Scam Trend Sees Attackers Bypass Two-Factor Authentication with Phishing and OTP Bots
- Two-factor authentication (2FA) is a prerequisite security feature for protecting users’ accounts, but scammers can exploit it.
- Most 2FA varieties use one-time passwords (OTPs) sent via text, call, email, or push notification.
- A relatively recent online scam trend steals OTPs and circumvents 2FA using phishing and OTP bots.
A new report details how online scammers can obtain OTPs that victims receive via text message, voice calls, email, instant messages, or mobile app push notifications via complex hacks with multiple stages. These include phishing and OTP bots, typically managed via a special browser-based panel or a Telegram bot.
Attackers focused on social engineering use these OTP-intercepting tools with credentials from personal data leaks, datasets purchased on the Dark Web, or phishing websites, for instance. These credentials and at least a phone number are enough to begin the operation.
The schemes debut by using the credentials to sign into the target’s account, and the owner then gets a code. Using a prepared script, the OTP bot calls the victim to make them disclose the verification code by entering it on their phone during the call. The administration panel or a Telegram bot steals the OTP, which ends up with the attacker.
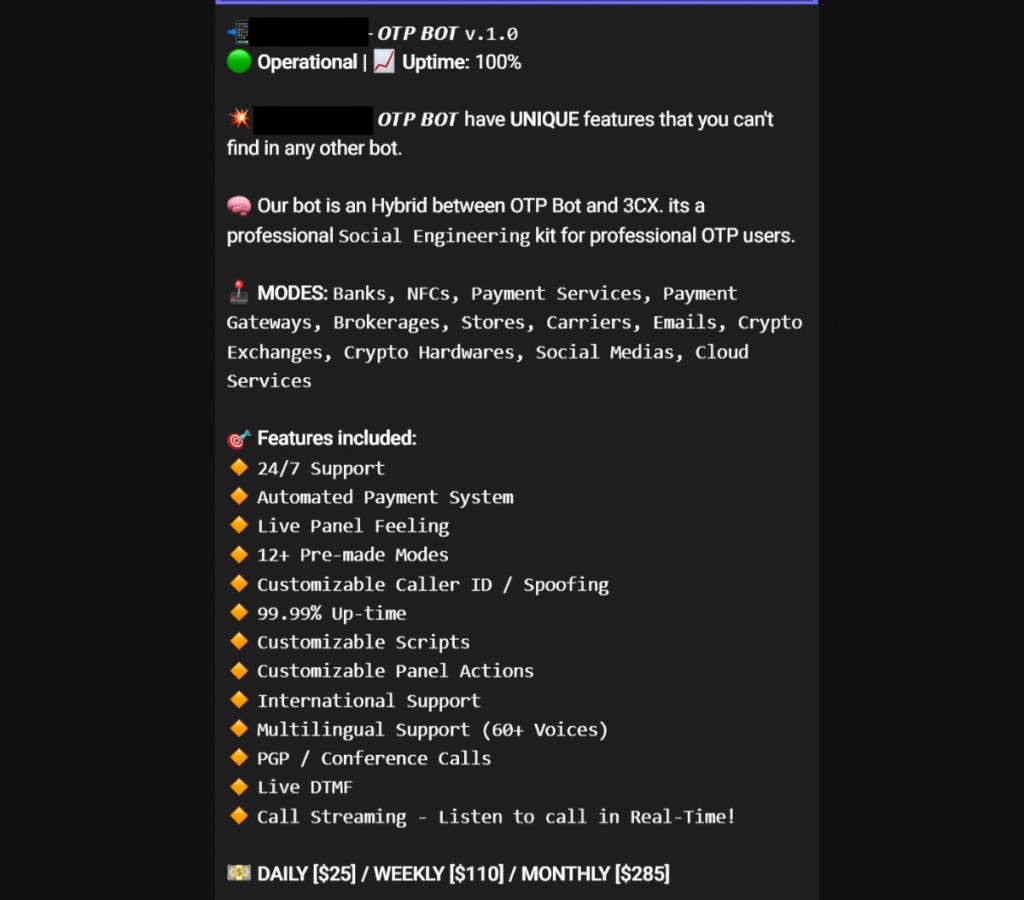
Bot developers compete on the Dark Web to sell the most “full-option” bot, as their functionalities range from one script targeting an organization's user to a highly customizable configuration with many scripts that let scammers create a whole bot call center.
The OTP bot’s key task is to call the victim since verification codes are only valid for a limited time and a phone call is more effective. Some OTP bots have over a dozen features including scripts in a variety of languages, female as well as male voices, and phone spoofing.
Would-be attackers can buy a subscription via cryptocurrency only. To set up their first call, the scammer selects what kind of organization they want the bot to impersonate, and the subscription offers options such as banks, payment systems, online stores, cloud services, delivery services, crypto exchanges, and email services.
The scammers can personalize the calls with information they hold, such as the victim’s name and the last four digits of the victim’s bank card number, and advanced options like spoofing, language, AI-generated voice type, and first sending a text message to announce the victim should expect a call from an employee of a certain company. Moreover, some of these bots support custom scripts the scammer can import.
Some typical steps of multi-stage phishing attacks include targeting the victim with a message from a seemingly legit company asking for an account update via a link that redirects to a phishing website, which collects the credentials the victim enters. The admin panel is used to display an OTP entry form on the phishing site.