The Retefe Banking Trojan is Back Through a Document Converter
- The Retefe banking Trojan has returned, targeting German and Swiss victims again.
- The malicious software is propagated through an abused shareware document converter.
- On the macOS, the crooks are deploying a fake Adobe Cloud installer, signed by the developer.
Following a year of inactivity, the Retefe banking Trojan has been noticed in the wild again, and the new samples are refreshed and upgraded. The campaigns that are based on the new Retefe are targeting Swiss and German users who are running either Windows or macOS. This indicates that the hackers behind these campaigns are after hefty bank accounts and not just random people. A Proofpoint analysis of the most recent samples that were provided to them by malware researcher Jaromir Horejsi has unveiled the following key changes:
- Retefe is now using the stunnel proxy instead of Tor for its communication with the C&C server.
- The “sLoad” intermediate loader was replaced by “Smoke Loader” which is better at avoiding detection.
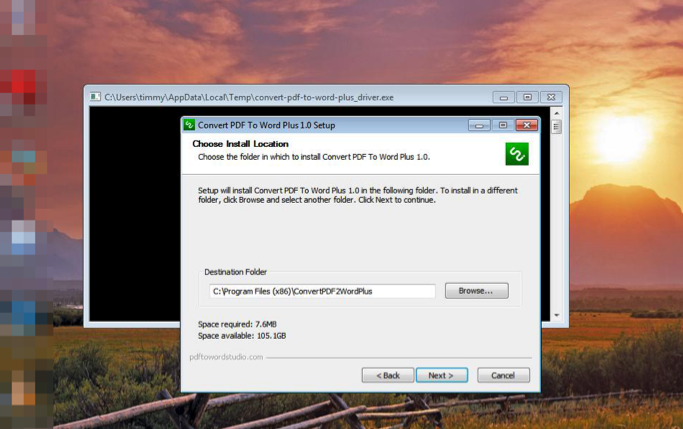
- The use of a shareware application named “Convert PDF to Word Plus 1.0”
image source: proofpoint.com
This document conversion tool is the new bait for Retefe, and considering the need that people have for turning a PDF document into a word one, it’s fairly easy for the malicious actors to reach out to a large number of victims. The shareware app is using a certificate signed by DigiCert, and it is practically a Python script packed as an executable. Upon its launch, the script writes and executes two files on the %TEMP% directory, with the one being the legitimate installer of the converter and the second being a decoy. The decoy is actually extracting 7-Zip and stunnel, and then decrypts and loads Retefe, the JavaScript banking Trojan.
image source: proofpoint.com
The researchers have noticed an alternative path of infection as well, involving the distribution of Smoke Loader which downloads Retefe after a couple of hours. The researchers estimate that the use of stunnel instead of Tor is done on the basis of avoiding detection. Tor allows the possibility of snooping on the hops between the nodes, so a victim on an enterprise environment could potentially detect and stop the communication.
image source: proofpoint.com
As for the macOS victims, Retefe reaches them mainly through fake Adobe Cloud product installers. The Gatekeeper security application is tricked by the fact that these malicious installers are using signed binaries by the actual developer. Those running macOS Mojave are safer thanks to additional integrity checks that are in place even for signed applications. For more details on how to handle controversial apps on macOS, check out Apple’s instructions page. For now, avoid “Convert PDF to Word Plus” and be careful with Adobe Cloud installers.
Have any comments to make on the above? Feel free to leave them in the dedicated section down below, or on our socials, on Facebook and Twitter.