Sextortion Scams Evolve to Avoid Email Gateway Detection
- Sextortion blackmail is on the rise, targets the education sector.
- The attackers ask for Bitcoin payment in exchange to holding onto "compromising footage".
Sextortion blackmail scams are becoming more and more common these days, with the education industry taking the brunt of the attacks, a new Barracuda Network study shows.
While these type of scams are nowhere close to being new, it seems they are now more sophisticated than ever before and are bypassing email gateways quite frequently. This means that, if before they'd land in your spam box, or get pushed directly into the recycle bin by email clients, now they're getting a front row seat in your inbox.
What's causing the change? Well, the blackmail is no longer "mass-produced," they're no longer used as part of large-scale spam campaigns. Instead, they're customized for their targets, they no longer contain malicious links or attachments and they use spoofed email addresses, which makes things a tad more complicated for email protection systems.
In most sextortion scams the attackers use a harvested email address and password to take advantage of the victim's fears in a threatening email. The attackers also spoof their victim's email address, pretending to have access to it, which makes things that much more terrifying. They demand to be paid in Bitcoin so they don't publicly release footage with the victims that were supposedly captured with their computer camera while visiting porn sites.
The emails come from accounts on Office 365 or Gmail that was already compromised, while the subject alerts to security issues like "your account has been hacked" or mentions passwords picked off during data breaches.
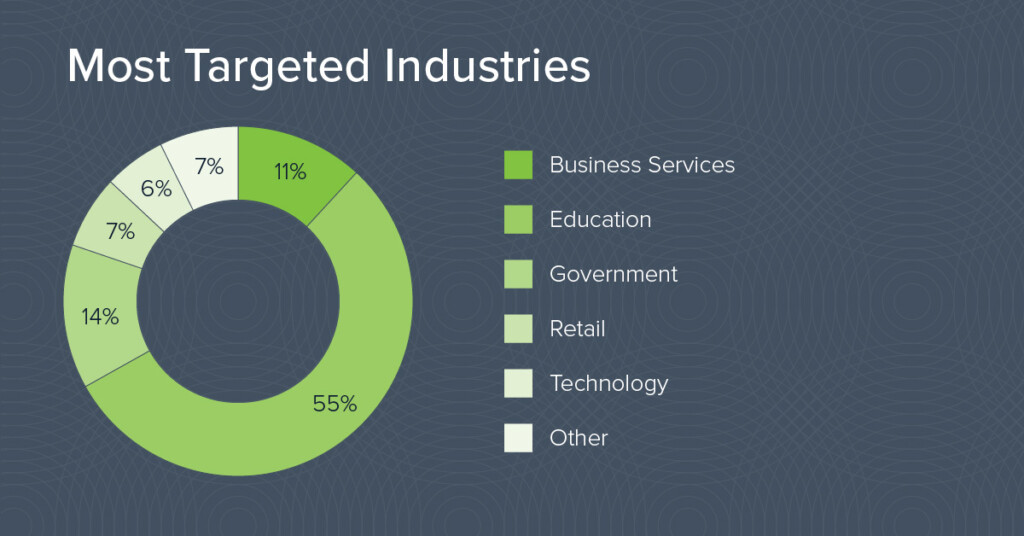
The study found that the industries that were most frequently targeted by sextortion and blackmail were Education and Government. Educational organizations have a lot of users, some with very young people that may not be too well-informed about security practices or how to seek help and advice. Plus, given the nature of the emails, they may also be reluctant to actually reach out to anyone for help, which makes them the perfect victims.
Courtesy of Barracuda Networks
So, what do you need to do if you get one of these emails? Well, Barracuda Network's Asaf Cidon, VP of email security, says it's best to ignore them. "And make sure that you are not using the password that the attackers mention in the email to log in to any online services. The attackers typically use passwords that were compromised in one of the massive breaches. So it's a good idea to make sure you aren't using these passwords anymore," he says.
Barracuda Networks mentions four ways to protect against sextortion scams such as getting AI-based protection and account-takeover protection, proactively investigate the email accounts to detect messages about password changes or security alerts, and get some security-awareness training.
While the scare you can get when receiving such an email is understandable, your accounts are probably not at risk. "If the password appearing in the email is actually a password the recipient still actively uses, I'd recommend to immediately reset it," Cidon adds.
Have you ever received such an email? Let us know what happened by dropping a comment in the section below. Share the article online to help others, and follow TechNadu on Facebook and Twitter for more tech news, guides, and reviews.