Rhadamanthys Infostealer Infrastructure Disrupted in Apparent Law Enforcement Takedown
Key Takeaways
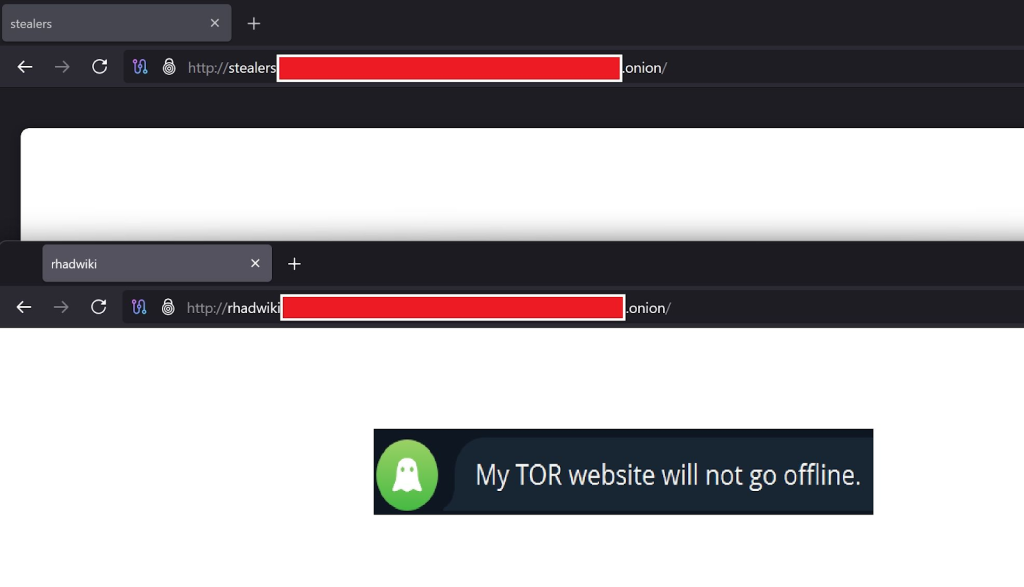
- Infrastructure offline: The infrastructure supporting the Rhadamanthys Infostealer, including its official TOR website, has been rendered inaccessible.
- Law enforcement: Internal communications among threat actors warn of EU police activity.
- Connections: The disruption is reportedly linked to a coordinated law enforcement crackdown on cybercrime.
The Rhadamanthys infostealer operation has suffered a significant blow, with its core infrastructure, including its TOR-based website, becoming unreachable. This disruption has triggered widespread concern among its user base, with internal communications revealing urgent warnings about a law enforcement operation.
Cybercrime Infrastructure Disruption
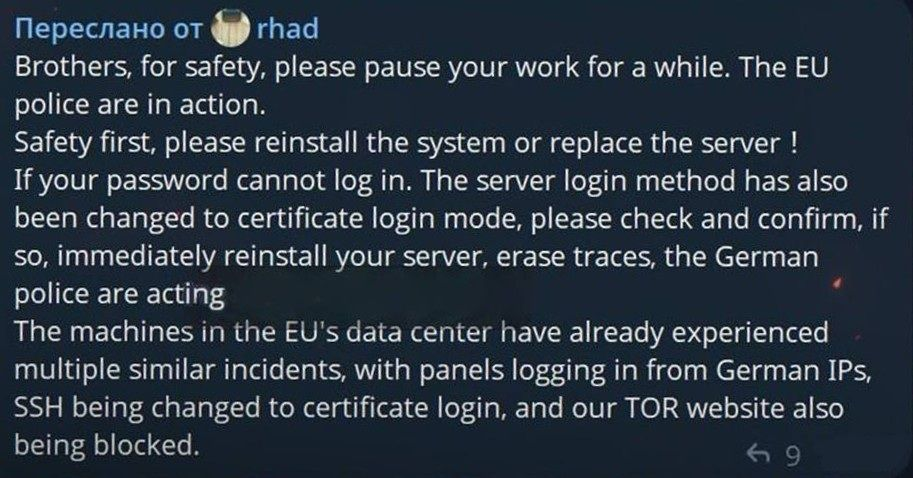
A message circulated among Rhadamanthys operators, attributed to a user named "rhad," advised an immediate cessation of activities, citing actions by EU police, according to Hudson Rock’s co-founder & CTO Alon Gal.
