a single sophisticated threat actor could have orchestrated the campaign “based on the fact that these attacks started within a week (~72 hours) of being publicly disclosed.”
China-linked Silk Typhoon (also known as HAFNIUM) has a known history of exploiting Microsoft enterprise software, including SharePoint and Exchange. Other threat actors, such as Iran’s MuddyWater, have also targeted collaboration platforms, but are not linked to the current campaign.
In March, Silk Typhoon exploited remote management tools using leaked corporate passwords. In July 2025, U.S. authorities arrested a Chinese state-sponsored hacker affiliated with the group responsible for the 2021 HAFNIUM Microsoft Exchange attacks.
Cybersecurity Experts Advise
Dana Simberkoff, Chief Risk, Privacy and Information Security Officer at AvePoint, urged shifting focus to proactive security posture management and building resilient environments through cultural readiness and shared responsibility for data protection.
Organizations “need to implement data minimization strategies, robust lifecycle management, and continuous DSPM to identify and mitigate risks before attackers can exploit them,” Simberkoff says.
“The fact that hackers gained access to cryptographic keys that could allow re-entry even after patching highlights why surface-level fixes aren't sufficient when the underlying security architecture lacks depth.”