Scranos Rootkit-Enabled Spyware Breakes Out Across the World
- Scranos has broken free from China and is already actively infecting machines from all around the globe.
- This powerful malware combines many components that are dedicated to different roles.
- Scranos is still in the development phase, improving the best components while continually testing new ones.
The Bitdefender Cyber Threat Intelligence Lab has published a report on Scranos, a cross-platform rootkit-enabled spyware operation that has left the constraints of the Chinese territory where it has been under testing until now, and broke out to infect users from all around the world. Bitdefender believes that the Scranos operation is still taking its form, as various new components are tested and evaluated on targets that have already been compromised. Those who are considered to be working well enough receive improvement updates, but the general picture is a multi-dimensional, multi-functional malware that can do the following:
- Steal Steam account login credentials
- Steal payment accounts from Facebook, Amazon and Airbnb websites
- Exfiltrate browsing history
- Download and execute any payload
- Subscribe users to YouTube video channels and silently display ads via Chrome
- Inject JavaScript adware in Internet Explorer, Chrome, and Opera
- Manipulate Facebook accounts by sending friend requests to other accounts, and then send phishing messages containing malicious APKs
- Extract cookies and steal login credentials from virtually all major browsers, including MS Edge and IE, Chrome and Chromium, Firefox, Opera, Baidu Browser, and Yandex
image source: labs.bitdefender.com
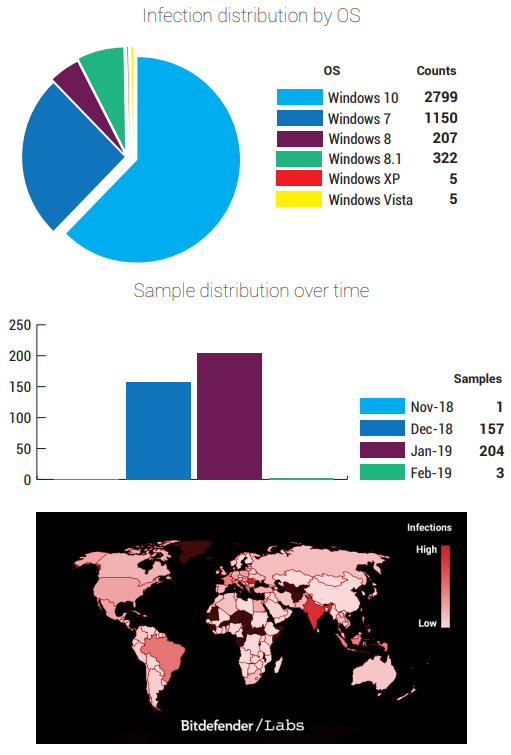
The primary way of infection and spreading for Scranos is through applications that have been “Trojanized”. As usual, cracks for pirated applications like costly professional tools and games are the main channel, but the extent of infection covers hardware drivers, video players, e-book readers, and even AV products. The telemetry data presented by Bitdefender portrays a global epidemic that has mainly hit India, Brazil, France, Italy, and Indonesia. As for the operating systems, most of the infections concern users of Windows 10 and 7, as expected. The samples that were analyzed use a valid digital code-signing certificate that was initially issued to a Shanghai-based consulting organization and has not been revoked yet.
image source: labs.bitdefender.com
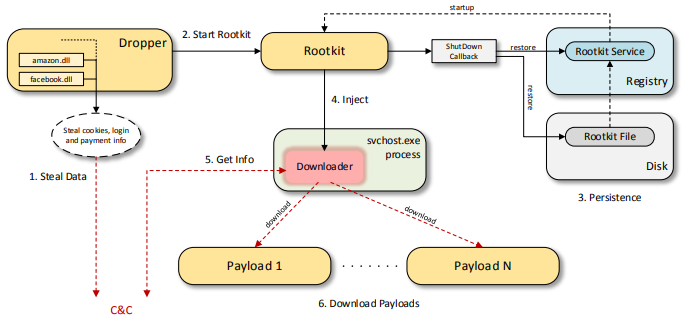
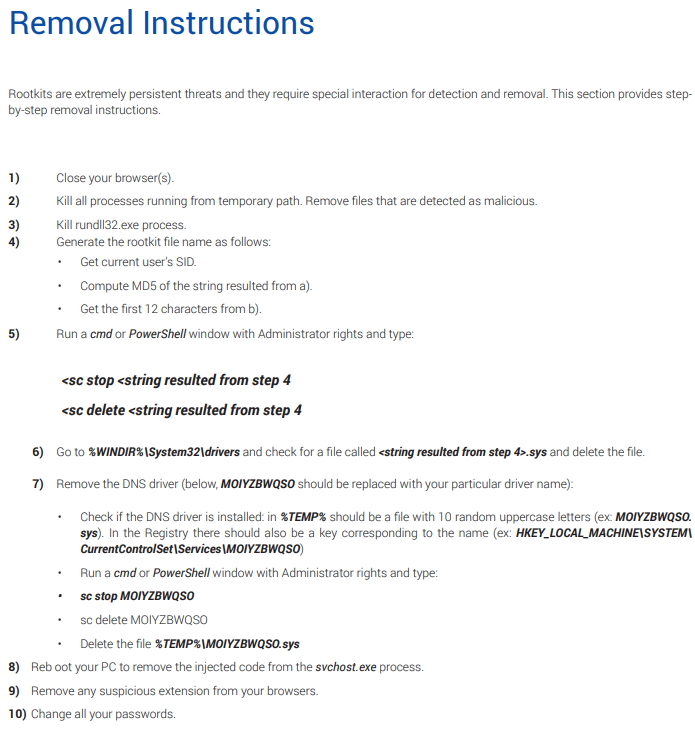
The operation of Scranos is so extensive and powerful, Bitdefender’s report counts 48 pages, covering the details on how its various components work, infecting, searching for specific targets, injecting code, communicating with a well-organized C&C network, and how multiple variants in different C&C addresses combine to create an affiliated network of third parties who are all working together against their victims. If you have been infected by Scranos, you can follow the “removal instructions” as shown below, or on page 35 of the report.
image source: labs.bitdefender.com
Care to share your views on the above? Feel free to do so in the comments section below, and help us warn more about the dangers of Scranos by sharing this post through our socials, on Facebook and Twitter.