The alert detailed evidence of compromise, including server logins from German IPs and changes to SSH login methods, prompting calls to reinstall systems and erase traces.
The takedown appears to be part of a coordinated effort targeting major cybercrime services. The internal messages specifically note that multiple machines in EU data centers have been affected and that the group's TOR website has been blocked.
This level of cybercrime infrastructure disruption points to a sophisticated and well-executed campaign by international law enforcement agencies.
The panicked reaction from the malware’s affiliates underscores the effectiveness of the operation, which has seemingly dismantled key components of the Rhadamanthys infostealer network, leaving its operators unable to log in or manage their activities.
Potential Link to Operation Endgame
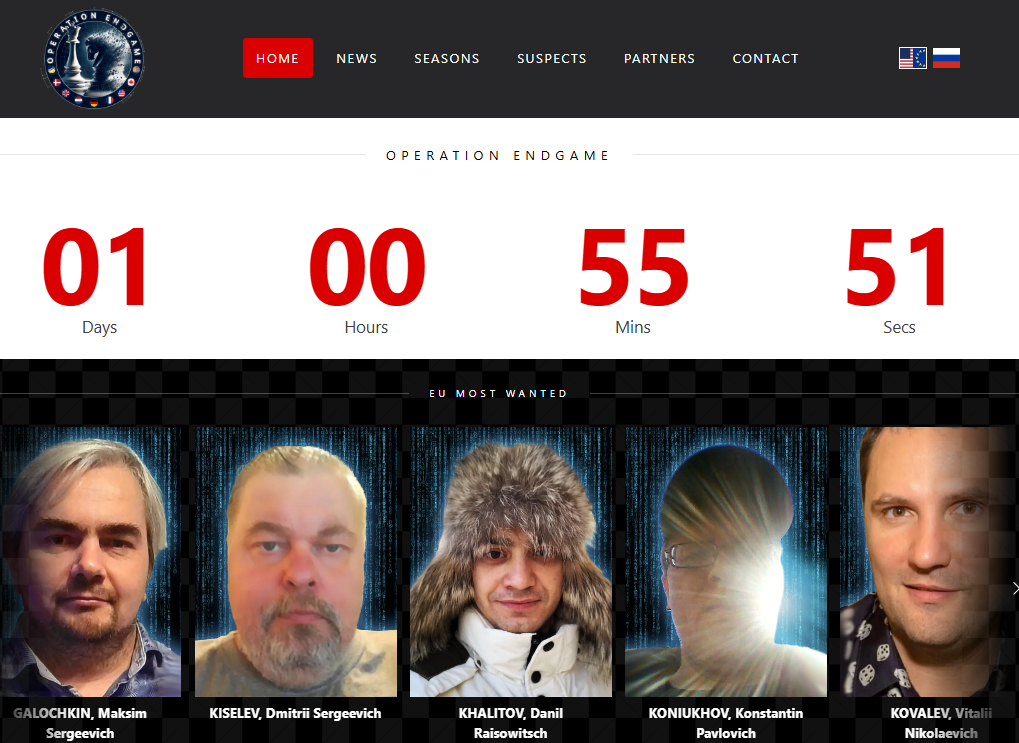
Evidence suggests the action against Rhadamanthys is connected to the ongoing Operation Endgame, a major international initiative targeting malware droppers and botnets.
An Operation Endgame update on its official website appears to coincide with the Rhadamanthys takedown, indicating this may be the latest phase of the global crackdown. We’ll update this story after the countdown ends.
This potential link situates the disruption within a broader strategic effort to dismantle the cybercrime ecosystem by targeting not just the malware itself but also the foundational infrastructure that supports its distribution and control.
The DanaBot malware recently resurfaced despite being dismantled via Operation Endgame about six months ago.
In August, a BlackSuit Ransomware takedown disabled nine domains and four servers, seizing $1 million, while Meduza Infostealer developers were arrested in a Russian authorities’ crackdown in October.