SafePay Ransomware Claims Attack That Disrupts Operations at IT Leader Ingram Micro
- Ingram Micro recently acknowledged a cyberattack that led to disruptions in the company's operations.
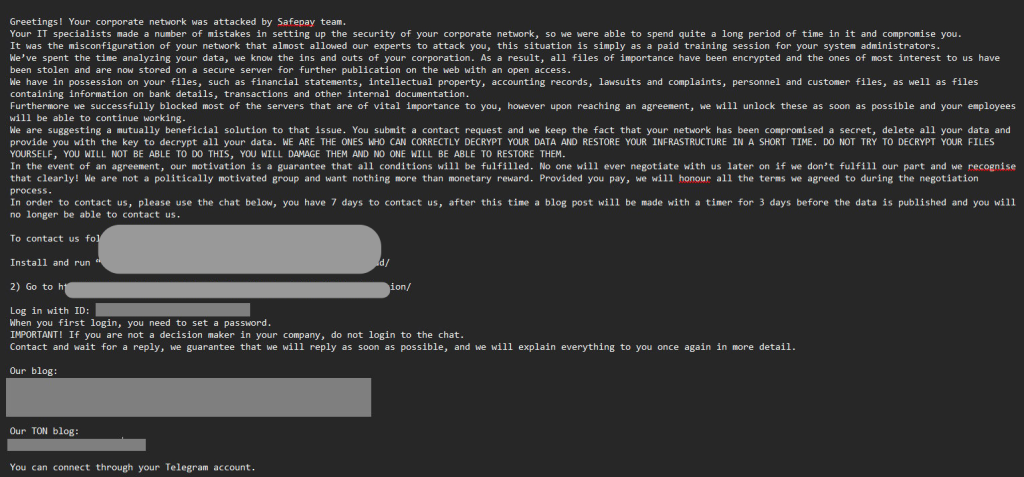
- Attackers revealed themselves to be part of the SafePay ransomware operation via a ransom note.
- They claim to have exfiltrated critical data, including financial records, intellectual property, and customer information.
Global IT distribution giant Ingram Micro has confirmed a ransomware attack that has significantly disrupted its operations, taking a substantial portion of its internal systems offline. The SafePay ransomware operation soon claimed the attack.
The attack, which began on July 3, paralyzed essential systems, including order processing platforms and critical services like the AI-powered Xvantage distribution and Impulse license provisioning platforms.
While communication tools such as Microsoft 365, Teams, and SharePoint remained operational, the incident resulted in widespread disruptions, preventing resellers and managed service providers from placing orders.
SafePay, a ransomware gang active since late 2024, claimed responsibility for the attack. The ransom note said the group exploited misconfigurations within Ingram Micro’s network, gaining extended access and compromising systems before encrypting files and issuing ransom demands.
Many of the company’s employees were directed to work from home to mitigate risks, as the compromised systems also included its GlobalProtect VPN infrastructure.
The attackers reportedly claim to have exfiltrated critical data, including financial records, intellectual property, personal and customer files, bank details, and more.
However, these ransom note claims are yet to be independently verified.
Following the discovery of the attack, Ingram Micro initiated incident response protocols, enlisting the support of cybersecurity experts to secure the affected systems and mitigate ongoing threats.
The company has also notified law enforcement while working to restore its operational capacity, apologizing to partners and customers for the resulting disruptions.
In May 2025, SafePay emerged as the most prolific ransomware group, surpassing former leader Qilin. The group led the field with 58 claimed victims.