Russian Group Coldriver (Callisto) Adapts with New Malware Strains for Cyberespionage After Exposure
- Rapid evolution: Coldriver developed and deployed three new malware strains within five days of its previous tool, LostKeys, being publicly exposed.
- New malware suite: The new tools are designed for stealthy information stealing from high-value targets.
- Aggressive operations: Google's Threat Analysis Group (TAG) reports that the new malware is being deployed more aggressively than in any previous Coldriver campaign.
The Russian state-sponsored hacking group known as Coldriver (formerly known as SEABORGIUM, also known as Star Blizzard, Callisto Group, TA446, TAG-53, and BlueCharlie), known for its persistent cyberespionage campaigns, has quickly pivoted its operations by developing and deploying a new suite of malware tools.
This rapid adaptation demonstrates the group's agility and commitment to maintaining its intelligence collection capabilities.
Technical Details of the New Russian Malware
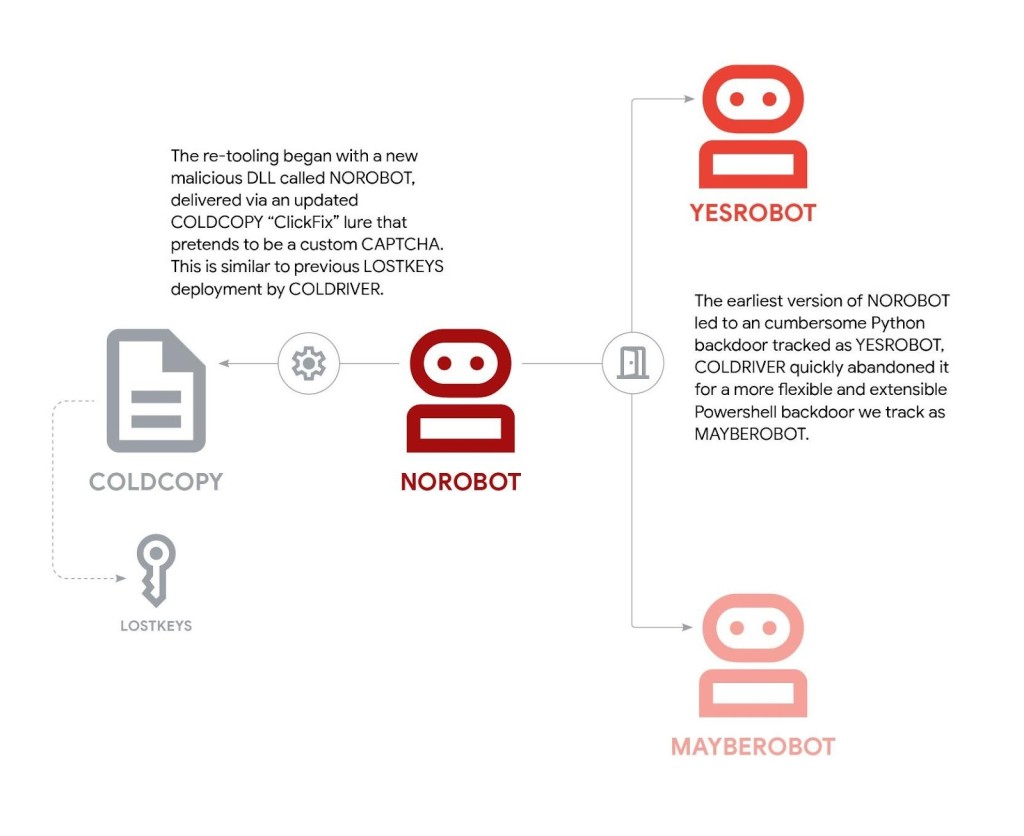
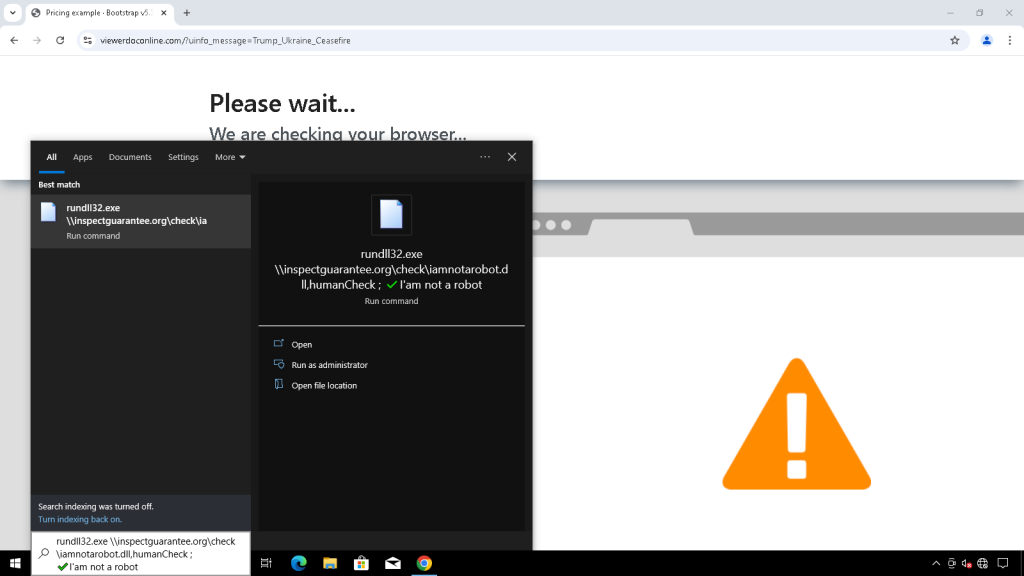
The group created three new malware strains just days after its LOSTKEYS backdoor was publicly disclosed by Google in May. The components are delivered via a new variant of the same COLDCOPY “ClickFix” lure, according to a recent report from Google Threat Intelligence Group (GTIG).
The new attack chain begins with a malicious file named NOROBOT, delivered through a fake CAPTCHA page—a tactic previously associated with the group.
This initial payload is responsible for installing a backdoor, which has evolved from an initial version called YESROBOT to a more advanced variant named MAYBEROBOT.
GTIG researchers note that while Coldriver continues to modify the initial NOROBOT delivery mechanism to evade detection, the MAYBEROBOT backdoor has remained stable. This suggests the threat actor is prioritizing stealthy entry while relying on a trusted, unchanged implant for post-compromise activities.
Implications for Cybersecurity and Espionage
Active since at least 2022, the Coldriver hackers are believed to operate under the direction of Russian intelligence services, primarily targeting human rights organizations, journalists, and civil society groups.
“It is currently not known why COLDRIVER chooses to deploy malware over the more traditional phishing they are known for, but it is clear that they have spent significant development effort to re-tool and deploy their malware to specific targets,” the report said.
While traditionally reliant on credential phishing, the group's increased use of custom malware indicates a strategic shift. The threat actor may be looking to infect already-compromised targets and exfiltrate additional intelligence directly from their devices.
The aggressive deployment of this new malware suite signals that Coldriver will likely continue its operations against high-value targets to fulfill its intelligence-gathering objectives.
In other recent news, a cyberespionage campaign targeting global organizations with custom APT implants was seen as recently as August 2025, and the British MI5 warned U.K. politicians of state-sponsored espionage threats from China, Russia, and Iran.