SafePay Ransomware Emerges as Most Prolific Threat Actor of May 2025
- The ransomware landscape saw significant shifts in group leadership, emerging actors, and fresh operational tactics.
- Qilin was surpassed by the SafePay ransomware gang in May 2025, with Play, Akira, and NightSpire following.
- The latter leverages various RaaS affiliations, including Qilin and DragonForce.
In May 2025, SafePay ascended to be the most prolific ransomware group, overtaking previous frontrunners and reinforcing its status as a primary adversary. The group led the field with 58 claimed victims, surpassing former leader Qilin, followed by Play, Akira, and NightSpire.
SafePay has now accounted for 198 attacks since its emergence in late 2024, consistently leveraging double-extortion tactics, a recent Cyble report said.
SafePay typically breaches organizations via vulnerable VPN and RDP endpoints, using compromised credentials or password spraying, then exfiltrates sensitive data before deploying encryption.
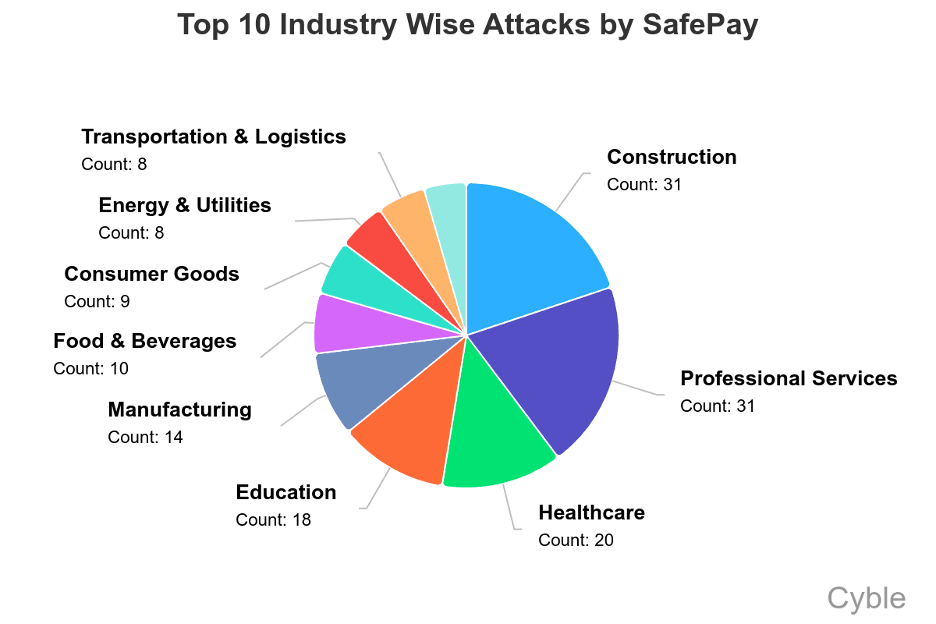
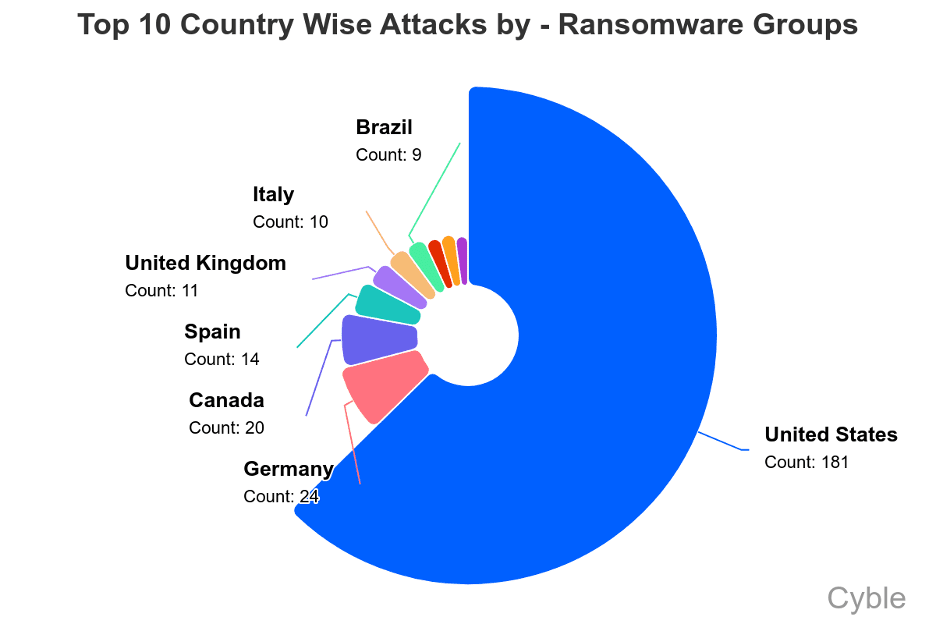
Unlike other groups, SafePay eschews a Ransomware-as-a-Service model, retaining direct control over its campaigns. Its primary targets have been in the United States and Germany, with an atypical focus on Healthcare and Education.
DevMan is another actor of concern, recently transitioning from an affiliate-focused model to independent operations.
Although responsible for only 13 incidents in May, DevMan’s custom encryptors and increased lateral movement speed pose a growing risk. The group leverages various RaaS affiliations, including Qilin and DragonForce.
May also saw the VanHelsing ransomware source code leaked freely on underground forums. This follows an attempted auction and subsequent internal fallout, raising the likelihood of opportunistic copycat operations, reminiscent of past incidents with LockBit and Babuk leaks.
Professional Services and Construction businesses were the most targeted sectors, together suffering over 100 attacks. The majority of victims were U.S.-based, with the country registering seven times the number of incidents seen in Germany, the second most-attacked nation.
Several new ransomware groups, such as Dire Wolf, DATACARRY, and “J,” established onion leak sites and claimed initial high-profile victims across Asia, Europe, and North America. High-impact attacks included those on U.S. emergency service providers, major technology firms, and supply chain operators.
Silent, Termite, Akira, and other established names also continued targeting critical infrastructure and manufacturing.