Salesforce Data Stolen via Third-Party Gainsight, ShinyHunters Claim Breach, Announce ‘Almost 1,000’ Victims
Key Takeaways
- Incident cause: Hackers exploited a third-party Salesforce integration via Gainsight-published applications, enabling unauthorized access to customer data.
- Attack vector: The incident was not a breach of Salesforce's core platform but rather an OAuth token attack on Gainsight.
- Threat actor: The activity has been linked to the ShinyHunters group, which alleges the victim list comprises “almost 1,000” organizations.
Salesforce has identified and is investigating a data theft campaign targeting its customers through a compromised third-party integration. The incident stems from unusual activity detected in Gainsight-published applications, which customers install and manage to connect to their Salesforce environments.
In response, Salesforce has revoked refresh tokens associated with the affected Gainsight applications to mitigate further risk. Gainsight’s September investigation confirmed they suffered a data breach due to stolen OAuth tokens linked to Salesloft Drift.
Salesforce Gainsight Breach Attribution
The company has clarified that this was not a vulnerability within Salesforce's core platform. Instead, the malicious activity is attributed to the app's external connection to Salesforce, which threat actors exploited to gain unauthorized access to certain customer data.
The attack was allegedly carried out by the ShinyHunters cyberattack group, which leveraged a consistent playbook: compromising a vendor, stealing OAuth tokens, and using those tokens to access data in integrated platforms.
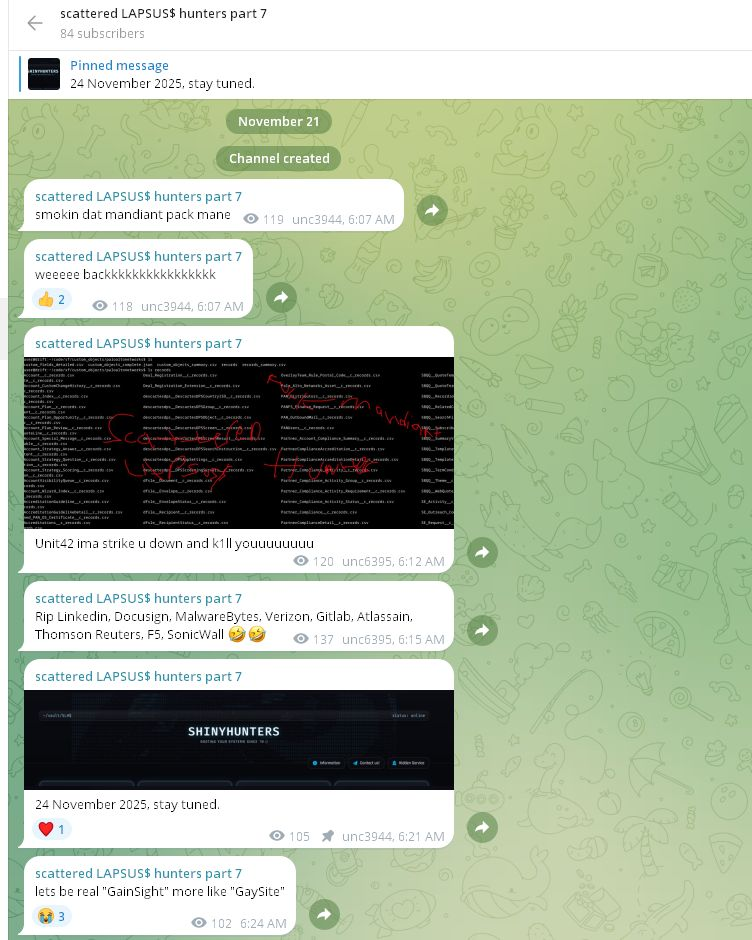
The ShinyHunters group (also part of the Scattered LAPSUS$ Hunters collective) has previously targeted similar SaaS ecosystem vulnerabilities. On a Telegram channel, the collective announced the launch of their RaaS platform for November 24, adding, “RIP LinkedIn, DocuSign, MalwareBytes, Verizon, GitLab, Atlassian, Thomson Reuters, F5, Sonic Wall.”
“The next DLS (Data Leak Site) will contain the data of the Salesloft and GainSight campaigns, which is, in total, almost 1,000 organizations, ” the group told Dissent Doe, PhD. “From the GainSight campaign, the large companies were: Verizon, GitLab, F5, SonicWall, and others.”
ShinyHunters told BleepingComputer they accessed another 285 Salesforce instances following the Gainsight breach, using secrets stolen in the Salesloft Drift intrusion.
OAuth Tokens and the SaaS Ecosystem Attack Chain
This Salesforce data theft incident highlights significant SaaS security risks related to interconnected application ecosystems. Ferhat Dikbiyik, Chief Research and Intelligence Officer (CRIO) at Black Kite, shared with TechNadu that this exact pattern was observed in a previous campaign involving Salesloft Drift, in which Gainsight acknowledged exposure due to stolen tokens.
Dikbiyik highlighted that over-provisioned permissions for third-party applications create a significant attack surface, explaining that even if the core platform, such as Salesforce, remains secure, a compromise in any single connected application or vendor can trigger a cascading data breach.
The only way to stay ahead is visibility, context, and continuous monitoring, and organizations must:
- Audit every connected app.
- Rotate vendor OAuth tokens immediately.
- Re-validate every integration.
- Harden your approval process.
- Push vendors for transparency.
ShinyHunters retaliated with Salesforce extortion threats after the FBI seized BreachForums in October.
Responding to hacker claims, a DocuSign spokesperson reached out to us to share the following statement:
“We are aware of ShinyHunters’ claim. Following a comprehensive log analysis and internal investigation, we have no indication of a Docusign data compromise at this time. Out of an abundance of caution, we have taken a number of measures including terminating all Gainsight integrations and containing related data flows. We continue to actively monitor for any suspicious activity and are partnering closely with Salesforce should additional information become available.”
This story has been updated to include DocuSign’s statement.