Researchers Disclose Five Vulnerabilities in the WiFi WPA3 Standard
- The WPA3 standard is plagued by five vulnerabilities, four of which are quite severe.
- The flaws allow for accessing a protected WiFi network without knowing the password, or after having recovered it.
- The disclosure and PoC tools come after the patching by the WiFi Alliance and the impacted vendors.
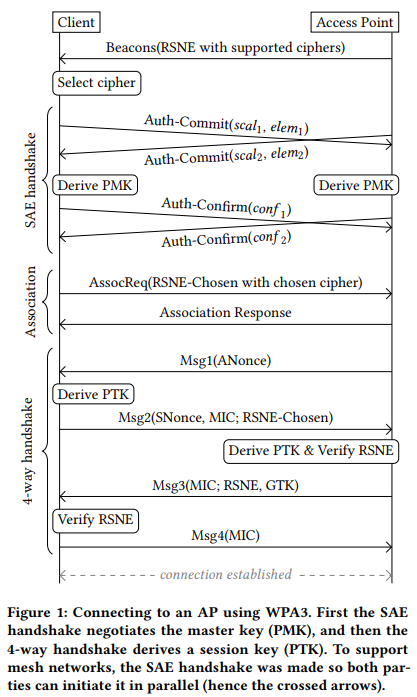
Back in October 2017, security researcher Mathy Vanhoef published the details of a fundamental vulnerability on WPA2 given the acronym “KRACK” (Key Reinstallation Attack). The vulnerability allowed an attacker to read encrypted WiFi traffic, steal sensitive data, and even inject malware into devices that were connected to the compromised network. As we were already more than a decade into using WPA2, the Wi-Fi Alliance announced WPA3 in January 2018, presenting the world with a more robust and secure standard. WPA3 uses stronger 128-bit encryption, replaced the pre-shared key exchange with “Simultaneous Authentication of Equals” (SAE), and makes even the use of weak passwords a less dangerous practice.
Over a year later, Mathy Vanhoef is back again and together with Eyal Ronen they disclose five vulnerabilities that concern the WPA3 standard, including a flaw allowing DoS attacks, two security holes allowing downgrade attacks, and two side-channel information leaks. Due to the fact that the report focuses on the weaknesses that concern the SAE “Dragonfly” handshake for key exchange, the paper is given the title “Dragonblood”. The Dragonfly handshake is supposed to be resistant to active, passive, and offline dictionary attacks, but the researchers have proven otherwise.
As detailed in the paper, when using a rogue AP that only supports WPA2, it is possible to take part in an obsolete 4-way handshake before the downgrade is detected, which gives the actor has enough information to conduct an offline dictionary attack. Another way to perform an offline dictionary attack is by figuring out the number of iterations used to encode the password of the user via a remote timing attack to the algorithm.
image source: papers.mathyvanhoef.com
The downgrade attack vulnerability concerns the possibility of jamming the messages of the Dragonfly handshake, and downgrading the client and AP to the P-256 curve, even if it was set to a P-521 curve (public key cryptography), potentially leading to password derivation.
image source: papers.mathyvanhoef.com
More technical details may be found in the paper published by the researchers, while tools that were developed to test the presented vulnerabilities are also available on a dedicated Dragonblood website. The researchers have already notified all affected vendors and coordinated with the Wi-Fi Alliance to plug the security holes before the deployment of the standard becomes widespread and much harder to patch. The WiFi Alliance has also announced a relevant security update on their website and clarified that they have no evidence that the presented vulnerabilities have been exploited.
What do you think about WiFi network safety in general, and have you had any adverse experiences with it in the past? Share your comments in the section below, and feel free to do the same on our socials, on Facebook and Twitter.