A Schneider MV Control Substation Has Been Vulnerable for Eight Years Now
- An old remote terminal unit from Schneider Electric has been vulnerable to remote access since 2012.
- The vendor knew about this but decided to address the flaws only for the reporting operator.
- The practices have changed today, but this product and its vulnerabilities got lost in time.
The Schneider Easergy T200 RTU, a medium voltage substation that is still listed on the vendor’s website, has reportedly been vulnerable for over eight years now. To be more precise, security consultants ‘PenTestPartners’ reported a serious flaw they found back in 2012 to Schneider via an operator who was using the device. Considering that industrial control equipment like the T200 RTU stays in service for decades, this is an interesting and also critically important report.
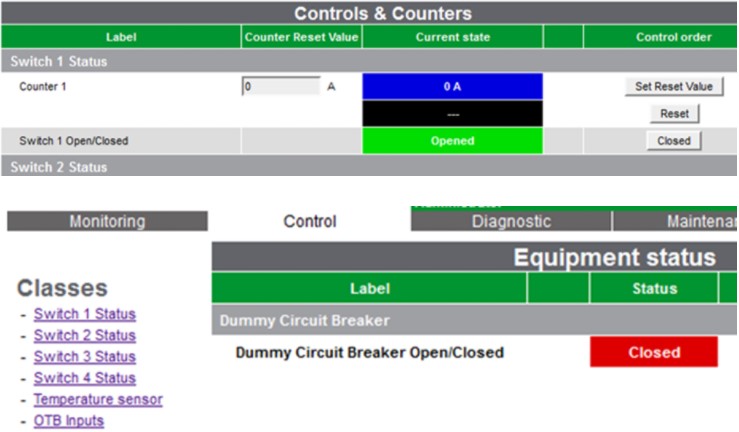
The particular device can be used to open and close power switches on home and commercial electricity networks. It features an integrated cellular data modem (3G), and it also supports radio, Ethernet, and private line connections. As the researchers discovered back in 2012, common APN configuration errors or plain lack of knowledge on the specifics of secure configuration could very easily lead to the device being exposed on the public internet.
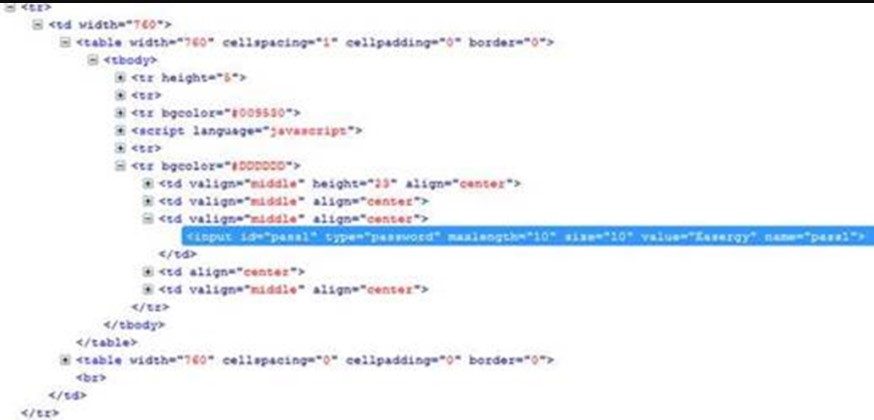
With no SSL protecting the login and the device’s default credentials being “easergy | easergy,” a third party could access it. The credentials are also conveniently stored in plaintext in the HTML. To make matters worse, the remote terminal unit system allows changing the switch status parameters without checking for authorization. Additionally, one can generate service request tickets in the web interface through XSS, as there’s no validation here either.
All of the above issues were shared with Schneider by the operator eight years ago. Oddly, the vendor decided to offer a fix to the particular operator but not make this universal.
Schneider thought they would only take action against the identified flaws on a case by case basis, and only for operators who requested this fix and paid for it. Thus, there has been no firmware update circulation that addressed the security bugs in the last eight years, so those using the Easergy T200 RTU are still vulnerable.
Of course, much has changed in remediation strategy since 2012, and Schneider Electric is now handling reports about security flaws a lot differently. As the reporter of this somewhat weird story suggests, their early reports got lost down the cracks of an immature disclosure program. Then, time passed, and nobody thought about the Easergy T200 RTU again, which lead to having these flaws for so many years.
If you are a user of the particular product, update to the latest available firmware, which is from 2018. It may address at least some of the aforementioned issues. Also, you can check Schneider Electric’s official recommended cybersecurity practices here.