Scammers Are Tricking People With Fake Software Renewal Notifications
- Scammers are using a simple yet effective trick, sending out fake notifications of auto-renewals.
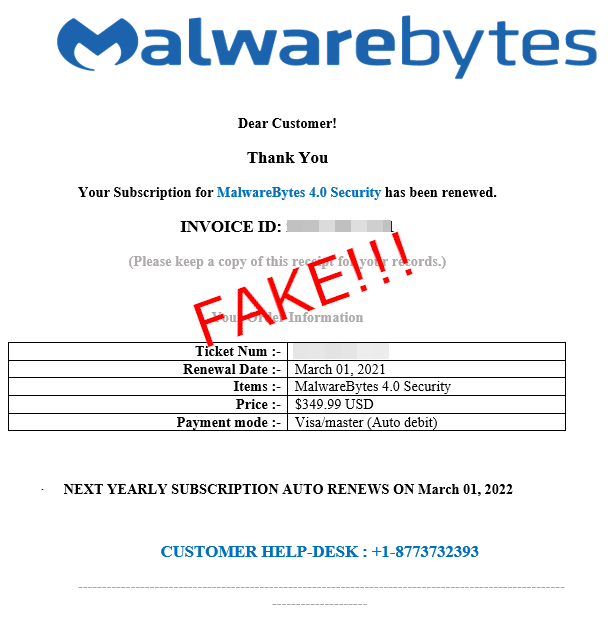
- The amounts presented in the phony invoices are absurd to convince the recipient to call a fake support line.
- The agent then installs RATs and creates more fake warnings, hoping to trick the victim into paying more.
There’s an ongoing scamming campaign involving fake software subscription renewal notifications. According to Malwarebytes researchers who have been following the campaign closely, this theme is used for the last couple of months. Unfortunately, a significant portion of the recipients of these fake notifications are getting tricked.
The actors are sending an invoice for a popular software product, supposedly charging the recipient an absurd amount for a renewal of the subscription. The notification includes a “customer help desk” number, which the scammers hope that the victim will use in order to dispute the “auto-renewal.” In an example using Malwarebytes Security 4.0, the scammers present victims with a charge of $349.99.
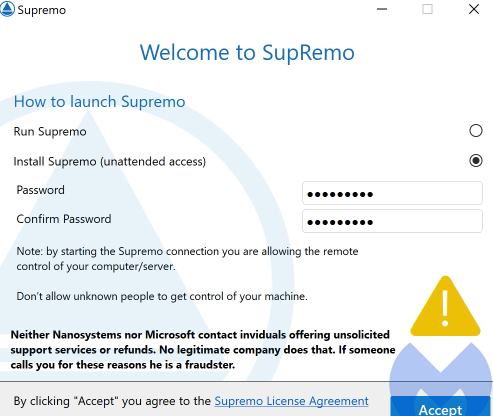
If the victim calls, the scammers pretend that a technician will have to access their computer to ensure that the software in question is uninstalled so that a refund can be granted. This is done through TeamViewer, which the victim is convinced to install for the crooks. If that happens, the scammers will simply proceed by installing more remote access tools like SupRemo.
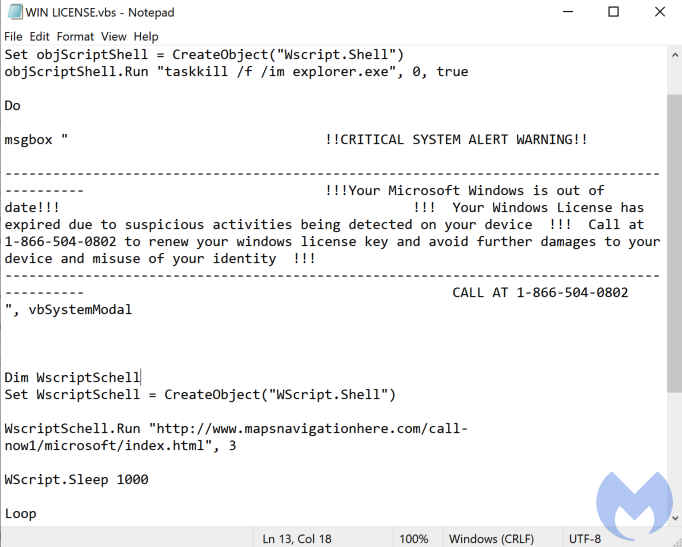
What the scammers do from then on is to write more notices and warnings on notepad, lock up the machine by using the SysKey utility, and generally ensure that the victim is constantly met with bogus alerts about fabricated threats and problems. All of that is done to convince the victims to pay them more money to supposedly clean the system, or uninstall the threats, or whatever. As long as the victim pays, the scamming continues.
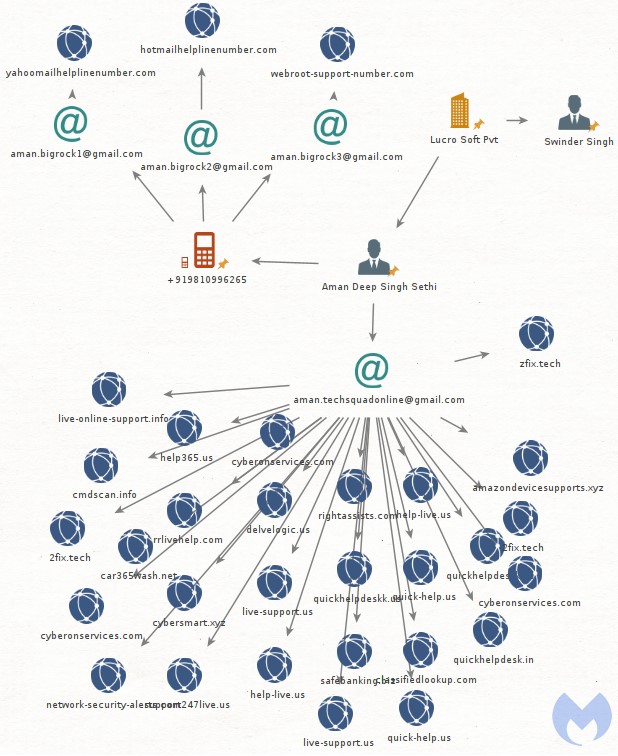
Malwarebytes was able to dig deeper to figure out who these scammers are and managed to identify the registrant of a malicious domain used for dropping the RAT tool, named Aman Deep Singh Sethi. Also, an associate named Swinder Singh was identified through a phone number, and eventually, a New Delhi-based company called 'Lucro Soft Pvt' was unearthed.
The researchers figured that the scammers had been active since at least 2015, while Lucro Soft was established in 2018, possibly to help them justify the income somehow. The identified infrastructure was mapped and is now actively blocked by Malwarebytes and all the security solutions that are receiving their indicators of compromise reports. The scheme has been uncovered, and the actors’ were exposed, so normally, they will stop all activity now.