New Sextortion Campaign Uses Nest Camera Footage to Defraud People
- Fraudsters are going the extra mile to convince their victims that they have infected their phones with malware.
- They are presenting Nest camera footage as the result of their hacking work, and they claim to send emails from stolen accounts.
- Thousands of emails have circulated since the start of the year, asking people to pay $600 in Bitcoin.
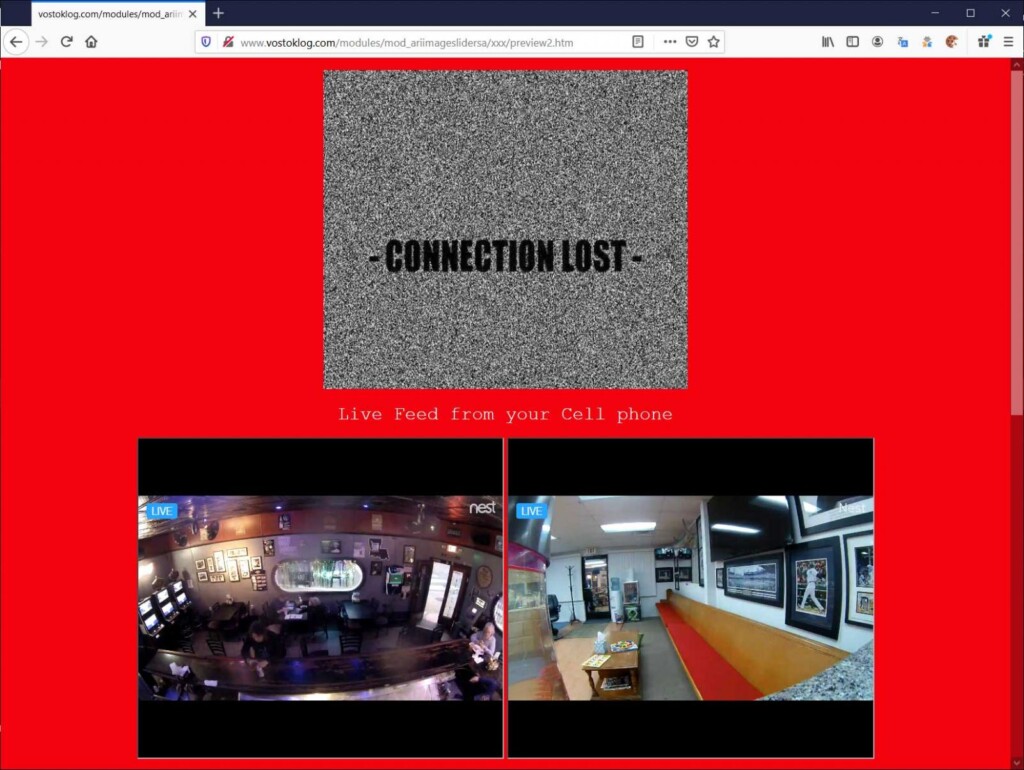
Internet users have been reporting a new type of a sextortion campaign that has been going on since the start of 2020, and which has now been confirmed by Mimecast researchers. Apparently, malicious actors are presenting publicly available Nest camera footage to their targets, trying to convince them that this is the product of skilled hacks. Moreover, the fraudsters are warning the target that they have a video of them during personal moments, threatening to make it public if they won’t pay 500 Euros in Bitcoin. Of course, none of the claims stand, so here’s a detailed analysis of the campaign to help you stay calm.
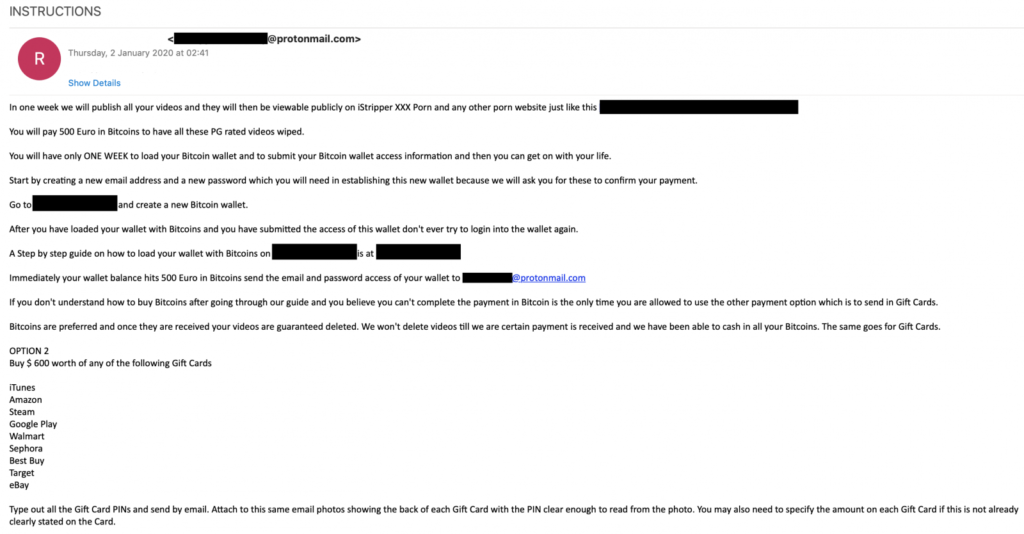
The first thing that you’ll get from these scammers is an email claiming to come from hackers. The sextortion actors make the bold claim of having planted malware on your phone which is able to activate the front camera and send footage back to them. To make the situation urgent, the actors are giving the recipient of the email a week to respond to their threat of making their personal footage public by uploading it onto various porn websites. While they say that they have been monitoring you for more than 11 months, the link that they provide in the email message points to an unrelated live video feed from Nest cameras.
Source: Bleeping Computer
These cameras are publicly accessible anyway, either by a configuration mistake or on purpose, but the actors like to present them as the result of their skilled work. If the recipient bites the hook, they will be offered the option to pay EUR 500 ($600) in Bitcoin or buy an equal amount in gift cards from iTunes, Amazon, Steam, Google Play, Walmart, Sephora, Best Buy, Target, and eBay. Mimecast researchers have also noticed a case where the actor pushed harder, with a deadline of four days and a demand of EUR 800.
Source: Bleeping Computer
To add some salt in their trickery soup, the actors are urging the recipient of the email to send a request to another address in order to receive the instructions. This is allegedly because the first email comes from a hacked email account, while the second one is a "secured" ProtoMail address. During the first week of 2020, the sextortion campaign sent out 1687 email messages, but the victim count is unknown. Hopefully, the recipients were composed and calm and didn’t pay anything to the scammers.