Romanian Police Arrested Two Malware Service Operators
- Two men in Romania were arrested for running malware crypting and AV scanning platforms.
- Their services were used extensively by underground hackers who were looking to raise the effectiveness of their malware.
- Crypters continue to play a pivotal role in malware campaigns and remain a headache for AV engineers.
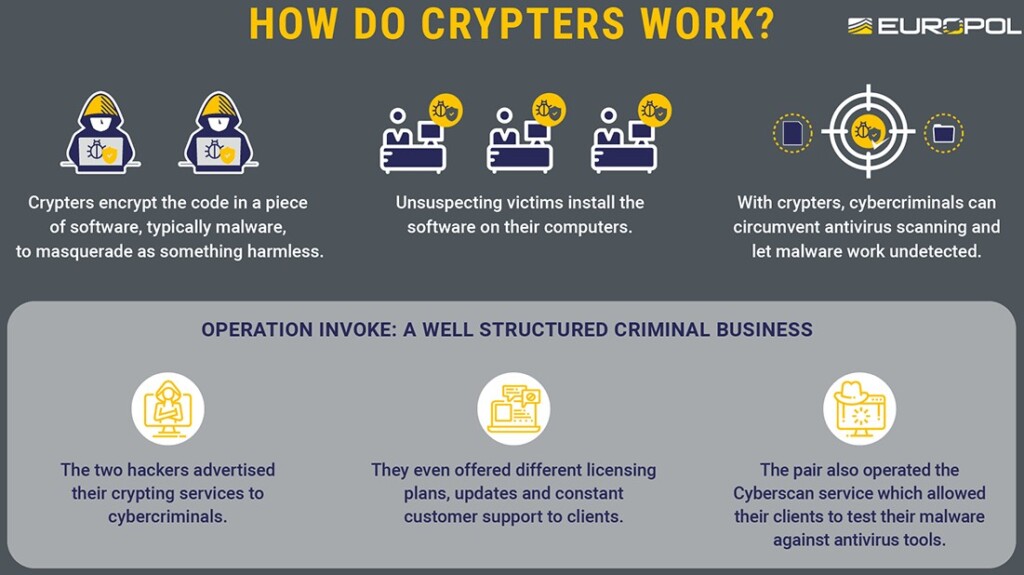
Two men based in Bucharest and Craiova, Romania, were arrested for allegedly running the ‘CyberSeal,’ ‘CyberScan,’ and ‘DataProtector’ crypting services. These services help malware authors wrap their payloads (trojans, info-stealers, ransomware) in an encryption shell, essentially evading detection from most AV tools.
Thus, they play a key role in the success of malware operations and also receive significant amounts of money raised via illicit means.
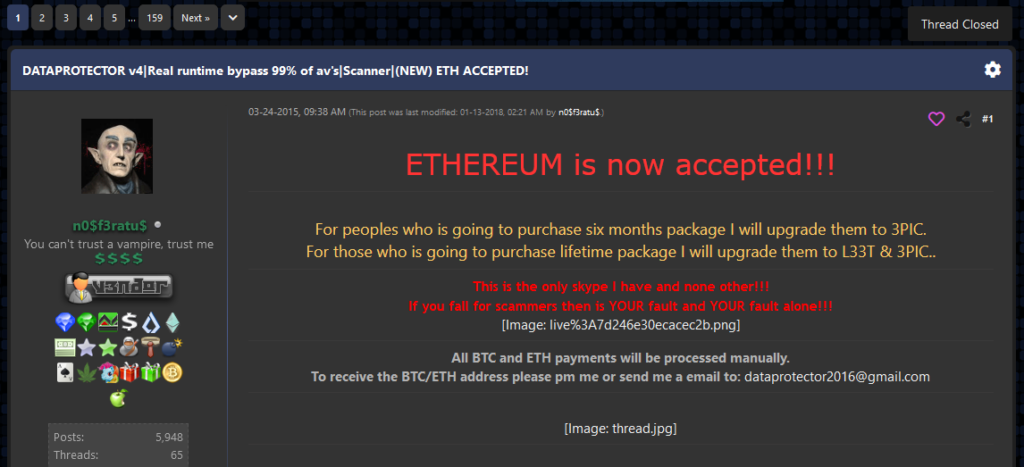
In the case of CyberSeal and DataProtector, it is estimated that the services were offered to 1,560 criminals who used a total of 3,000 malware strains. The prices for these services vary between $7 and $40 for testing samples against antivirus scanners, and between $40 and $300 for the actual crypting services. The difference in the price depends on the license conditions, as some clients bought ongoing support with updates and practical help.
The police raided four houses and uncovered backend infrastructure (servers) in Romania, Norway, and the United States. As a result, the ‘cyber-seal.org’ and the ‘cyberscan.org’ domains that used to host the two services are now offline.
The law enforcement agencies that worked together to successfully carry out this operation include Europol, Poliția Română, the FBI, the Australian Federal Police, and the Norwegian National Criminal Investigation Service. This goes to show how well-networked these two services were on the dark web, their popularity, efficacy, and extent of their operations.
ZDNet reports that the two suspects were active on the malware scene since at least 2014 when the CyberSeal was launched. DataProtector came online in 2015, and CyberScan was only set up last year. All three were aggressively advertised on a multitude of hacking forums, gradually building up a reputation.
As we analyzed back in December 2019, crypters are an indispensable part of malware operations today, and the space is very active in refreshing their methods to avoid detection. From AES256 to RC4, there’s a range of encryption algorithms used to make malware “stealthy”, while XORing, hexadecimal string transformation, non-ASCII character embedding, string rotation, and character order shifting are all helping achieve that goal.